Breaking News: Major U.S. Pipeline Crippled in Ransomware Attack
The title there is important, because there are plenty of headlines that make it sound like the pipeline control systems were hacked, which is emphatically not the case. It was a ransomware attack against the IT network. (In industrial settings we talk about the IT network and the OT, or operational technology, network. There is a sort of semipermeable membrane between the two, and its permeability differs from one org to another. But generally the OT network is reasonably well isolated from the IT network. What it looks like here is that Colonial chose to shut down the operations out of an abundance of caution, and as a containment measure. There are still some questions as to what stands between the current state of things, and restarting operations. There are cases where things like not having accounting and billing systems online--things which live on the IT side of the house—cause the operation to be stuck, because some of them are designed such that when you can’t do the accounting, you don’t flow the gas through the line. I don’t know if that’s precisely the case here but that’s not unprecedented.
Coming up this week on Breaking Badness. Today we discuss: Peloton Has Hit a Pothole, Vulnerabilities Are Full of Missed-Steaks, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Peloton Has Hit a Pothole
- There certainly has been a chain of events that’s put the brakes on their momentum. But yeah, we stole the story headline from the first line of the article in ThreatPost by Lisa Vaas—”Peloton has hit a pothole.” This has all the makings of good drama. Death, Danger, and Data—spilled. Look for the made-for-TV movie about this in the next couple of months. Only question is which channel it will be on. Anyway. Long story short, they have been leaking rider data, they ignored a pentest result that they really should not have ignored, and there have been physical injuries and, as you said, at least one death. Fitness is great and all, but really staying alive and healthy needs to be part of any sensible regimen.
- Jan Masters of Pen Test Partners discovered that it’s possible to scrape user data from Peloton’s servers, regardless of whether it had been set by the user to “private.” This didn’t involve a lot of sophisticated hacking, because the issue was unauthenticated API endpoints exposed on the web. Peloton made a “sort-of” fix where only authenticated users could access these endpoints—but all that meant is that if I want to scrape other users’ private information, all I had to do is sign up with Peloton. So Houston, we still had a problem—but finally, when the pentester went to a journalist, in this case the security reporter Zach Whittaker, that finally woke Peloton up and they made a more proper fix. <liPeloton has between 1 and 3 million users, depending on whether you’re counting total users or total connected users. Even if it’s just the million-plus connected users, what was leaked was demographic info like username, gender, age, location, workout stats, and whether or not they were in the studio. Certainly enough to make a stalker or extortionist take notice.
- What doesn’t have built in cameras and mics these days? I could go on a long rant about privacy and the lameness of “smart” devices but I will try to restrain myself. But you might recall the episode right around the time of the inauguration when there was concern about putting Joe Biden’s Peloton bike in the white house—-and that was before this leak was disclosed publicly. When a company has a demonstrably poor security practice in one area, you certainly do wonder how they’re doing in other areas. You can bet that there’s going to be a lot of scrutiny, and well there should be.
- I have to say it seems like just laziness, to be honest. This wasn’t a case of a hack, and it really doesn’t even seem to have been some misconfiguration that a security-minded developer could accidentally overlook. It really seems as if someone made the decision that it was probably no big deal to have these endpoints exposed on the Internet. Maybe they were hoping for security by obscurity.
- To minimize the likelihood of a leaky API, do a little bit of threat modeling: ask yourself, do I have any API endpoints that I support? What data do they expose? Who needs to connect to them? How do I ensure that only authorized and authenticated users can connect to them? What would happen if an unauthorized user knew that these endpoints existed, and wanted to gain access? This isn’t hard.
- We know that they have lots of different motivations and that threat actors are creative. First off there’s the stalking/personal harassment risk when you have the level of detail about a user that they exposed. Then, we know that lots of people reuse usernames, so it’s not hard to imagine that for at least some accounts, this could help someone gain access to other accounts (though I will say that it does not look like passwords were available). But maybe most concerning is that this has basically said to malicious actors, “hey, here’s a company with a lot of interesting data and they don’t seem overly concerned about security.” So you can assume that there are actors out there looking for other ways to get access to more Peloton data even if these APIs have been locked down.
Vulnerabilities Are Full of Missed-Steaks
- Tesla’s support and will auto-connect to a generic ‘service wifi’ SSID. This was discovered back in 2017, by the way, and once there our researchers started looking for potential weak points within the ‘ConnMan’ (an open source generic network connection manager developed and released by Intel over a decade ago).
- Next up they started fuzzing ‘ConnMan’ and discovered a stack overflow bug in the DNS forwarder and a stack infoleak in the DHCP component (IT’S ALWAYS DNS!)
- They circumvented the DEP and ALSR by:
- DEP (Data Execution Prevention
- ALSR (address layout space randomization)
- Their DHCP fuzzing allowed them to overcome DEP and ALSR by identifying where they needed to be in memory and to give proper permissions for the next stage of their exploit to work.
- A hacker who exploits the vulnerabilities can perform any task that a regular user could from the infotainment system. That includes opening doors, changing seat positions, playing music, controlling the air conditioning, and modifying steering and acceleration modes. However, the researchers explained, “This attack does not yield drive control of the car though.”
Two Truths and a Lie
You'll have to tune in to find out!
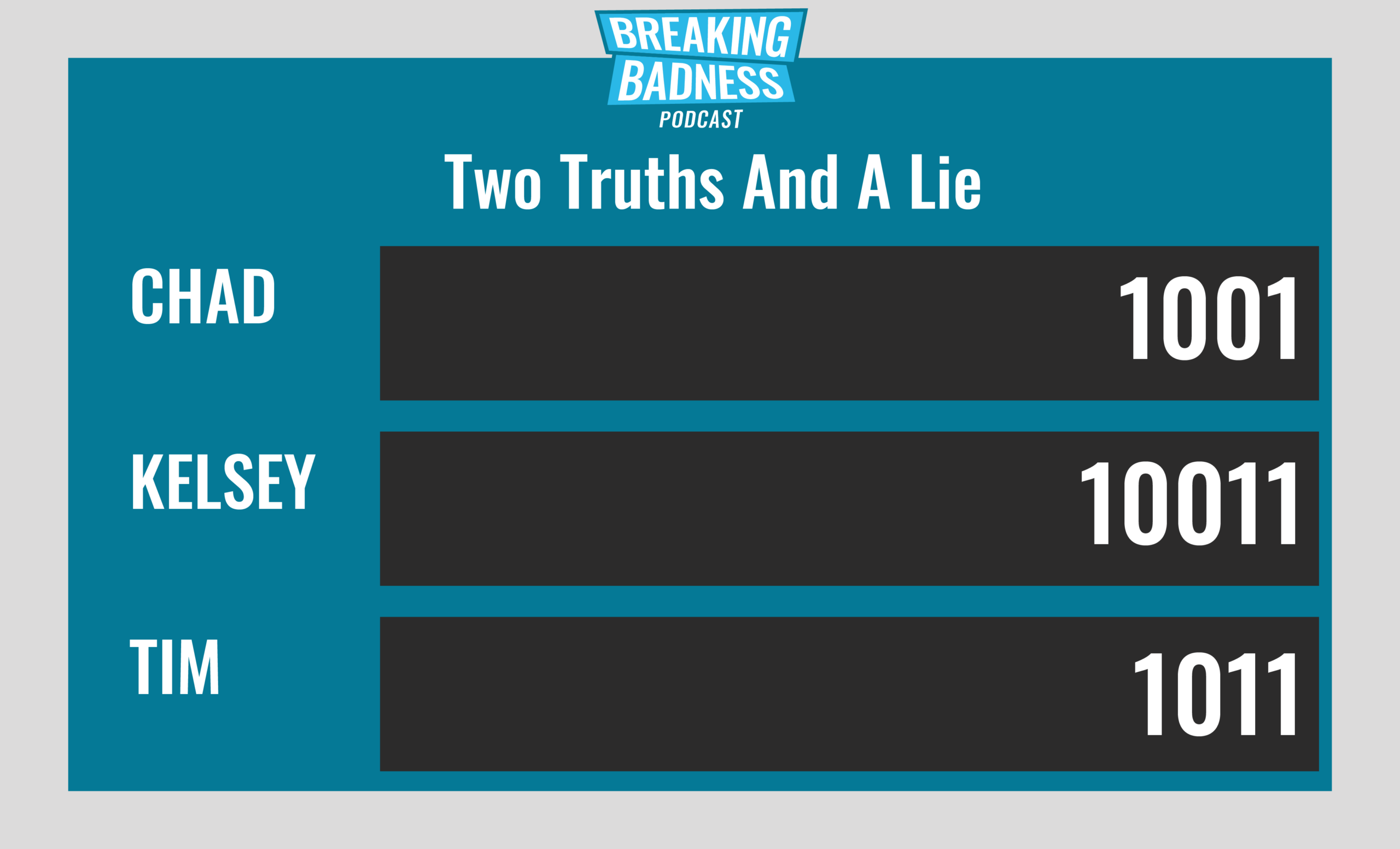
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Peloton Has Hit a Pothole[Taylor]: 3/10 Hoodies[Tim]: 3/10 Hoodies
Vulnerabilities Are Full of Missed-Steaks[Taylor]: 5/10 Hoodies[Tim]: 5/10 Hoodies
- That’s about all we have for this week, you can find us on Twitter
- @domaintools
- , all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
- *A special thanks to John Roderick for our incredible podcast music!

