Coming up this week on Breaking Badness. Today we discuss: Survival Horror, Ransomware, It’s in the Game, and our fun new game, two truths and a lie. Be sure to watch Forrest Brazeal’s original song, "the Ransomware Song".
Here are a few highlights from each article we discussed:
Survival Horror
- Back in 2020, CAPCOM announced that they had been subject to a customized ransomware attack on their systems following unauthorized access to their network. This leaked a lot of personal information from customers, sales reports, financial information, human resources, you name it. Along with that was quite a bit on former employees, shareholders, and corporate data. It was a lot of data. Later on it came out that this customized ransomware was RagnarLocker— a popular variant that makes up a decent percentage of the ransomware affiliate market. Not as big as say Conti or Egregor, but a few percentage points overall.
- In the end, CAPCOM refused to pay the ransomware so the RagnarLocker group dumped the data they had onto their leak sites. An artist is now suing CAPCOM because in their games they had suspected that their imagery from a resource CD had been illegally used in their games without paying the artist. This is a big deal as gaming companies—and software companies—are typically quite rock solid when it comes to fair use for these reasons. This could be a huge lawsuit with the artist claiming $12Ml in damages.
- They don’t say exactly how the artist became aware of the images in the dump. I would suspect they played the games and noticed the similarities. If you look at the images side-by-side it’s super obvious and I have no doubt they’ll win this case. The case details doesn’t say the dump was how they became aware, but they are using the breach data as evidence since it contains matching filenames and other details that make this an easy win. I just hope it gets accepted as evidence since I’m no lawyer, but it seems that leaked data may not be admissible in court? This is why I can’t give legal advice though.
- The MalwareBytes blog also highlighted some changes in the land of PR for ransomware groups. There is this transition of sorts to Robin Hood “extort from the rich and give to charities”. You’ll notice in some of the ransomware gang’s communiques and some of the chats that have been leaked by journalists that the people behind these have all sorts of personalities. Some honestly have tons of money now and are trying to shore up their image, some have political motivations, some are just curious hackers that have improved their socioeconomic situation. This move is one of a diverse tapestry of backgrounds for these ransomware affiliates. One of them catching a conscience is nothing new.
- MalwareBytes proposes that what we may see here is a trend, similar to the growth of double extortion, where ransomware authors look for compromising information in leaks and pre-sell that to legal firms. I could sort of see this happening, but that’s also a lot of additional work, right? Ransomware is a pretty low-hanging fruit game. They need to turn around and ransom the next network and not spend time reading every bit of data they grabbed. That’s why we see these leaks containing troves of garbage sometimes. They’d require a whole other team to do that kind of work and I don’t see that happening. Maybe they could partner with a shady law firm on the side.
- Hopefully corporations aren’t trying desperately to hide that they’ve been using people’s content illegally. In the case that you are an organization that’s doing something terrible like that then maybe you are willing to pay to keep your secrets, but I would hope at some point you’ll get what’s due to you if that’s in your standard business practice.
Ransomware, It’s in the Game
- Well, if anyone is listening to this and hasn’t heard of EA, that means that we must be doing something right in terms of expanding our reach, since I think everyone in infosec knows this company. It’s one of the biggest gaming outfits out there, with titles like FIFA, Battlefield, the Sims, and a whole lot of others. As an aside, this is the best way to enjoy championship-level soccer, or footy, without the corruption. Recommended. Anyway, it seems that the source code to a bunch of source code for games, as well as internal tooling, has been lifted from EA. This includes FIFA21, which is pretty huge, as well as the so-called matchmaking server that helps facilitate connected playing.
- When it comes to the value of source code to companies like EA, It’s relatively everything. In fact, there’s not much of a “relatively” to it. It’s one thing if, say, the blueprints for the next Tesla get stolen, because it’s not trivial to do the actual manufacturing of a Tesla. But source code for a game, on the other hand—that’s pretty much the whole kit and caboodle. That’s actually not really quite true either, since obviously the production of finished software involves a lot more than just having the source code. But it’s pretty fundamental to the business. And by the way, it was not just the source code to the games, though that makes it easy to illustrate what’s going on. They got a lot of internal sdks and other tooling, so that point I made a moment ago about how the source code isn’t everything—well, these attackers have gotten a lot more. It’s a rough week for EA any way you look at it.
- Malicious hackers are not known for humility. So in true malicious hacker form, these folks crowed about their conquest on some underground forums, and the folks at Motherboard saw the postings (indirectly, through a source). And EA confirmed it to Motherboard, so it’s for real. Naturally, the stolen goods are for sale.
- How they got in is kind of clever, in an F-U I hate your cleverness way. The entry point was Slack. The way they did it was by getting hold of stolen cookies, then using the access afforded by that to get into an internal employee slack channel. How they specifically did that was that they concocted a story of having lost their phone at a party, and social-engineered EA’s IT support staff to give them 2FA tokens so they could log in as the employee to the corporate network. And from there they did fairly standard lateral movement, pivot-and-escalate stuff, creating a VM that gave them better visibility into the developer network and the access they needed to download the source code and tooling.
- EA said that a limited amount of data was stolen, and while that’s true, you could also say that there’s a limited amount of sand in the Sahara. But what else can they say? When you’re doing crisis communications you want to help keep folks calm and to portray things in the least negative light while still being truthful. And there are some minor bright spots, such as that it appears that no personal player information was leaked.
- Everyone, absolutely everyone, is susceptible to social engineering. And, sadly, one of the ways in which social engineering can be the most successful is when it capitalizes on people’s impulse to help. So imagine you’re the IT support person, you get this call from the purported employee who lost their phone, and you empathize with them, and maybe you have some evidence that tends to support that they are who they claim to be, and, well, Bob’s your uncle. Now we don’t know a ton of detail about how the social engineering part went, in terms of the literal actual communication. We just know that, unfortunately, it worked.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
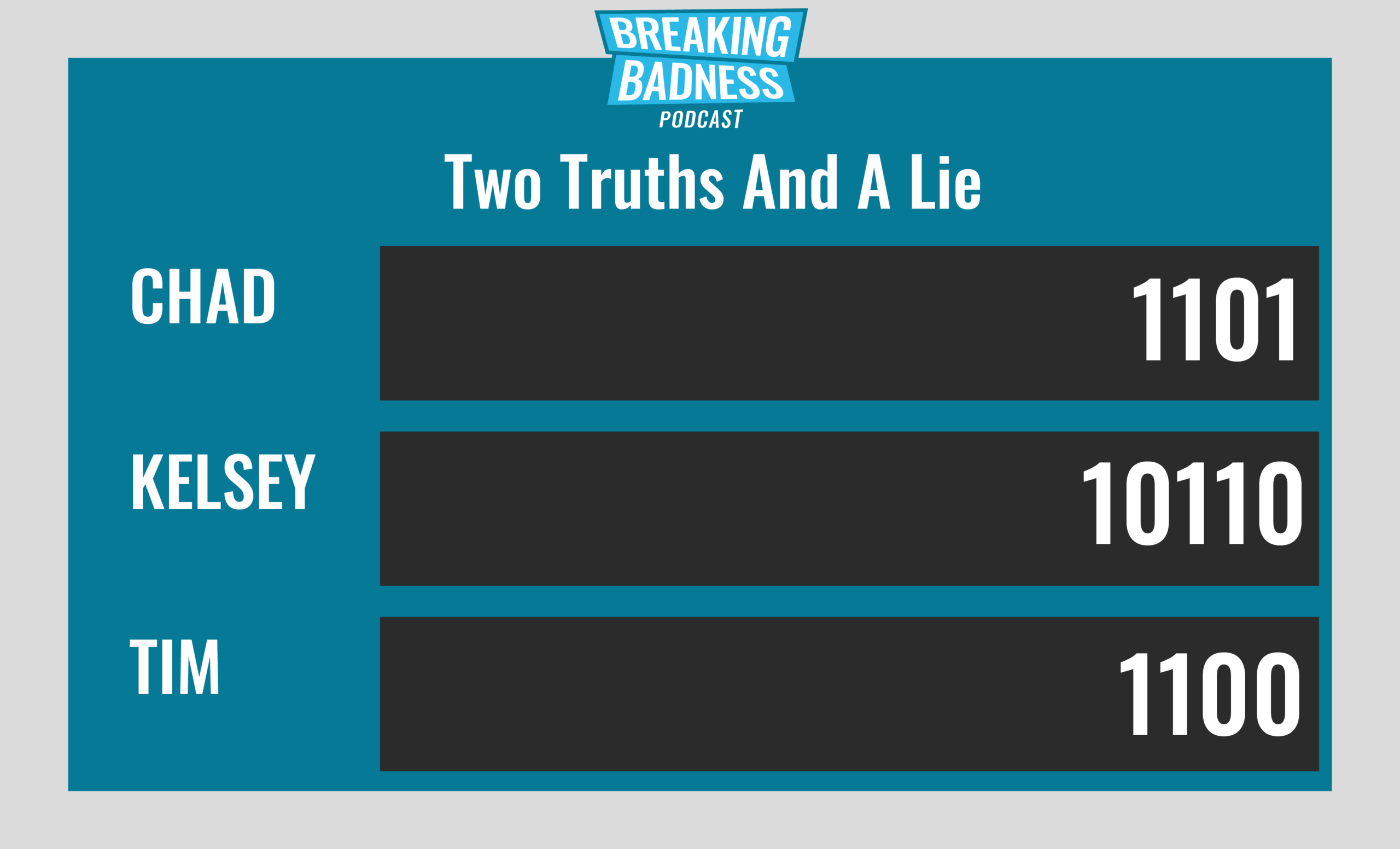
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Survival Horror[Chad]: 0/10 Hoodies[Tim]: 4/10 Hoodies
Ransomware, It’s in the Game[Chad]: 5/10 Hoodies[Tim]: 5/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

