Coming up this week on Breaking Badness. Today we discuss: ZOMG! Microsoft Azures Lots Of Mischief Ahead, Buckle Up! The Captain Has Turned On The Data Theft Sign, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
ZOMG! Microsoft Azures Lots Of Mischief Ahead
- First thing to know is you can run Linux on Azure (because basically most of the planet runs on Linux).
- OMI (Open Management Infrastructure) is Microsoft’s Azure management interface that allows for WMI-like (you guessed it: Windows Management Infrastructure) functions on Linux. OMI’s abstraction makes it super easy to manage Linux boxes on Azure. This OMI is automatically installed on every single machine.
- Where things went sideways is that extensions for OMI are vulnerable to privilege escalation of the simplest order. OMI runs as root with no privilege restrictions. The researchers at wiz.io discovered that if you remove the Auth header when interacting with OMI, it will let you run anything as root.
- A realistic scenario where this would be exploited though would be where a low-privilege user finds a way to pass some unsanitized input to run on the machine, and from there they can simply call the OMI to get root. This could be any number of ways and there’s probably a few dozen vulnerabilities out there that would allow someone to do this.
- Unfortunately, a further problem is that some management interfaces are exposed to the Internet, leading to an RCE (remote code execution) situation, which we are seeing actively exploited now by botnets and cryptominers.
- Microsoft deployed an initial patch that was a failure, but they’ve now got that fixed. On September 22 they’ll be forcing an update to all of the OMIs with the proper patch.
Buckle Up! The Captain Has Turned On The Data Theft Sign.
- Airlines (as opposed to other parts of the extensive aviation sector) account for some 61% of cyberattack victimology in aviation. This particular attack has been in flight for at least two years now.
- Cisco Talos linked some recent aviation targeting campaigns to a specific actor who has been running successful malware campaigns across the board for more than 5 years.
- Ransomware gangs and other cybercriminals are increasingly buying their way into corporate networks. You can think of it as outsourcing for the initial compromise which comes in the way of previously installed backdoors on specific targets. In this case, IABs (initial access brokers) are selling access into victim networks.
- This particular threat actor is not a 1337 h4x0r per se; they used off-the-shelf CyberGate malware without further modifications, and some samples appear to show that CyberGate has been replaced with AsyncRAT. It’s also thought that this was combined with “off-the-shelf”crypters that allow the usage of the malware and still go undetected.
- The attack begins with a targeted phishing email that contains an attached pdf file which was linked to a .vbs file hosted on Google Drive. Once the PDF is downloaded and opened, the final Remote Access Trojan is encrypted and is dropped into the victim’s computer. The attack can potentially translate to spying of victims and their behavior, exfiltration of data such as credentials, screenshots, clipboards and webcam data.
- A few domains have been uncovered by Talos during the investigation, such as akconsult[.]linkpc[.]net which was being used as a command and control server for the aviation campaign, hosting the AsyncRAT payload. Because the server was using TLS to encrypt the C2 traffic the researchers used the same certificate fingerprint and found 8 more subdomains linked to the campaign as well as 50 malware samples.
- Analysis of the activity associated with the domain reveals that this actor has used several RATs and that, since August 2018, there are samples communicating with this domain with names that indicate the adversary wanted to target the aviation industry.
- To help protect against these activities, Defenders can identify network traffic from or to the highlighted infrastructure and clean up any system that had traffic associated with IOCs.
- As always, it’s also critical for users, specifically employees from the industry, to be alert to suspicious emails messages and avoid downloading or running malicious attachments in these messages!
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
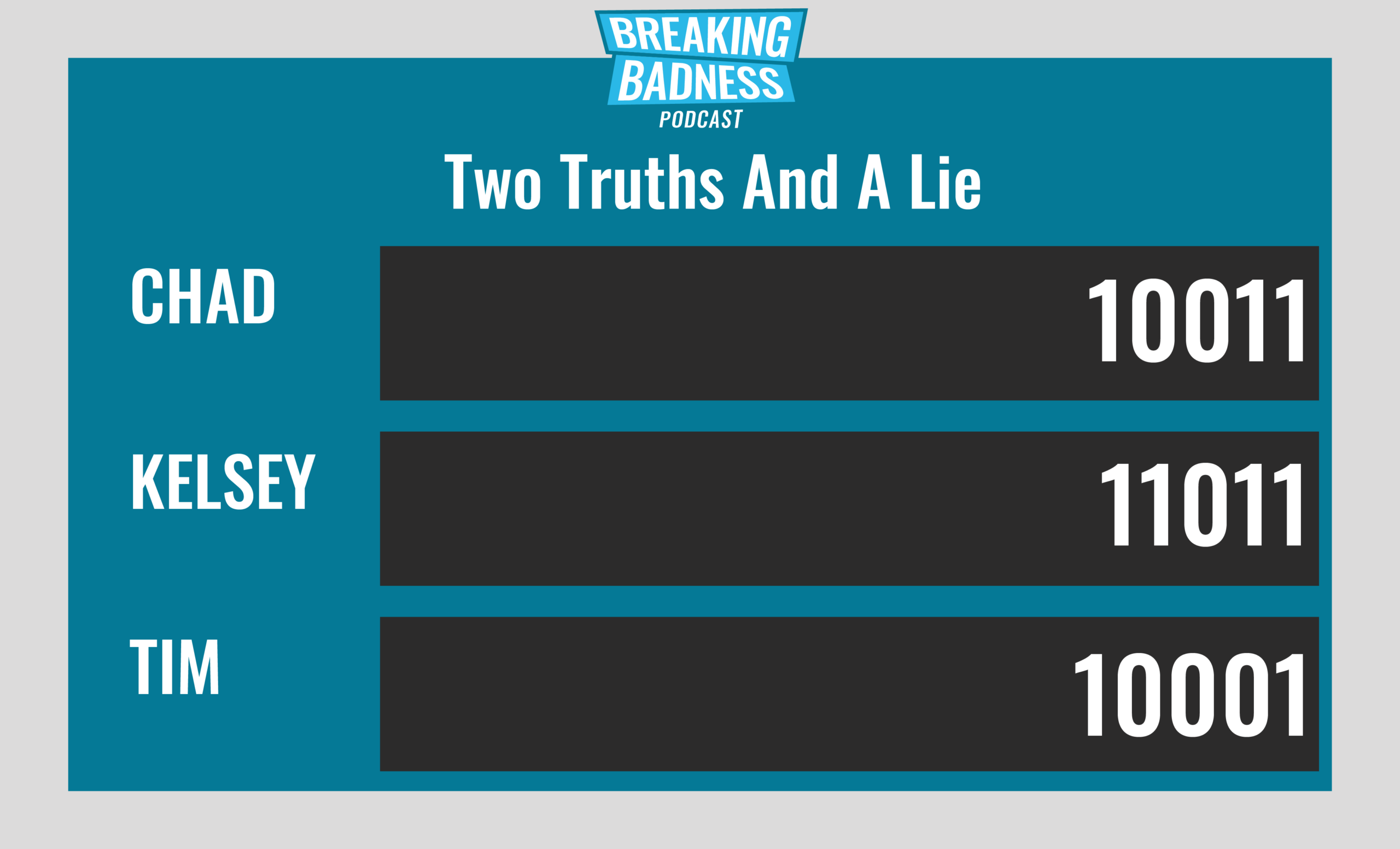
Current Scoreboard
This Week’s Hoodie/Goodie Scale
ZOMG! Microsoft Azures Lots Of Mischief Ahead[Chad]: 8/10 Hoodies[Dan]: 8/10 Hoodies
Buckle Up! The Captain Has Turned On The Data Theft Sign.[Chad]: 7/10 Hoodies[Dan]: 8/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

