Coming up this week on Breaking Badness. Today we discuss: An Arrest With No Rhyme or Treason?, Microsoft Excels at Mitigating Risk, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
An Arrest With No Rhyme or Treason?
- Group IB is a threat intelligence company that provides finished, actionable intelligence to their customers. They also have some products like a hunting framework and also do some risk management pieces. Basically they’re one of those security services firms. They came onto the scene around 2003, started by two Russian nationals Dmitry Volkov and Ilya Sachkov though technically the company is headquartered in Singapore. They moved there after their founding in Russia because they wanted to be more agile as a company and not have to operate under some Russian restrictions. Their business at this point spans parts of Europe, Vietnam, South Africa, Malaysia, you name it. They’re a decent sized international firm with over 500 employees.
- Ilya Sachkov though was arrested, it looks like by someone in a white van ironically, as Russian media showed one at the front of their Moscow offices carrying various things from the building during a round of searches the state did at Group IB’s Moscow and St. Petersburg offices.
- Group IB stated that their lawyers are looking into it, but weren’t going to comment on the charges right now. They’ve also assured customers that their data is safe due to the globally distributed infrastructure they have.
- Looking at the penal code in Russia, high treason means up to 20 years in prison, but with how tough Russian prisons are I don’t think most people make it to serve their full term. Hoping that this is just a scare tactic from Putin and that Group IB can dissolve their Russian offices and move elsewhere. Perhaps it’s time for Ilya Sachkov to apply for citizenship somewhere else. Kind of surprised they hadn’t yet given what we know of Putin and Russia’s general interactions with corporations in the Federation.
- The Russian state is charging them with treason for providing intelligence to foreign agencies. With how global they are this makes absolute sense that they would. It’s their business. They investigate cyber threats and publish actionable intelligence for their customers. This would be like the NSA picking me up for looking into Equation Group infrastructure and publishing on it which I definitely have done. Everything is so connected in the cybersecurity world. Tooling at these points are shared -- I mean everything is Cobalt Strike at some point. If you’re doing any kind of investigation into state sponsored activities you’re probably going to write a report on some Russian infrastructure at some point. It will be interesting to see what the evidence says, but I’m guessing the evidence presented will show standard reporting on the Dukes.
- Russian media has said that FSB, the Federal Security Service, one of Russia’s intelligence agencies was trying to force some cooperation from Group IB and that Ilya Sachkov refused as CEO. This, coupled with the CEO’s remarks in 2019 about wanting to be a global firm out from under Russian influence paints an interesting picture. Putin doesn’t like people mugging him off so these charges might just be revenge for not cooperating.
Microsoft Excels at Mitigating Risk
- It’s been a rough year for Exchange servers and the humans that love and care for them, with a couple of nasty vulnerabilities and feeding-frenzy exploits of them. Some listeners will recall ProxyLogon, back in the spring, and ProxyShell, this past summer. (Is summer already past? sigh.) Both were pre-auth, RCE vulns, and as you’d expect, a whole who’s-who of state-sponsored groups went to town on them.
- So this service, which is called the Emergency Mitigation service, basically runs as a Windows service on an on-prem Exchange server that has the Mailbox role (which in a lot of cases is basically the whole installation - the other role called Edge Transport is not used in all environments). What it does is detect when the server is vulnerable, and apply some mitigations, which Microsoft takes pains to say (in the manner of those sped-up medical disclaimers in all the ads) are NOT a substitute for actual patches, buth which help protect the server until said patches are available.
- There are three mitigations that they’re talking about right now:
- The first is an IIS URL Rewrite rule mitigation. It blocks specific patterns of malicious HTTP requests that can endanger an Exchange server.
- Next up is Exchange service mitigation, which disables a vulnerable service on an Exchange server.
- And then you got your App Pool mitigation. This disables a vulnerable—wait for it—app pool on an Exchange server.
- It’s pretty obvious (and appropriate) that this service is going to check for further mitigations as Microsoft develops them. And in a way this is part of a bigger protective initiative that started back in the spring with the Exchange On-premises Mitigation Tool, or EOMT. The name of that one is pretty self-explanatory. These are reasonable developments.
- Fortunately there is a way to disable EM - but don’t take that the wrong way, I think this service looks valuable and it’s probably a good idea to leave it enabled in most cases. But I also think it’s important to give folks choices in these matters, because there could be cases where the cure is, if not worse than the disease, at least something that someone might not want to live with. So for example, lots of shops will have an SMTP filter of some kind upstream of the Exchange server (this is the Barracudas and Zscalers and Check Points and Proof Points and whatever other Points that sit out there at the edge and scrub incoming connections of various kinds of nastiness - and those products often get rules to deal with various vulns and exploits pretty quickly. If you have such a system and you also would experience some pain from certain features being disabled by this EM service, then you might decide to disable it.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
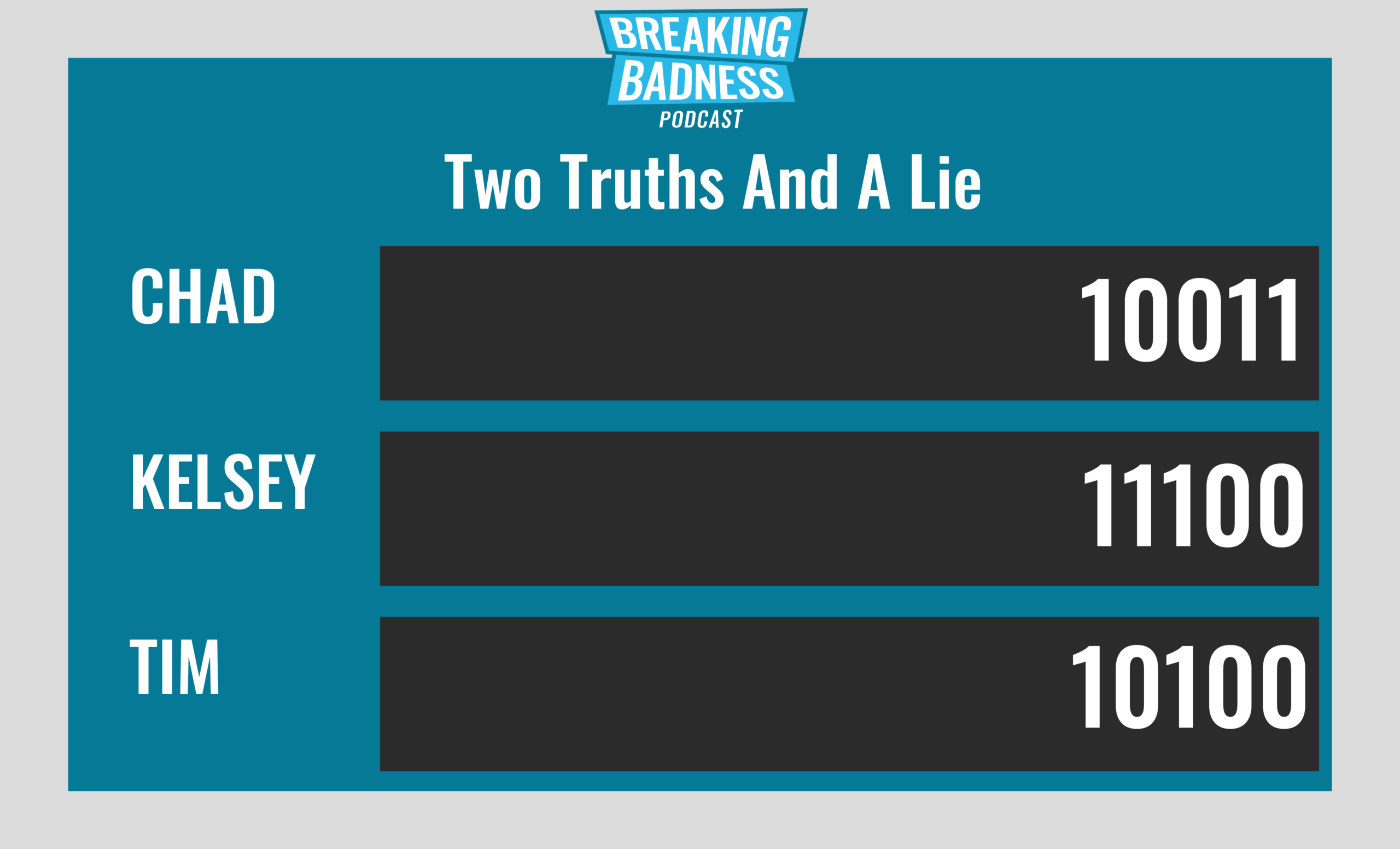
Current Scoreboard
This Week’s Hoodie/Goodie Scale
An Arrest With No Rhyme or Treason?[Chad]: 9/10 Hoodies[Tim]: 9/10 Hoodies
Microsoft Excels at Mitigating Risk[Chad]: 10/10 Goodies[Tim]: 9/10 Goodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!


