DomainTools Iris Investigate- Part 2
Part II: Example (Fictitious) Investigation Sequence
To illustrate the concepts and components of Iris Investigate, we will step through an imaginary investigation sequence, using fake domains and addresses. While the entities described are fictitious, the principles, including how inferences of connection, intent/nature, and identity are made, are exactly those used in real investigations every day.
Note: as of this writing, these domains, as well as “Bob Smith’s” email address, are imaginary, so a real search will not show them. This section is meant to be read through rather than performed online.
Scenario: The domain “acmegrommets.co” has been observed in nefarious activity, seeming to spoof the legitimate domain “acmegrommets.com.” However, details about who owns the domain are hard to come by. There’s no “About Us” page on their site, and the domain was registered using a privacy service, which frustrates efforts to use Whois as the source of information. It’s also hard to know whether it is a one-off “lone wolf” risky domain, or part of a larger network. In any event, since the domain and its controlling entity seem bent on doing harm, it is important to gain information quickly in order to minimize the harm.
Objectives: As the investigator tasked with assessing the risk posed by this domain, and potentially taking action against it, you hope to meet several objectives by using Iris Investigate:
- Learn who owns/controls acmegrommets.co. If you can’t positively ID the owner, then the next best thing is to come up with as detailed a profile as possible.
- Expose additional domains connected to acmegrommets.co. This objective actually serves several purposes:
- it may help expose a larger criminal network (if one exists)
- if there is a network of connected domains, seeing them may yield insights into the nature of the operation (does it focus on grommets per se? Does it impersonate legitimate outfits? Does it dabble in other enterprises, such as aglets or clevises?)
- one or more of the related domains may have ownership information that is elusive on the original target domain, acmegrommets.co.
- Document the connections between acmegrommets.co and its owners, related domains, infrastructure, and any other data that may serve your needs.
Overview
Creating an Investigation
Because you have the objective of learning as much as possible about acmegrommets.co, you click “New Investigation” after logging into Iris Investigate. You can name the investigation and, if you wish, supply a description.
Initial Search
You begin your investigation by entering acmegrommets.co in the search box (again, please note that this is not a real domain, so typing this into Iris Investigate would not actually return results). After doing so, you notice several things:
- Because the term you entered is a valid domain name, and the domain exists, Iris Investigate returns a record containing information DomainTools has about acmegrommets.co.
- The domain was registered with a popular privacy service, so there are no useful contact details in the current Whois record.
- By looking at the Domain Profile Data Panel, you can observe that 10 other domains are hosted on the same IP address as acmegrommets.co.
- Several thousand other domains are served by the same name server as acmegrommets.co.
Given this information, a good path for continuing your investigation is to “pivot” on the IP address and see what the other 10 domains are. This is a good path because:
- Whois privacy prevents identification and also prevents connecting this domain (via registrant contact information) to other domains
- The name servers won’t be useful for linking the domain to others, since there are so many domains served by them
- The IP has a fairly low population of domains. This means that it is easy to review the domains, and it could suggest a link between them. (By itself, shared hosting is no guarantee that domains are related. But with other corroborating evidence, it can support such an inference, especially when the number of domains on the IP is relatively low).
To see the other domains on the IP address, you right-click the IP address, which brings up an Operations Menu. From the Operations Menu, choose “Expand Search” to perform a pivot.
NOTE: Although in this example we found this information in Domain Profile, this IP address would also be highlighted as a Guided Pivot because of the low number of domains involved. You could have opened the Pivot Preview in order to see the list of the domains and their Domain Risk Scores.
Iris Investigate now displays all of the domains hosted on that IP address. Among the domains, you see the following:
- amalgamatedgromet.com
- nationalgrommetts.com
- superag1et.info
- federa1c1evis.com
- be11crankworld.com
- etc…
This list of domains makes the IP address look very interesting! There is a clear thematic connection among these domains. The names show a focus on certain manufactured items, and the misspellings and numeral/letter substitutions suggest that these domains are being used in phishing campaigns, with the owners hoping to lure victims into clicking links that look like they go to legitimate businesses.
Since the IP address now has your attention, you click the IP Profile Data Panel. Here you see several key pieces of information about the address: its country (Liechtenstein), the name of the IP range’s owner (“Otto’s Discount Web Hosting”), and the actual CIDR range of all addresses allocated to this provider. The country is interesting: while there is nothing wrong with hosting web sites in Liechtenstein, it is not necessarily the most logical place for American firms to host their sites (and these imagined grommet/aglet/clevis outfits are all American). A search engine lookup of the hosting provider may turn up interesting details about it, such as whether or not it has earned a reputation as a so-called “bulletproof” hoster.
You can supplement this information by looking up the same IP address in the pDNS Data Panel. Passive DNS resolution data often shows additional domains that are currently, or have been, hosted on the IP address. Sure enough, in addition to the eleven you already found, pDNS shows three additional domains that could be related:
- Spragc1utches-online[.]com
- Charnpionspline[.]com
- federaldogclutch[.]co
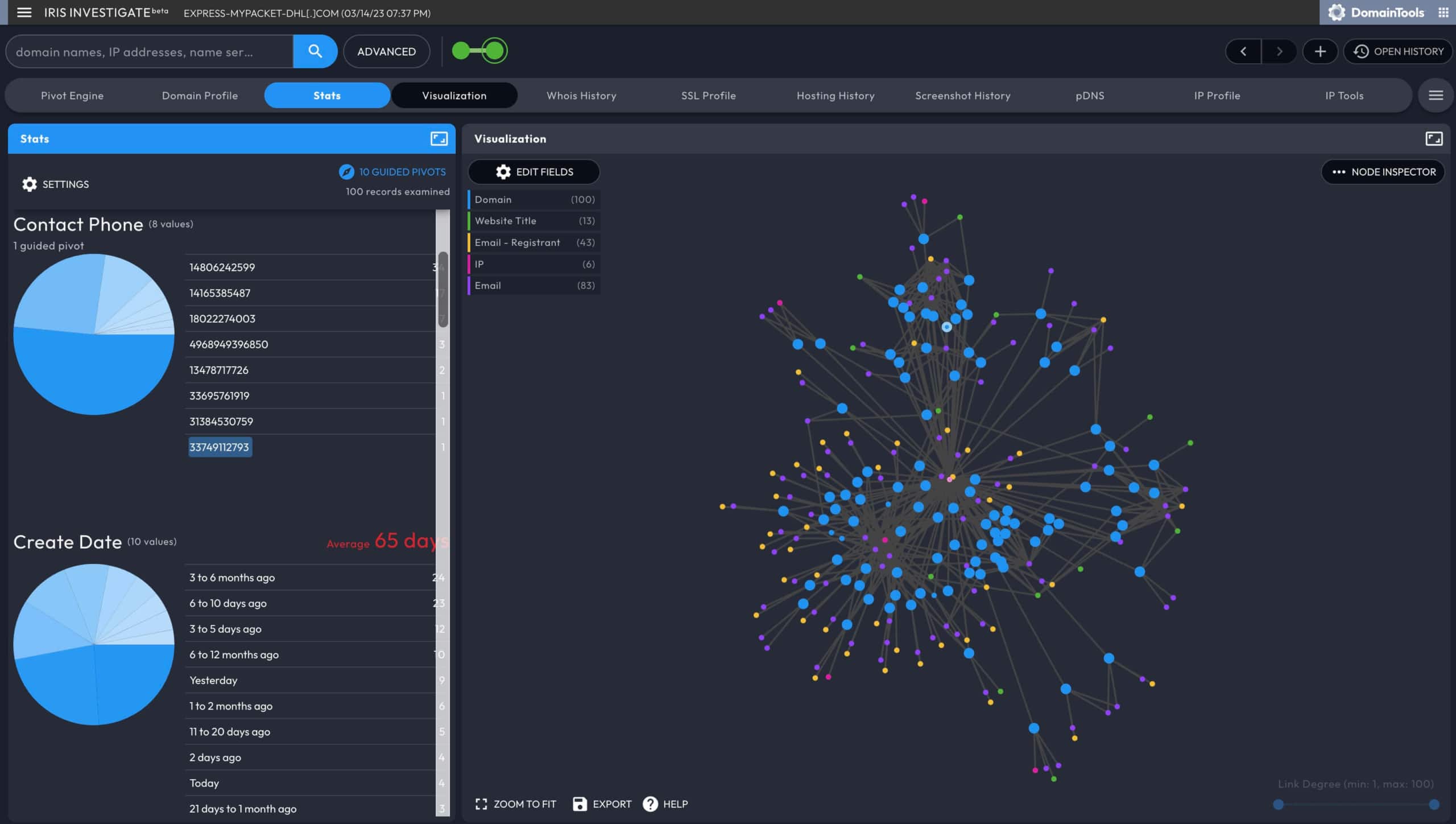
Iris Investigate helps you spot other possible connections. In the case of these domains, while it looks increasingly likely that there is a link among the eleven that are hosted on the IP address, it would be valuable to see if there are other connections among them. You can use the Visualization Data Panel to spot such connections.
In the Visualization Data Panel, you notice the following:
- Six of the 11 domains were created on the same date
- 8 of the 11 (including the six created on the same date) were registered with the same registrar
- All 11 have a shared phone number (which happens to be nonsensical, as it is all 1’s).
This information has now built a strong case that these domains are connected:
- Thematic similarity in names and in name schemes (i.e. numeral substitution)
- A lot were created on the same date
- All share a (bogus) phone number
- All are hosted on the same IP address
It is now extremely unlikely that the shared hosting is coincidental. As the investigator, you begin to feel confident that you have exposed a segment of criminal infrastructure that extends beyond the original domain, and you have also found strong indicators of the intent (targeting grommet etc. consumers) and techniques (likely phishing) of the controlling entity.
However, you still have no idea who the actual criminals are. The next part of the investigation will help you find possible leads on the identity of the operator(s) of the domains. The connections between the domains are important to this part of the investigation, because if you are able to find identity information on one of the domains, there’s a much greater chance that you have found an identity for all of them.
Eight of the 11 domains are registered with Whois privacy. Of the remaining three, one was registered by “Donald Duck” and the other two by “Darth Radar.” The administrative, technical, and billing email addresses are all useless, because they are either privacy service emails, or pseudo-anonymous addresses from free email providers. However, you do notice something interesting: there is a fourth category of email address shown by Iris Investigate—the DNS/SOA record. In some cases, these addresses can provide identifying information. You’re in luck: the DNS/SOA record for federa1c1evis.com seems to correspond to a person whose name is not obviously fictitious (let’s call him “Bob Smith”).
The email address [email protected] only shows up in one of the 11 domains on the shared IP. However, you have other options to find connections.
Starting with your original target domain, acmegrommets.co, you now click the Whois History Data Panel. The current Whois record, shown by default, shows the privacy-protected identity. However, you can explore the timeline of previous records to see if any other email addresses were recorded earlier. A convenient way to do this is to use the Next or Previous buttons. In this case, working backward from the present, you click Previous, scanning for different email addresses.
Good news: in a record from three years ago, you find [email protected]. Now, although you know that “Bob” owned the domain at one time, do you know whether the domain was malicious at that time? What if “Bob” sold it to someone else who is the actual bad actor?
A good way to establish continuity of ownership is to compare historical screenshots. You click the Screenshot History Data Panel and navigate back in time (using the Previous button) to before and after the bob.smith email address changed over to the privacy email. In this case, the screenshots did not change. This gives you a very strong indication that when the domain went into private registration, it didn’t actually change hands, and that it was likely malicious going back at least three years.
You can repeat this exercise for other domains on your list of 11. Even if you don’t find [email protected] in historical records of the others, you have established a strong enough link among these domains that it may be worth digging deeper on “Bob,” as you have strong circumstantial evidence that this individual is responsible for malicious activity.
If you wish, you can also expand your search of current records: on the DNS/SOA record for federa1c1evis.com, you right-click [email protected], which brings up an Operations Menu, and you click Expand Search. This pivot shows you five additional domains that were registered with that name, including ace1ugnut.com and acmegromets.com (note the misspelling of “grommet”). These other domains follow the thematic logic, and since email addresses are unique, there’s a strong likelihood of connection, even though they’re not on the same IP address as the original 11. The name “Bob Smith”—or any real person name—may not be unique, but only one individual or organization can hold a given email address. So [email protected] is likely to correspond to a specific entity.
Even if you take no counteroffensive action against “Bob,” you can take proactive defensive measures: you can go to research.domaintools.com and set a Registrant Alert for [email protected]. Now, DomainTools will send you an email any time a new domain is registered with that address.
Let’s recap your investigation using Iris Investigate:
- You began by looking up a domain of interest, acmegrommets.co
- You expanded this domain to a total of 11 by “pivoting” on the hosting IP address
- You observed a strong thematic link in these domain names
- You observed a temporal correlation among several of them in their create date
- You found a potentially identifying email address (and, incidentally, in real-world investigations it’s also common to uncover legitimate phone numbers and physical addresses)
- You discovered 5 more domains, which also shared the thematic link, tied to this address
- The History Data Panel recorded the queries you ran in establishing these links
- Bottom line: far from looking at a “lone wolf,” you now have a strongly-connected infrastructure of 16 domains, an email address linked to many of them, and a human name that may merit additional investigation
While we slightly oversimplified the process for illustrative purposes, many real-world investigations proceed very much like this. This is only possible with the depth and breadth of the DomainTools databases, and is only this easy with Iris Investigate. We hope this illustration is useful to you in your exploration of DomainTools Iris Investigate.