About DomainTools Iris Investigate

For your convenience, we’ve included the video transcription below
Hello and thank you for joining. Welcome to our DomainTools Iris platform overview. Here at DomainTools, we have been powering investigations with our domain ownership, DNS observable and web crawl data for nearly two decades. In this video we are going to be taking a quick look at our Iris investigative platform. Iris brings together a lot of the data sets that we have gathered and allows us to easily uncover additional correlated malicious infrastructure and domain activity. With the Iris omnibox here, we can start an investigation with our IP address, and email address, an SSL certificate, a Google Analytics code and more.
Look-alike Domains
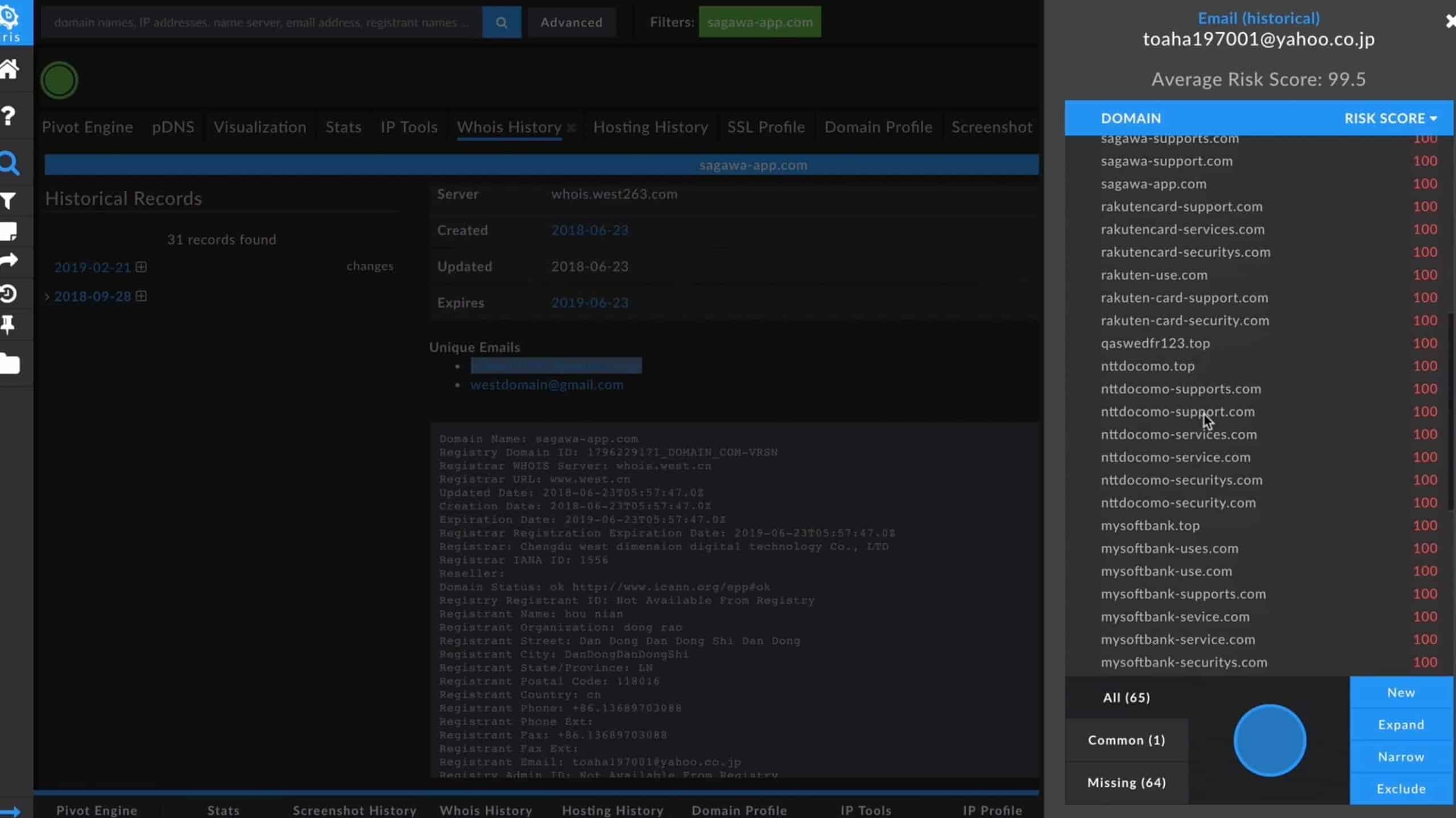
In this case, we are going to start with a domain, sagawa-app[.[com. This is a look-alike domain, targeting customers of a large Japanese shipping and logistics company, Sagawa. In the Pivot Engine we get a tabular view of the most recent data pulled for any data set that we are looking to gather. Ownership information, registrar and create date data, hosting infrastructure data, our web crawl data including Google Analytics code and Adsense trackers, mail server information, redirects, and SSL certs where available. The current contact info we have for this domain is redacted. But we can use our historical Whois tab to go back in time and take a look at what this data looked like when this domain was initially registered.
Here we can see the name, address and phone number of our registrant and we parsed out a yahoo.co[.]jp email address that we can right click to pivot on, to find any other domain in our data set that has been associated with it. This magnifying glass allows us to take a look at these domains before bringing it into the Pivot Engine, we can then determine whether they are relevant to our investigation. What we see here are 65 malicious domains targeting not only Sagawa but also Yahoo Japan, Softbank and Digi-Docomo, Rakuten, Apple, and more. A simple expand selection here will bring the rest of these domains into our Pivot Engine here so we can get a better look at what our threat actors are up to.
Historical Screenshots
Another useful feature inside of Iris, is the ability to look at our historical screenshots of domains. In this case, the Sagawa app domain shows itself to be a well-crafted look-alike, stealing the logo and layout of the real deal. However, we can see that our advisories have left a step by step guide for any unlucky visitor to follow that directs them to overwrite the security settings on their Android device and then grab a malicious application from a dropper domain, Sagawa.oicp[.]io. Using our Advanced Search interface, I am going to manually add oicp[.]io to the Pivot Engine. In this interface, you can drop up to a thousand domains at the same time or craft a more sophisticated query based off of the Pivot Engine data set. Create dates, Risk Scores, SSL certs, and etc are all played and can greatly assist in threat hunting.
Guided Pivots
Now we can get a look at oicp[.]io. Here we can see the hosting IP is highlighted, a feature we call Guided Pivots. This feature allows us to highlight potential pivot points that are likely to be useful to an investigator. In this case, it is directing us to an IP address hosting only 26 domains. We can use the Preview Pivot Pane to get a look at these, and see that our actors are hosting not only an oicp[.]io here but also several other variants on that name. Note that 4 of these are scoring a 100 according to our Risk Score. This means we have observed these on third-party lists of known-malicious domains. But these 99s just below here haven’t quite made it to any traditional intel feeds just yet. Our predictive machine learning classifiers peg these as malware domains, so you will want to expand and bring these to the Pivot Engine and export the whole thing for blocking and hunting. Iris also includes a data Visualization tool. Here we can view the domains from our Pivot Engine and layer on any data points that we collect. In this case, we are looking at the hosting IP addresses and SSL certificates that are associated with our malicious domains. We can easily hone in on the dedicated infrastructure used by our advisories and expand our hunting and pivoting from there. Our Passive DNS partner data gives us a better look at the activity timeline for our dropper domain Sagawa.oicp[.]io. These in the wild lookups andresolutions, show us its current activity. We can use this data to hunt for additional malicious IPs, subdomains, SOA records, text records, and more.
I hope this demonstration has given you a better understanding of how our data sets are presented in the Iris platform and some ideas on making domain and DNS investigations more intuitive and comprehensive. Thank you for your time.