Coming up this week on Breaking Badness. Today we discuss: The DarkSide of the Fumes, Irish Health Service on Life Support, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
The DarkSide of the Fumes
- First of all, the pipeline has been coming back online. As you’ll recall, the shutdown had been deliberate, as a containment measure and out of an abundance of caution. While it’s possible that Colonial could have kept the operation up given that the ransomware was on the IT side of the house, as opposed to the OT or operational technology side, in my opinion they were smart to do what they did, because as we’ll get into a little later, the IT and OT “sides of the house” aren’t by any means completely separated.
- DarkSide is a relatively new group or really I should say collection of affiliated groups, first surfacing around August of last year, 2020. Cybercrimers use DarkSide for encryption and to gain access to victim resources. As all the cool kids are doing these days, even though they themselves are not cool kids, it’s an “as-a-service” model—in this case RaaS, ransomware as a service. They have done some PR apparently, in the sense that they said they’d avoid certain types of businesses such as health care, education, public sector, non-profits, and, as everyone probably guessed, funeral services. Flashpoint, a cyber intel company that some folks are probably familiar with, says that they are also “big game hunters,” meaning they go after large targets who can pay big ransoms.
- Colonial Pipeline was under huge pressure to get the fuels flowing again, but other ransomware-d outfits face all kinds of pressure, too. But pay they did, to the tune of $5 million, or 75 bitcoin.
- The impact of Colonial Pipeline paying the ransom and potential regulatory repercussions are the big questions being asked, and by the way, I’m not going out on a limb here to say that other organizations are also paying the ransom in some cases, and that’s not going to just go away. But of course there’s the fear that this payment will embolden other ransomware actors.
- The Ransomware Task Force made it clear in their report that extensive cooperation and coordination across governments and the private sector are vital, that ransom shouldn’t be paid but that there should be structured pathways for assistance to affected organizations, and multiple other recommendations. Check out that report, everyone!
- The keen listener might recall that when we briefly touched on this in the last episode, I referred to a sort of semipermeable membrane between IT and OT operations in industrial control environments. There’s a theory that any control network should be entirely isolated from other networks—an air gap. The reasoning behind it is perfectly sound, but practical realities make that an exceedingly rare reality. One of the only true air gaps that I’m aware of is around the control systems for nuclear power plants. In almost every other case, there is a certain amount of data flow between the IT and OT environments. Of course, this is almost always strictly controlled through access control lists, firewall rules, etc, and in some environments there is also the use of something called a data diode, which allows traffic in one direction only (which would be outbound in the case of control networks). But it’s not an air gap and for a whole lot of reasons, it almost never will be. I think this myth persists for a couple of reasons: one is that a lot of folks just assume that the networks are set up that way, and another is that some organizations will refer to a strict set of firewall rules as an “air gap,” which of course it is not.
- The reality is that there are many impacts. A major impact is that DarkSide has taken the first part of their name seriously and gone dark, at least for the time being. No one really knows why exactly or whose doing that really was. I find it unlikely that they will stay in hiding forever, though I guess they could rebrand, kind of like Altria, which really doesn’t sound like the name of a cigarette company, now does it? I suppose we should have a contest to guess the new name of DarkSide, if in fact they do that.
Irish Health Service on Life Support
- Around early morning Irish time last Friday the HSE was told that there was a significant ransomware event affecting their core systems. These are affecting multiple hospitals in Dublin and elsewhere as these systems are all connected with local and national core health systems. Luckily, it was just healthcare records that were hit and no actual live saving systems or equipment. Everything was running, but with a large delay and all emergency services functional.
- The HSE immediately contacted the country’s National Cybersecurity Centre (NCSC) which put into effect their crisis response plan. Props to them for having that already in place for this kind of event as it very likely saved them millions of dollars. In this case they shut down several of their systems to contain the problem.
- According to Iris health officials, it was a human powered ransomware attack which points to the more sophisticated gangs. In this case it’s being reported that the Conti ransomware group is behind the intrusion. Conti is tied to TrickBot/BazarLoader/etc as an initial infection vector.
- The HSE has been very transparent. First and foremost they said that they would not be paying the ransom whatsoever. Always lovely to what that especially after the pipeline payout of several million to the Darkside gang. HSE also said this is the most significant cyber attack that has ever happened on the Irish state and if you look at how widespread the effect is that certainly seems to be the case. They also mentioned that they were working with McAfee to rectify the issue so they are in good hands there.
- You know I was spending a lot of time thinking about this the other day as I read through the Verizon DBIR report on intrusions over the last year. It’s intriguing because if you look at the medical industry they really haven’t been as attacked as much as the public sector has been, nearly ¼ of the amount of intrusions. I think we’ve heard about hospitals and health systems a lot because it makes a big story, but the truth is there is a lot of ransomware happening all the time that we don’t hear about at all. These high profile cases that make the news are just the whales. These gangs are making a lot of money on the side and we never hear about those infections.
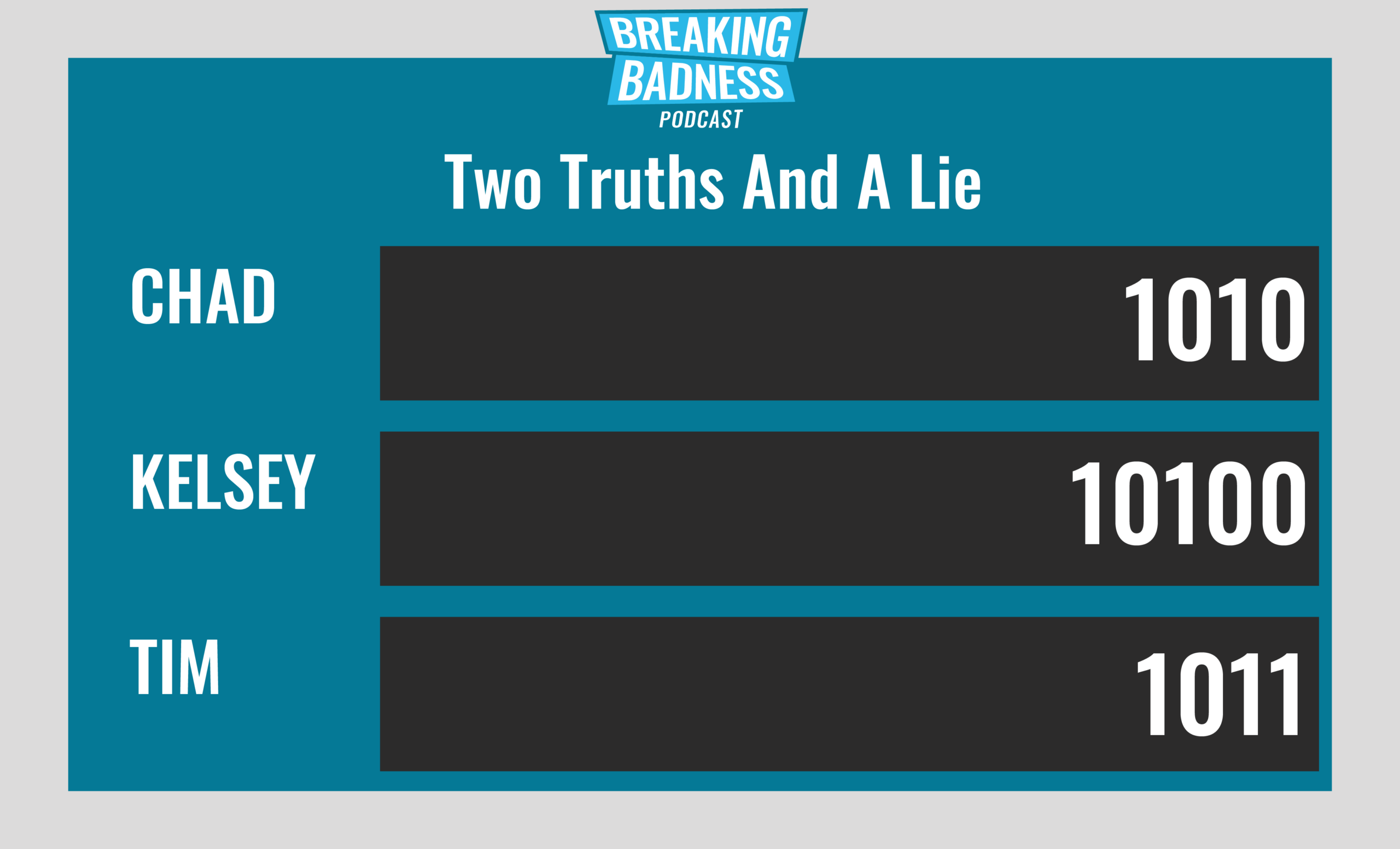
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
Current Scoreboard
This Week’s Hoodie/Goodie Scale
The DarkSide of the Fumes
[Chad]: 8/10 Hoodies
[Tim]: 8/10 Hoodies
Irish Health Service on Life Support
[Chad]: 9/10 Hoodies
[Tim]: 6/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!




