The Resurgence of the “Manipulaters” Team - Breaking HeartSenders
Share this entry
The Pakistan-based “Manipulaters” (their corruption of the word “manipulators”) represent a notorious and, in some respects, pioneering cybercrime empire. The Manipulaters have a decade-long history of selling phishing kits, spamming services, and malware. This history spans dozens of cybercrime marketplaces and the malicious domains associated with them are measured in the tens of thousands. The Manipulaters have enabled countless attacks against enterprises and customers; most security teams at Fortune 100 companies have encountered their deployed phishing kits or received spam from their mailers.
Nearly nine years ago, Brian Krebs released research on the Manipulaters Team, a fraud group that tricked people into giving up usernames and passwords via fake bank and e-commerce sites. Since then, the Manipulaters claimed to be turning over a new leaf–righting their wrongs and refraining from running large fraud schemes.
In 2021, Krebs reviewed the social media postings from the Manipulaters which showed they were prospering, while rather poorly hiding their activities behind a software development firm in Lahore that secretly enabled an entire generation of spammers and scammers.
In late 2023, our researchers stumbled upon a set of domains that linked back to their organization. That triggered the subsequent investigation into the historical domain and host records that unearthed that the Manipulaters have profited for more than a decade by selling vast quantities of phishing kits, commodity malware and spamming services, and more – eventually expanding into selling web domains, both for their own use as well as resale to other criminals. Coincidentally, in early 2024 and apropos of nothing, the Manipulaters reached out directly to Krebs asking for his removal of previous stories on their exploits.
Though lacking the technical sophistication many other large cybercrime vendors have, their most notable characteristic is being one of the earliest phishing-focused cybercrime marketplaces to horizontally integrate their business model while also spreading their operations across several separately branded shops. Unfortunately for them, another notable characteristic is a history of severe operational security inconsistencies.
Using a combination of domain-related data and open-source intelligence (OSINT) techniques, DomainTools Research identified dozens of Manipulaters cybercrime marketplaces that show a threat actor group that represents a growing concern. This concern is not limited to innocent consumers and enterprises; a series of operational security failures call into question the integrity of their criminal enterprise and may even suggest some of their customers are also targets. Ironically, the most significant risk to Manipulaters’ customers might be the Manipulaters themselves.
This piece explores both facets of this prolific, but perhaps enigmatically flawed, group.
The Role of Cybercrime Marketplaces
Cybercrime marketplaces serve a foundational role in the underground economy. These marketplaces exist primarily as a storefront for cybercrime service offerings but can also become de facto communities. Such communities can enable cybercrime in several ways, including driving innovation by associating cybercrime with financial reward, refining new techniques and methods that benefit members of the group, and lowering the technical barriers to entry to cybercrime by providing tools developed by others. Importantly, removing technical barriers to entry also increases the addressable market such cybercrime marketplaces cater to.
Marketing Apparatus
What the Manipulaters lack in technical sophistication, they make up for in scale and scope. Whereas other cybercrime groups seek to build an iconic brand, the Manipulaters prefer to deploy dozens of cybercrime shops using different names. This strategy is likely based on several motivating factors, including:
- Spreading risk across many domains makes the takedown of a single domain less operationally disruptive and may help avoid law enforcement scrutiny by appearing small.
- Operating several brands allows for reputation laundering if a customer accuses them of being a scam or offering low-quality products.
- Saturating the underground economy with seemingly disparate products and services that make new entrants less likely to compete.
The Long Road to Now
The Manipulaters are rapidly expanding operations following a period of relative inactivity after journalist Brian Krebs identified several of their members. This expansion appears to focus more on spamming tools and sender services, likely because of the overabundance of phishing kits and the relative ease of cloning them is less profitable than a services model.
Evidence suggests that new members have joined and at least one early member of the Manipulaters left the group. They appear to have a physical presence in Pakistan, including Lahore, Fatehpur, Karachi, and Faisalabad.
The Manipulaters have a long history of selling phishing kits, account checkers, proxy and RDP access, “bulletproof” hosting, and forged identity documents. Regarding software applications, they often rebrand or cobble together existing tools. Their priority now appears to be selling spam services.
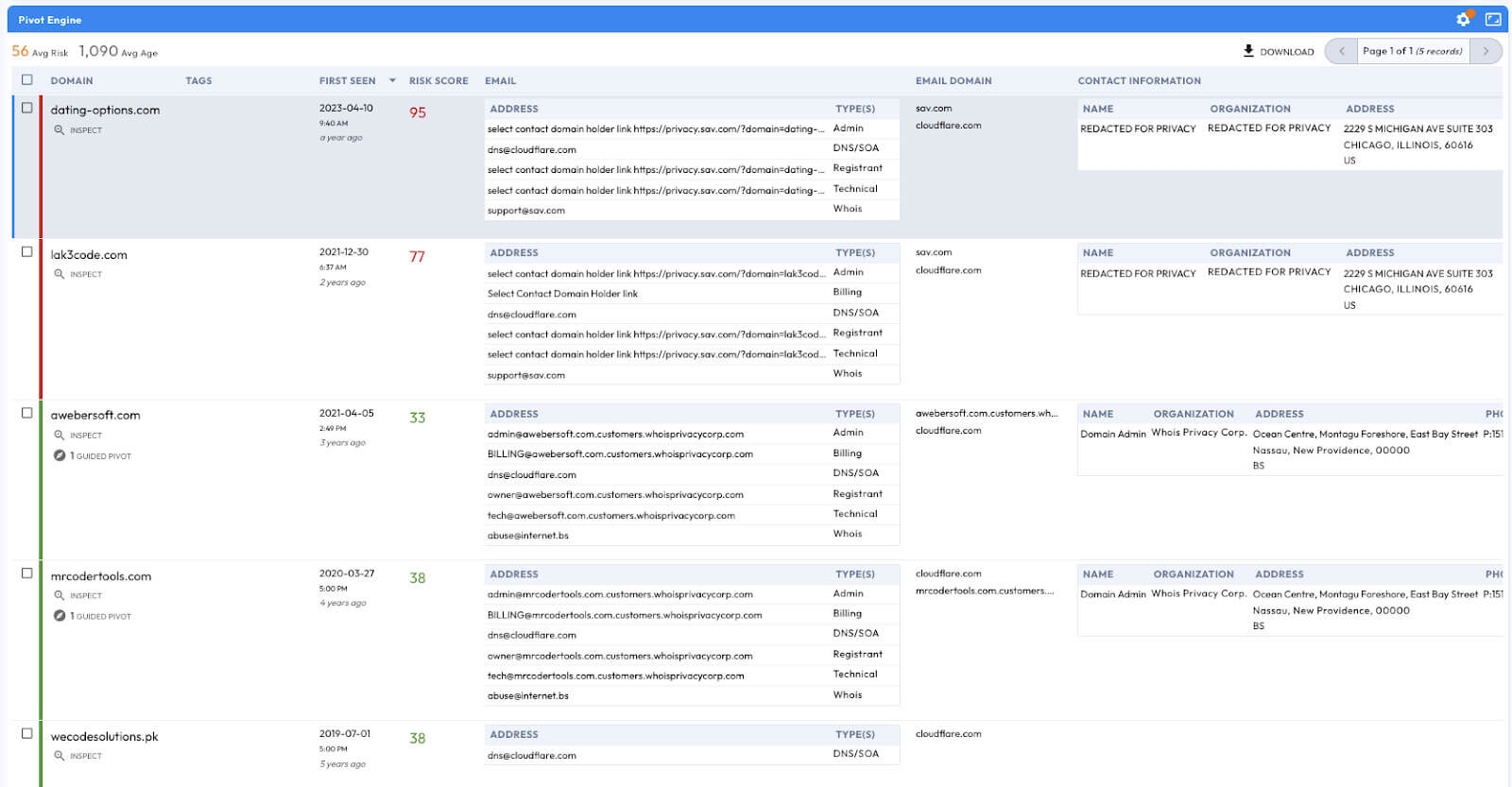
The domain wecodesolutions[.]pk is closely associated with the Manipulaters. This domain proves useful in collecting additional domains associated with the host 191.101.164[.]254 (Figure 1). Two domains are of particular interest:
lak3code[.]com
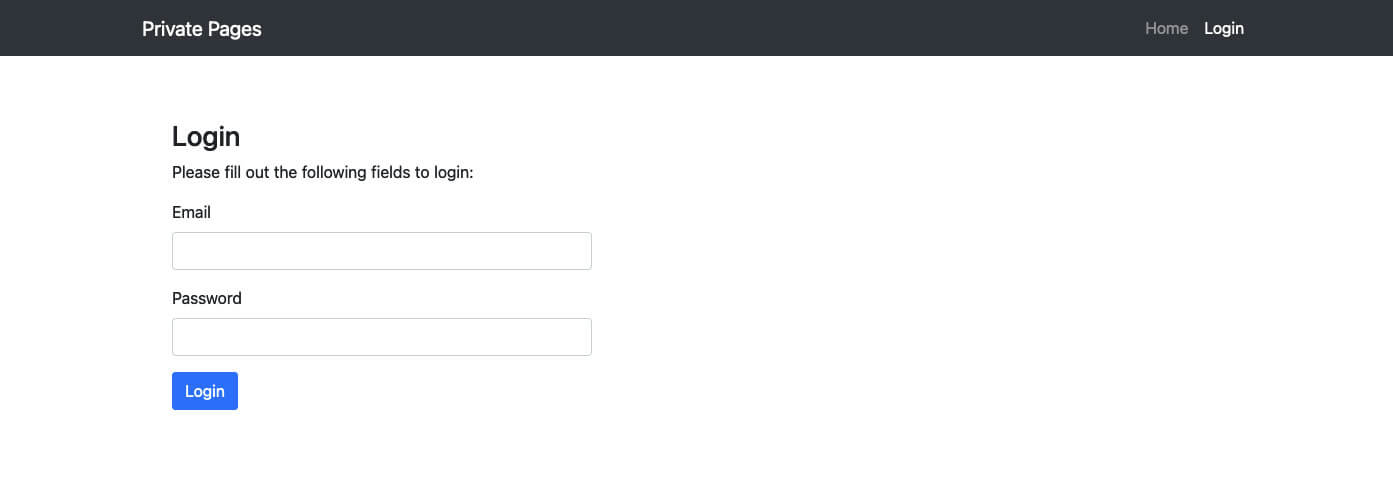
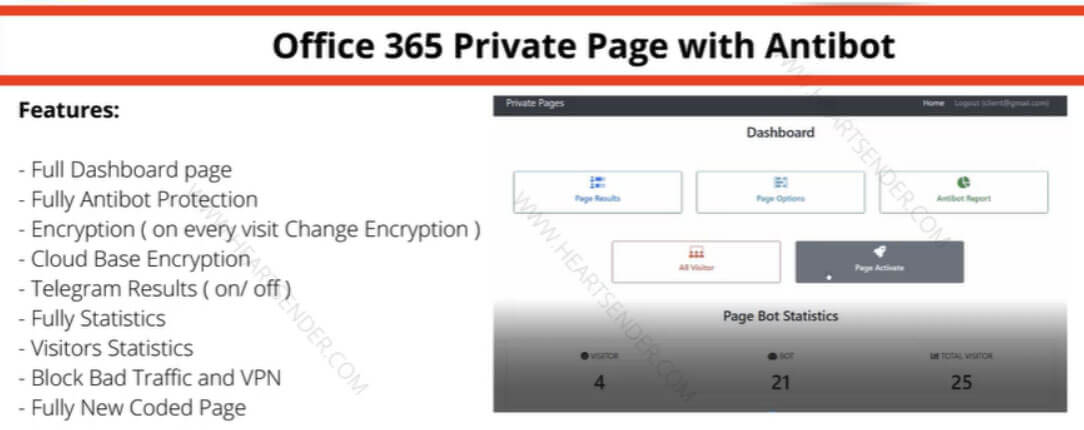
The interface shown in Figure 2 resembles one featured in an advertisement for “Office 365 Private Page with Antibot” posted on heartsender[.]com, another Manipulaters storefront (Figure 3). The ad includes a list of features used in modern phishing campaigns combined with a management panel.
mrcodertools[.]com
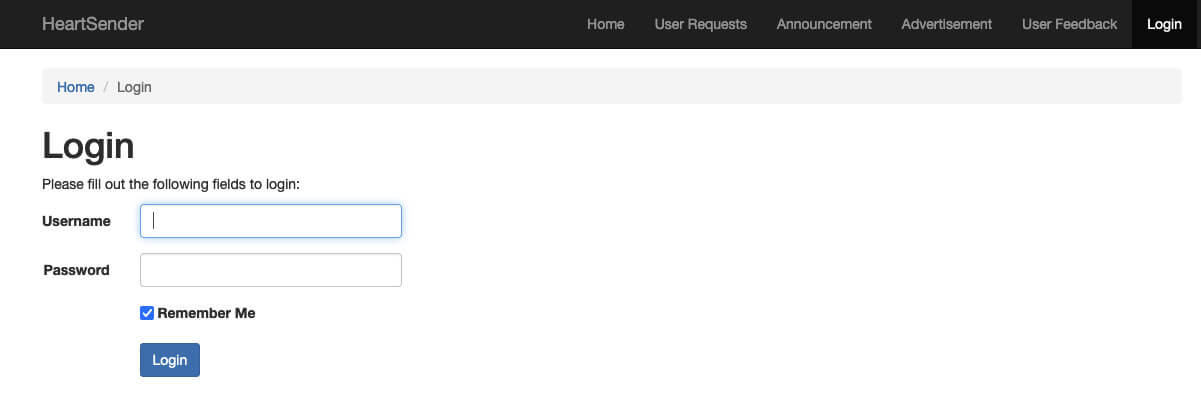
The path /web/site/login appended to the domain mrcodertools[.]com reveals a management panel named “HeartSender” that resembles the one found at lak3code[.]com/web/site/login (Figure 4). Several menu items are notable: user requests, announcements, advertisements, and user feedback. Most of these pages require an authenticated user to access them. Some, however, do not.
The “Advertisements” screen contains a data table with more than 10,700 rows. Each entry includes a specific software product the Manipulaters sell (Figure 5). This panel may also represent part of the apparatus the Manipulaters use to manage customers and promote their services.
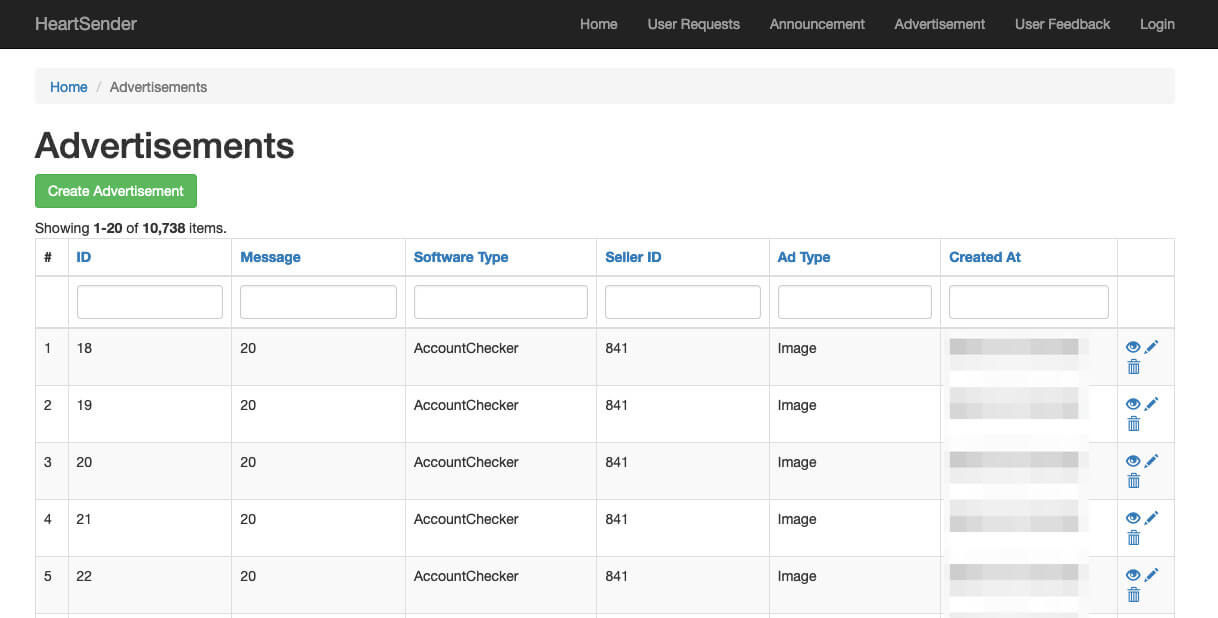
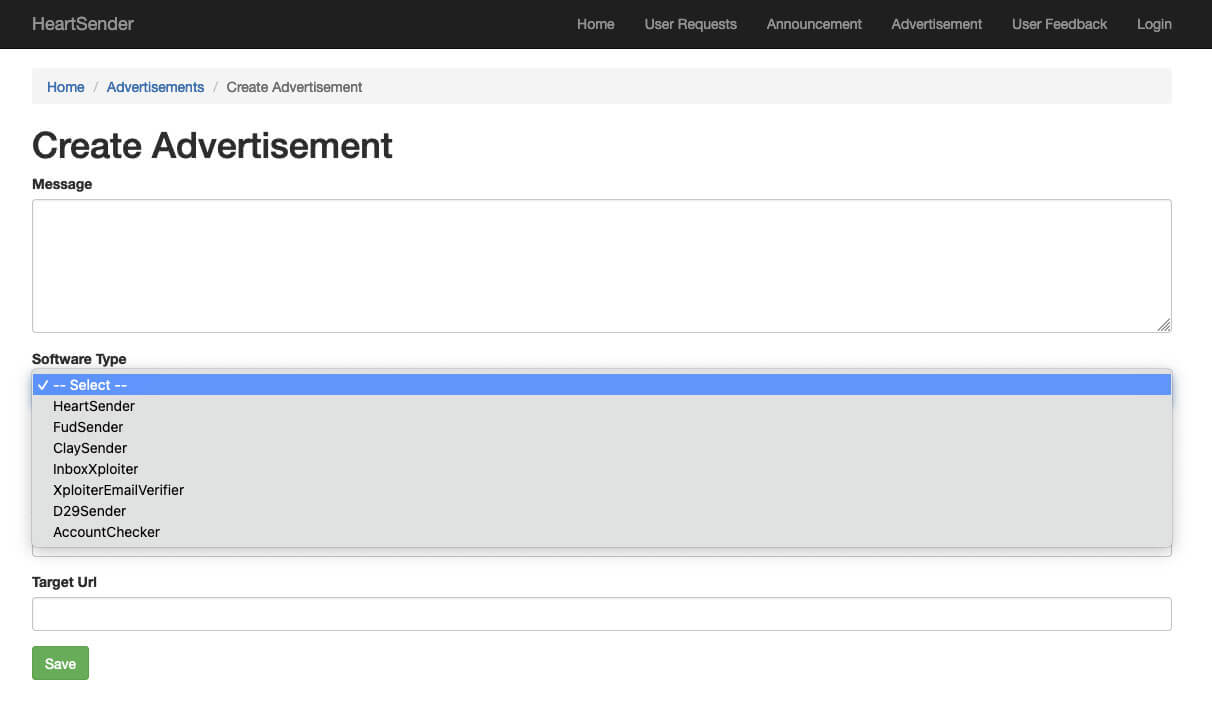
The “Create Advertisement” page is similarly accessible by an unauthenticated user. The dropdown menu for the field “Software Type” reveals the names of several products: HeartSender, FudSender, ClaySender, InboxXploiter, XploiterEmailVerifier, D29Sender, and AccountChecker (Figure 6). These product names proved helpful.
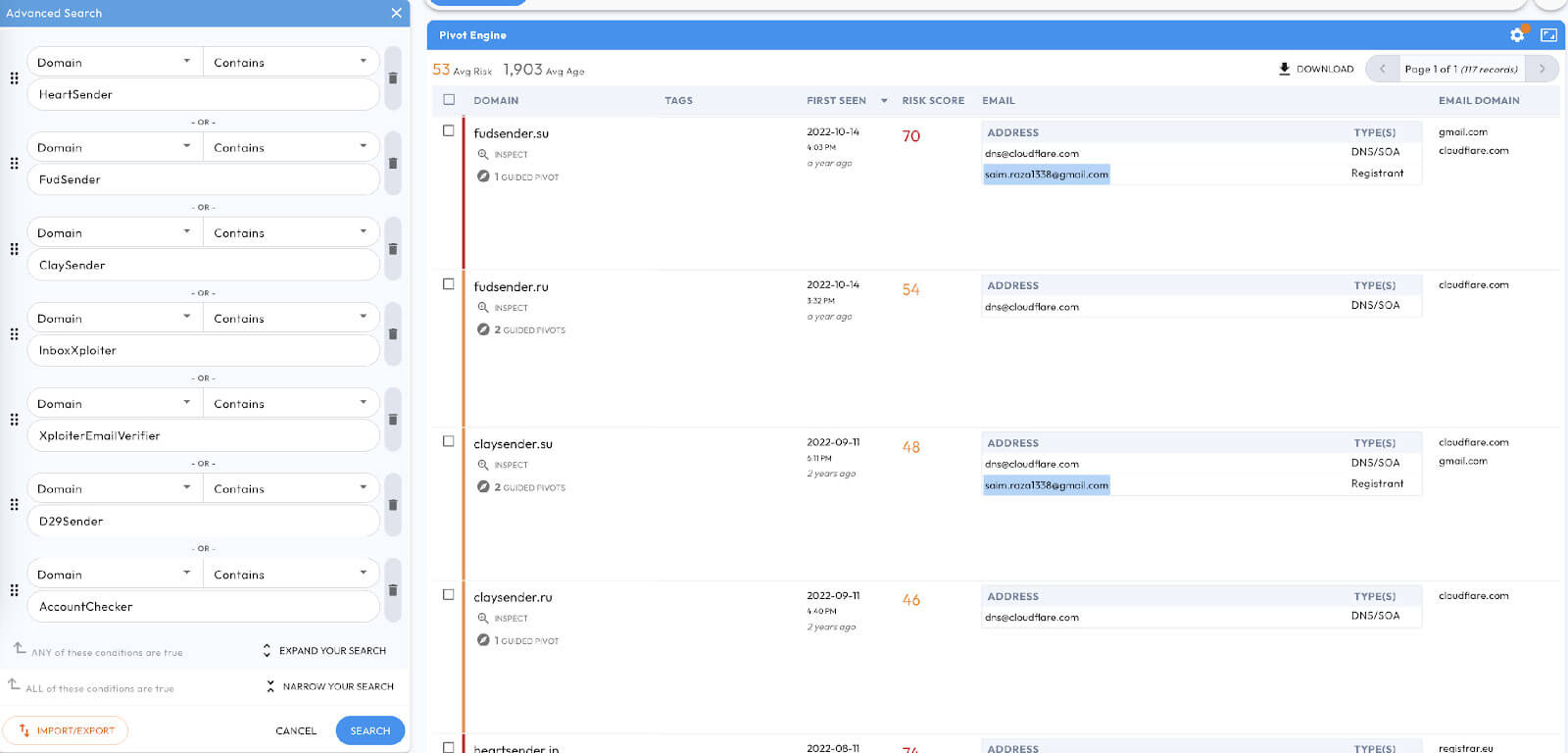
Building a query in DomainTools Iris Investigate for domains containing the product names listed in Figure 6 returns several results, including 117 domains, several hosts, and notable email addresses closely associated with the Manipulaters like saim.raza1338@gmail[.]com (Figure 7). These results offer helpful footholds and pivots to identify additional Manipulaters-controlled domains and infrastructure.
Introducing HeartSender
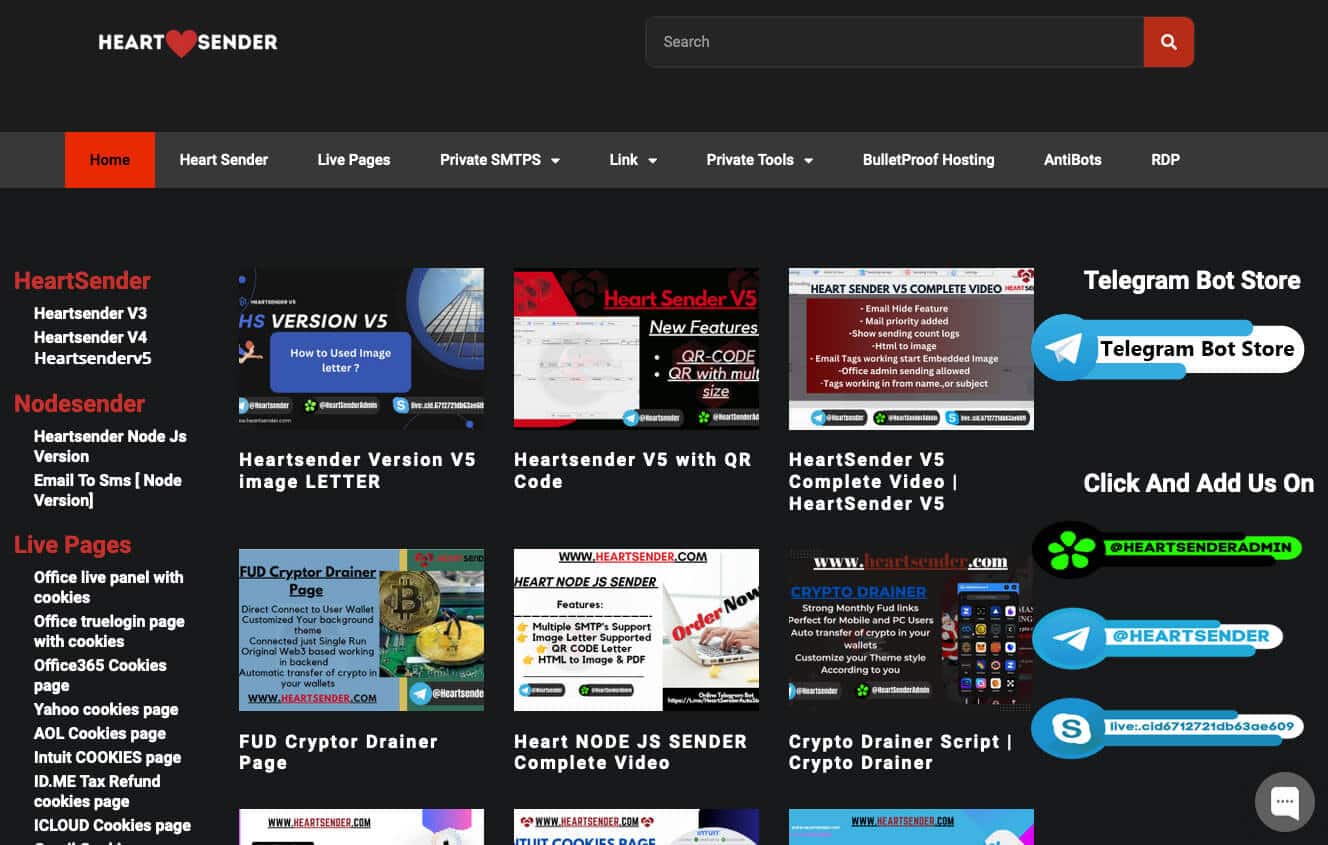
The heartsender[.]com storefront focuses on email and email-to-SMS spamming services (Figure 8). Customer response in cybercrime communities to HeartSender has been largely positive and represents a meaningful technical advancement for the Manipulaters, especially its improved email-to-SMS spamming capabilities (Figure 9). The latest person to join the Manipulaters could be the reason for the improved capabilities.
A code snippet found on another Manipulaters domain may offer insight into how the Node.js version of HeartSender works (Figure 10).
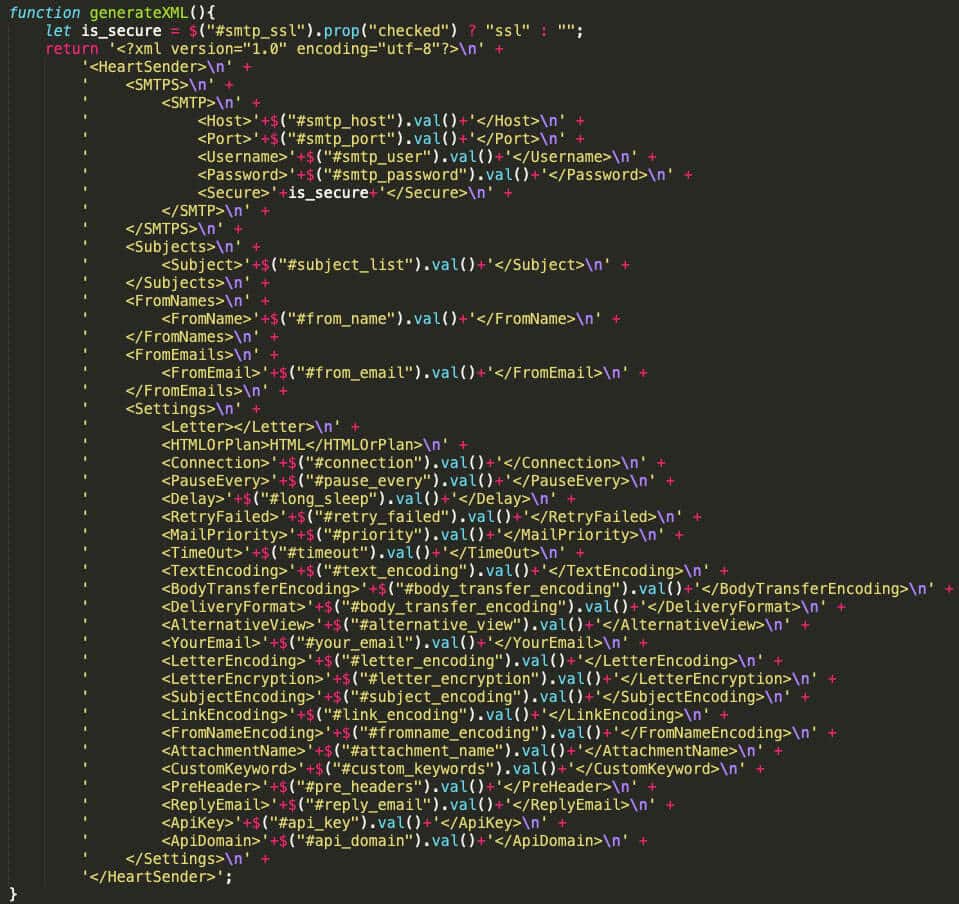
The Javascript function generateXML() dynamically constructs an XML string based on form field values using string concatenation and interpolation. This XML corresponds to a predefined scheme for sending emails using HeartSender. Perhaps the most notable portions of “main.js” are found in the <Settings> element. These elements exist to evade spam filters and detection generally, including <PauseEvery>, <Delay>, <BodyTransferEncoding>, <LetterEncoding>, <LetterEncryption>, and <LinkEncoding>.
The desktop version of HeartSender also deserves particular attention, but for different reasons.
Additional Pivots From the HeartSender Demo and a Pakistan IP Address
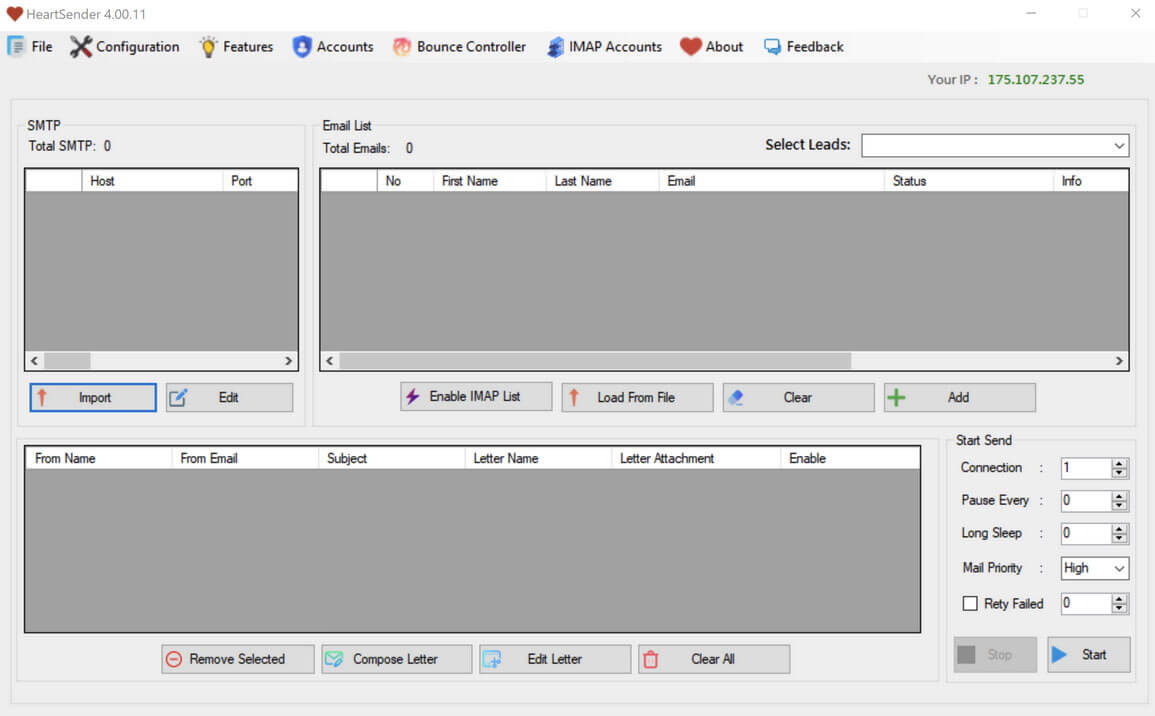
A screenshot of HeartSender 4.00.11’s interface displays the IP address 175.107.237[.]55 (Lahore, Pakistan) (Figure 11). This IP address is associated with several accounts, including the email addresses fudtoolshop@gmail[.]com, bodla057@gmail[.]com, mr6450465@gmail[.]com, and admin@coderteam[.]in. It is also associated with the usernames “saimraza786” and “mrbodla.” These naming conventions and aliases closely match those historically tied to the Manipulaters.
Domain registrations associated with the email address “fudtoolshop@gmail[.]com” return nearly 500 domains, many flagged as high risk in DomainTools Iris Investigate. The email address bodla057@gmail[.]com returns a domain registration for bodla[.]info with registrant “Hamza Bodla” in Fatehpur, Pakistan.
From HeartSender to dozens of Manipulaters-run shops
The host 185.11.145[.]254 has long been associated with Manipulaters activity and revealed dozens of deployed shops.
The Manipulaters often pair shop domains with domains containing tutorials and promotional videos for their products, providing a helpful point of reference for mapping the group’s domain footprint. Some of these domains include:
| Shop | Promotion domain |
| buyspamtool[.]com buyspamtool[.]ru | bstvideos[.]com |
| claysender[.]com | claysendervideos[.]com |
| d29sender[.]com | d29sendervideos[.]com |
| freespamtool[.]com | freespamvideos[.]com |
| freshspamtool[.]com | freshspamtoolvideos[.]com |
| fudpage[.]com fudpagetools[.]com | fudpagevideos[.]com |
| fudspam[.]com fudspam[.]su | fudspamvideos[.]com |
| fudtools[.]com | fudtoolvideos[.]com |
| gxsender[.]com | gxsendervideos[.]co |
| heartsender[.]com heartsenderscampages[.]com | heartsendervideos[.]com |
| officesender[.]com | officesendervideos[.]com |
| smtpshop[.]com | smtpshopvideos[.]com |
| toolsplug[.]com | toolsplugvideos[.]com |
| xleetshop[.]com | xleetvideos[.]com |
Trouble on the Horizon Targeting USPS-Related Impersonation and Session Cookie Grabbing
The Manipulaters’ newfound interest in email-to-SMS spam could be in response to the massive increase in smishing activity impersonating the USPS. Proofs posted on HeartSender’s Telegram channel contain numerous references to postal service impersonation, including proving delivery of USPS-themed phishing lures and the sale of a USPS phishing kit (Figures 13-14).
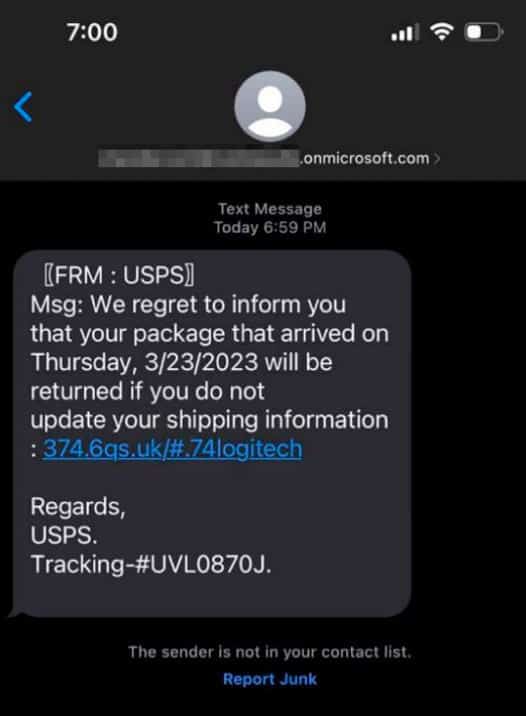
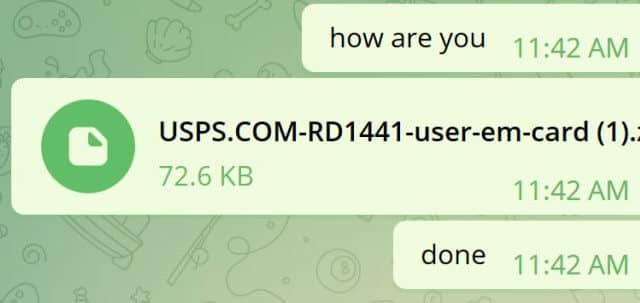
The Manipulaters appear to favor spamming services paired with session cookie grabbers, including operating a cybercrime shop focused almost exclusively on cookie theft and even creating an account named grabber@fudteambilling[.]com (Figure 15). This dangerous combination can make account takeover activity much less detectable than traditional credential phishing.
A Case Study in Technical Debt and Sloppy Authentication
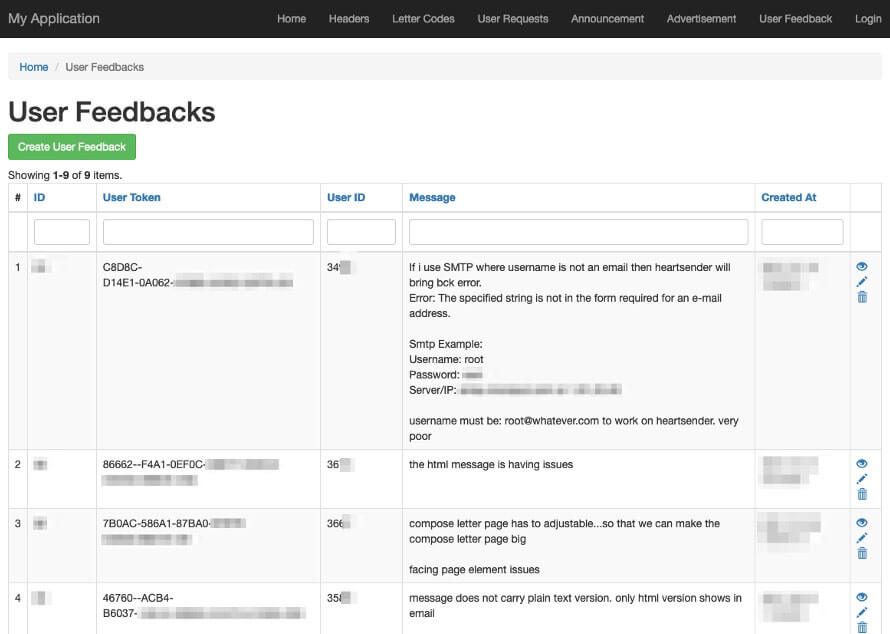
Ironically, the Manipulaters may create more short-term risk to their own customers than law enforcement. The data table “User Feedbacks” (sic) exposes what appear to be customer authentication tokens, user identifiers, and even a customer support request that exposes root-level SMTP credentials–all visible by an unauthenticated user on a Manipulaters-controlled domain. Given the risk of abuse, this domain will not be published.
There is so much more, however. Breach records associated with the unnamed domain and other domains used by the Manipulaters reveal a large online footprint paired with several severe operational security failures.
When It Rains, It Pours
Research suggests that several PCs associated with the Manipulaters have been compromised by stealer malware for a considerable amount of time, exposing vast swaths of account-related data along with an outline of the group’s membership, operations, and position in the broader underground economy. Curiously, the large subset of identified Manipulaters customers appear to be compromised by the same stealer malware. All observed customer malware infections began after the initial compromise of Manipulaters PCs, which raises a number of questions regarding the origin of those infections.
These breach records can be divided into three clusters. Overlap exists between activity clusters likely because several people were working on the same projects.
Cluster “Adnan”
Associated usernames: adnan, grabber, harsh, mrcoder, xleet
Associated email addresses: admin@fudsender[.]club, admin@fudsender[.]com, admin@heartsender[.]com, f.udtoolshop@gmail[.]com, fudscam@fudsender[.]com, fudsender.utube@gmail[.]com, fudspam.toolss@gmail[.]com, fudspam@hotmail[.]com, fudtool786@gmail[.]com, mohsinaseller@gmail[.]com, mr.codertools@gmail[.]com, saim.pays@gmail[.]com, xleet@fudsender[.]com
Associated domains: busypaymant[.]com, fudsell[.]com, fudsender[.]com, fudsender[.]store, fudteambilling[.]com, fudtool[.]su, fudtoolshop[.]com, fudtoolvideos[.]com, mrcodertools[.]com, profud[.]tools, provip[.]tools, saimraza[.]com
Cluster “Imran”
Associated usernames: fudtoolr, imran231, saimraza786, turbopk
Associated email addresses: abdulrehman940@gmail[.]com, admin@buyspamtools[.]com, admin@fudsender[.]com, admin@fudteam[.]com, admin@remitciti[.]com, admin@turbopk[.]net, ikorai99@gmail[.]com, info@shahg[.]co, itmalik91@gmail[.]com, itwebs92@gmail[.]com, saim.raza1338@gmail[.]com, sh4hgh3x0r@gmail[.]com
Associated domains: billing.saimraza[.]info, fudtoolshop[.]com, fudtoolvideos[.]com
Cluster “Bodla”
Associated usernames: live:fudtoolshop, mr6450465, mrbodla, mrbodlah, saimraza007, saimraza123, saimraza786
Associated email addresses: admin@coderteam[.]in, admin@fudteam[.]com, bodla0143@gmail[.]com, bodla057@gmail[.]com, fudtool786@gmail[.]com, fudtoolshop@gmail[.]com, help.alizain@gmail[.]com, henrylukeusa@gmail[.]com, mr6450465@gmail[.]com, osamaevee2000@gmail[.]com, sahrn512@gmail[.]com
Associated domains: bodla[.]info, coderteam[.]in
Conclusion, Where Do We Go From Here?
The Manipulaters offer illustrative examples of how cybercrime vendors integrate into the broader underground economy. In the decade they have been active, the Manipulaters have appeared in and created many different marketplaces selling phishing kits, malware, spamming services and more. Most recently, DomainTools Research has found them moving into email-to-SMS services with HeartSender, as well as pairing spamming services with session cookie grabbers. We have also found some of their infrastructure seems to be accessible by unauthenticated users and that some of their (and their customers’) infrastructure has been compromised by malware.
Given the Manipulaters’ resurgence and improved capabilities, DomainTools Research urges businesses and consumers to remain vigilant against threat actor groups like the Manipulaters and those they enable with their products and services.
Download our Security Bulletin for more additional background details on the Manipulaters and to explore the role of historical Whois and DNS data in mapping a domain-focused threat actor’s footprint.
For free 2024 lists of domains, email addresses, and usernames associated with the Manipulaters and a non-exhaustive collection of domains from 2015 to early 2018, visit our SecuritySnacks GitHub Repo.
Active Shops – 03.25.24:
bulktools[.]su
buyfreshtools[.]com
buyspampages[.]com
buyspamtool[.]com
buyspamtool[.]ru
claysender[.]com
d29sender[.]com
freespamtool[.]com
freshscampages[.]com
freshspamtool[.]com
freshtoolshop[.]com
fudfreshtools[.]com
fudlinkheartsender[.]com
fudpage[.]com
fudpagetools[.]com
fudscampages[.]com
fudscams[.]net
fudsender[.]com
fudsender[.]live
fudsender[.]ru
fudspam[.]com
fudspam[.]su
fudtools[.]com
gxsender[.]com
heartsender[.]com
heartsenderscampages[.]com
inboxxploiter[.]com
newspamtools[.]com
nodesender[.]com
officesender[.]com
scampageshop[.]com
smtpshop[.]com
spamfather[.]com
spamtoolx[.]com
stroxshop[.]com
toolsplug[.]com
xleetshop[.]com
Email addresses:
admin@buyspamtools[.]com
admin@claysender[.]com
admin@coderteam[.]in
admin@fudsender[.]club
admin@fudsender[.]com
admin@fudsender[.]store
admin@fudspam[.]tools
admin@fudteam[.]com
admin@heartsender[.]com
admin@remitciti[.]com
admin@turbopk[.]net
afaqkhan.khan334@gmail[.]com
ahmadbodla@yahoo[.]com
aliraza0347601@gmail[.]com
askimran.33@gmail[.]com
bluebtcus@gmail[.]com
bodla_143@yahoo[.]com
bodla0143@gmail[.]com
bodla057@gmail[.]com
burhanahmad107@hotmail[.]com
emraanmurtaza9@gmail[.]com
f.udtoolshop@gmail[.]com
faisal_awan2011@yahoo[.]com
freshtoolsshop@gmail[.]com
fud.tool.s@gmail[.]com
fudpages@gmail[.]com
fudpagez@gmail[.]com
fudscam@fudsender[.]com
fudsender.utube@gmail[.]com
fudspam.toolss@gmail[.]com
fudspam@hotmail[.]com
fudtool786@gmail[.]com
fudtoolshop@gmail[.]com
grabber@fudteambilling[.]com
gxsender@hotmail[.]com
hamzaseller@gmail[.]com
heartsender123@gmail[.]com
heartsenderupdates@gmail[.]com
ikorai99@gmail[.]com
imranmurtaza03@gmail[.]com
imranmurtaza323@gmail[.]com
info@shahg[.]co
itwebs92@gmail[.]com
javidtabiseller@gmail[.]com
mohsin@gmail[.]com
mohsinaseller@gmail[.]com
mr_coder@inbox[.]ru
mr.codertools@gmail[.]com
mr6450465@gmail[.]com
mrbodla@gmail[.]com
mrbodla@yahoo[.]com
osamaevee2000@gmail[.]com
pakfunplus91@gmail[.]com
privatetools26@yahoo[.]com
rainyeyes143@gmail[.]com
saim.pays@gmail[.]com
saim.raza1338@gmail[.]com
saim.raza933@gmail[.]com
saimmalik123@yahoo[.]com
saimraza1992@gmail[.]com
sanwal_raza66@yahoo[.]com
sh4hgh3x0r@gmail[.]com
smtpshop.su@yahoo[.]com
sunnyseller@gmail[.]com
support@mr-coder[.]com
talhasheikh918@gmail[.]com
xitforum00@gmail[.]com
xleet@fudsender[.]com
Usernames:
adminfreshscampages
buyfreshtool
clay_sender
clayadmin
d29admin
d29sender
d29senderupdate
freshfud_tools
freshscampagesadmin
fud spam
fud_page
fudfreshtool
fudpages
fudpagesadmin
fudsender
fudspam_com
fudtool
fudtoolshop
hamzabodla
heartsender
imran33
krank007
fudtoolshop
mr-coder
mrbodla
mrbodlah
mrcoder
node_sender
nodesenderadmin
rainy_eyes
rameez786
saadaliadmin
saimraza
saimraza007
saimraza786
sunny_bodla057
39 Domains Seized from the Manipulaters [Update]
The Justice Department’s Criminal Division and FBI, in cooperation with law enforcement partners in the Netherlands have taken down 39 domains and their associated servers used by the Manipulaters (a.k.a. Heartsender, Saim Raza) on January 30, 2025. The seizure of these domains is intended to disrupt the ongoing activity of groups such as this one and stop the proliferation of these phishing kits within the cybercriminal community.
Read the DOJ press release here.
If you would like to get in touch with us on how we unearthed this information, please contact us here.






