How DomainTools and Phantom Work in Harmony so you can SOAR
Updated: January 29, 2020
One of the most exciting developments in the cybersecurity product space right now is elevation of orchestration software from a niche tool to an essential capability.
Vendors and analysts have christened the category “SOAR”, an appropriately aspirational acronym that stands for “security orchestration, automation and response”. It reflects the broad application of these products to a variety of use cases.
Perhaps the most conspicuous endorsement of this trend was Splunk’s acquisition in 2018 of Phantom for an impressive $350 million. I listened with keen interest to Splunk’s rollout of their new “adaptive orchestration framework” at the 2018 Splunk conference. The presentation by Oliver Friedrichs, founder of Phantom and now at Splunk, seemed right on target to address challenges I often hear from security leaders trying to scale their orgs.
Listening to Oliver there in Orlando also evoked a sense of nostalgia – I remember a couple years ago when an email showed up in my DomainTools inbox from Oliver asking for API keys to build a DomainTools integration in Phantom. I had no idea what he was building at the time, but as I looked closer, I quickly fell in love with the product he and his team were building, and I’m proud they selected DomainTools to be among their earliest Phantom integrations.
The orchestration use case was also top-of-mind when my colleagues and I put the final touches on the Iris Investigate API that we rolled out last year. There are specific features we built into the API, like Guided Pivot counts, component risk scores, and tagging, because we knew they would make for awesome Phantom playbooks, and I’ve been eager to get those built ever since.
That’s why I’m so excited about the new “DomainTools Iris Investigate” Phantom app we have just released that is purpose-built to work with the Iris Investigate API. Now, all that rich Iris Investigate data is available not only for ad-hoc research on specific incidents in Phantom, but also for automated actions in Phantom playbooks.
Here’s a quick run-down of the key capabilities of the new app.
First, you’ll see we’re using the standard “whois” action in Phantom to fetch a complete Iris Investigate profile for a domain name. It’s quite silly, honestly, to call this just “whois” because registrant details represent just a subset of the domain data returned from Iris Investigate. We also include:
- IP address and hostname details for the name servers, mail servers, and web server powering the domain
- SSL certificate details and tracking codes for the website hosted on the domain
- Email addresses extracted from DNS SOA record
- DomainTools Risk Score, with components & evidence, and
- Investigative tagging for cross functional collaboration
That last one is quite powerful, especially in the context of a product like Phantom.
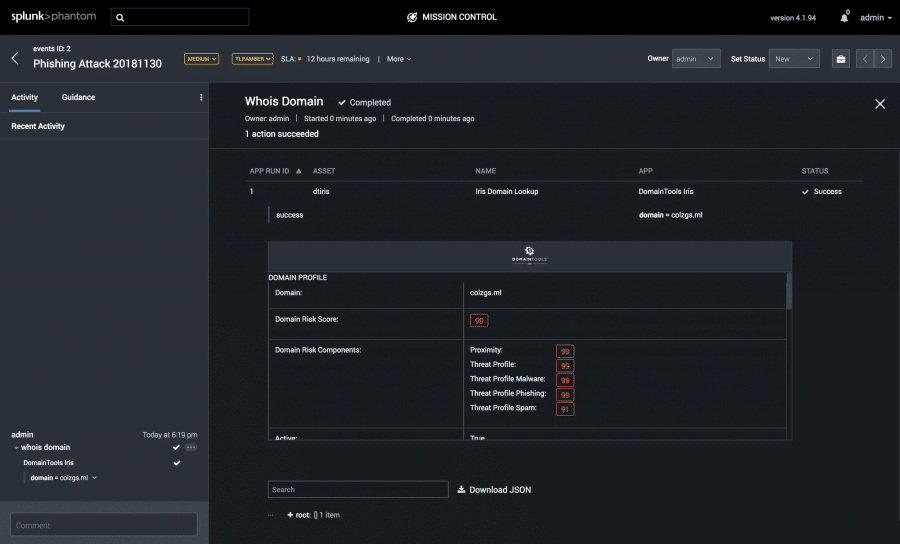
If you’re already using DomainTools Iris Investigate, or even one of our SIEM integrations, you’ve come to appreciate the predictive nature of the DomainTools Threat Profile and Proximity-based, Domain Risk Score. The Iris Investigate API returns that score, but also gives the individual scores for each machine-learning classifier, and some insight into the evidence for the prediction.
We leveraged Phantom’s flexible UI framework to give a nice color-coded view to the Domain Risk Score on the interactive investigation page, but the real power is in Phantom’s playbooks, where you can now make targeted decisions based on those component risk scores. Want to respond more urgently if we give a domain a score of 90 for malware? Or take a different action for moderately risky likely-spam domains? Easily done, courtesy of the decision blocks in a Phantom playbook.
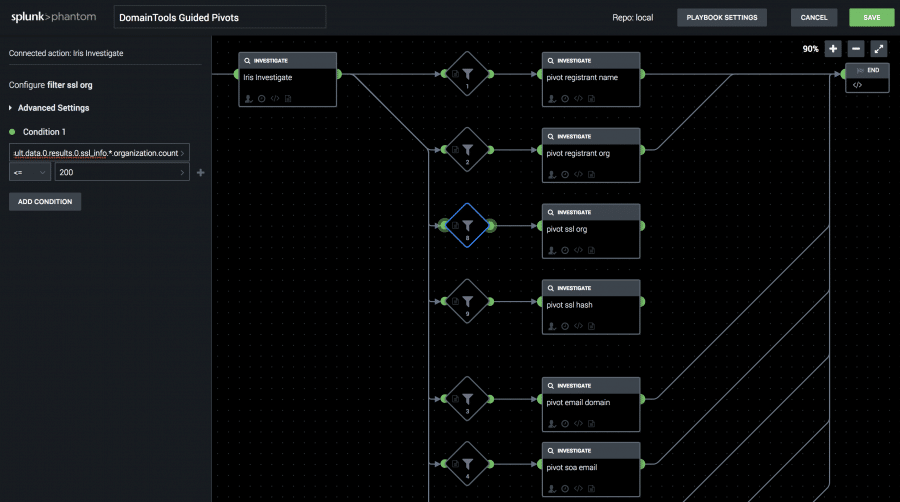
But if you really want to do something awesome with those Phantom decision blocks, you should take a good look at the Guided Pivot counts in Iris Investigate. These counts are returned on every Iris Investigate result on more than a dozen fields, and they indicate how many other domains are shared with that value.
For example, the IP address for domaintools.com returns a Guided Pivot count of 4, which makes it a perfect target for a follow-on pivot to enumerate those connected domains. That lets you easily build an “auto pivot” playbook that replicates typical analyst actions and let’s you proactively block shared infrastructure with precision.
Those pivot searches are available in several “reverse” actions to support legacy playbooks, but if you’re starting from scratch, be sure to check out the “pivot” action, which has support for nearly every query type in Iris.
Additionally, we have built in tagging to serve as a way for investigators to decorate data in an Iris investigation. Organizations can leverage their tags created in DomainTools Iris within Phantom to expedite the triage process when needing additional context to inform the playbook across their security operations workflow.
There’s a lot more you can do with this in Iris, and we’re sure we’ve only just scratched the surface. The best results will come when you start leveraging the Iris Investigate API in your own playbooks, and since that API is already available to all DomainTools Enterprise Iris customers, there’s no reason to wait.




