How the Failure of Silicon Valley Bank Inspires Malicious Actors
Share this entry
On March 10th, 2023, California regulators seized Silicon Valley Bank (SVB), the 16th largest bank in the United States. Current events can be powerful tools for malicious actors seeking to manipulate public anxiety and confusion for their own gain, using phishing, credential harvesting, crypto scams, business email compromise (BEC), and other attacks. An event of this magnitude presents a glaring opportunity for scores of bad actor opportunists to exploit. In this article, I will discuss how major events like SVB’s seizure are utilized by bad actors, how to utilize Iris Investigate to see newly-created domains in real time along with additional infrastructure, and why it’s necessary to be able to quickly react using a real-life example.
Reviewing Newly-Created Domains
The first thing we will look at is how this event impacted new domain registrations related to terms such as “siliconvalleybank” and “svb.” In the graph below, you’ll see the trend for these registrations over the last 30 days. Note how on March 10th, there was a large increase in registrations that then only continued to increase on the 11th, the 12th, and 13th.
So what exactly does this data alone tell us? Well, to be honest, not much, not until we dig further. The only thing we know right now is that there are definitely more registrations happening related to these terms, but let’s dig into those newly registered domains and see what we find.
I’ll use DomainTools Iris Investigate to find the information we are looking for. If you are unfamiliar with Iris Investigate and want to learn more about the tool, I encourage you to reach out!
I’ll start with a straightforward query that I’ll share below. We’ll look at domains that contain the terms “svb” and “siliconvalley” that were “First Seen” on or after March 9th.
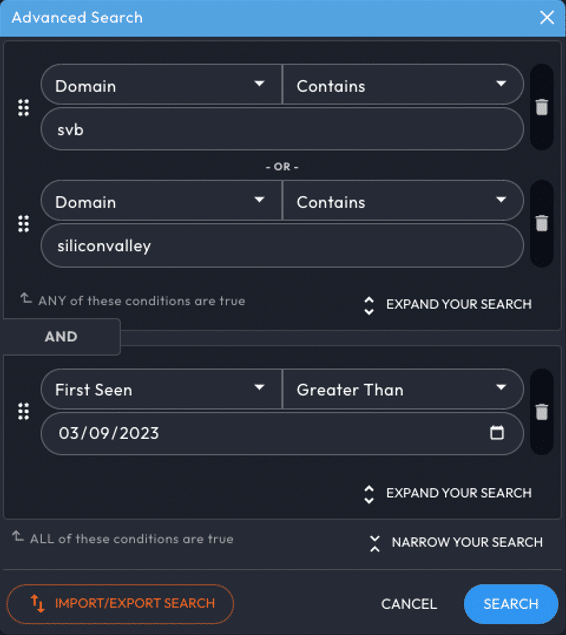
After running this search, we found a lot of suspicious-looking domains. Let’s go through some of these and try to identify intent . The very first domain on our list is svblogin[.]com, first seen 2023-03-12. With a name like that and the obvious timing, it’s easy to assume there’s probably malicious intent, but one of the first things I like to look at is the current screenshot of the home page. When looking at the current home page, things look a lot more clear.

After verifying all of the contact information on the page, it’s obvious that what seemed like malicious intent is actually just aggressive marketing. Moving on to other domains on our list, we also see login-svb[.]com, first seen March 10th, 2023, so let’s dive into this one. Again, lets first look at the screenshot of the current homepage (photo below).
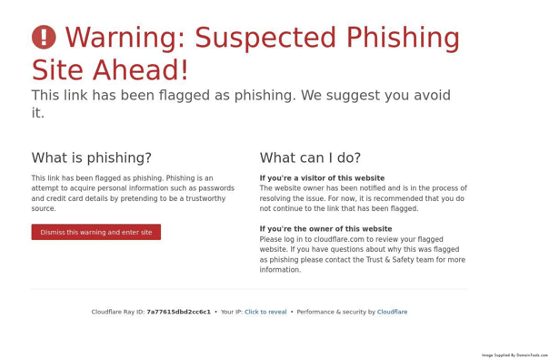
That one was easy! It looks like this domain has been flagged by Cloudflare, the host, for suspected phishing. With a name like that, it’s hard to blame them. One thing to note for any possible future investigations around specific terms, if you use the desired term in conjunction with words like “login-,” “secure-,” and “update-,” you will often find domains with malicious intent.
Using Iris Investigate To Spot Spoofing in the Wild
Alright, so far, things have been pretty straight forward; we’ve had some aggressive marketing and an obvious phishing attempt. Let’s now dive into something a little more interesting. Another domain that came up in our investigation is svb-circle[.]com, first seen March 11th, 2023. (Screenshot of homepage below)
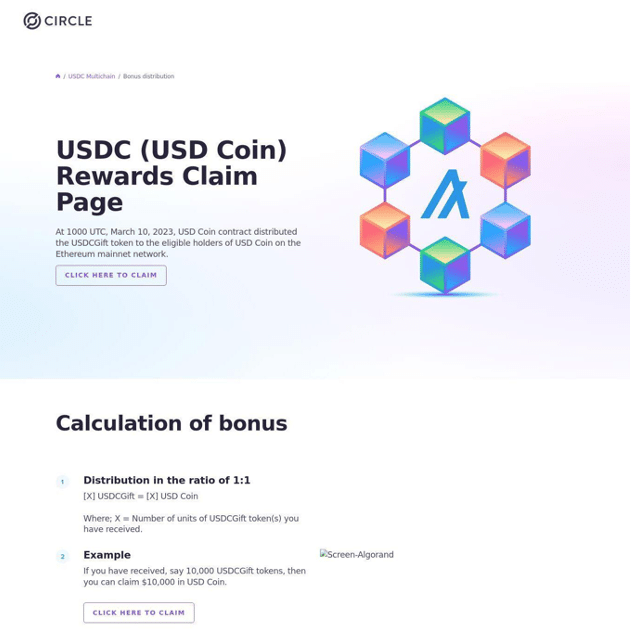
The intent here is far less obvious. After seeing this webpage, I did a little research on Circle to try and determine why they would need an SVB-related domain name. What I found was another obvious scam. Circle is a peer-to-peer payments firm which manages the stablecoin “USDC.” Circle was also a customer of SVB and had a very large cash reserve. The bank’s collapse spooked a lot of Circle customers, creating a window for bad actors to take advantage of this anxiety and uncertainty among these users. The reality is that these sites have no affiliation with Circle whatsoever and exist to steal visitors’ digital wallets and personal details by spoofing Circle, using a lure that guarantees the coin holder a 1:1 conversion rate on USDC to USD. What I also learned was that email security firm Proofpoint had also spotted Circle scams originating from the SVB fiasco; they were kind enough to share a sample via Twitter of the phishing emails sent to targets.
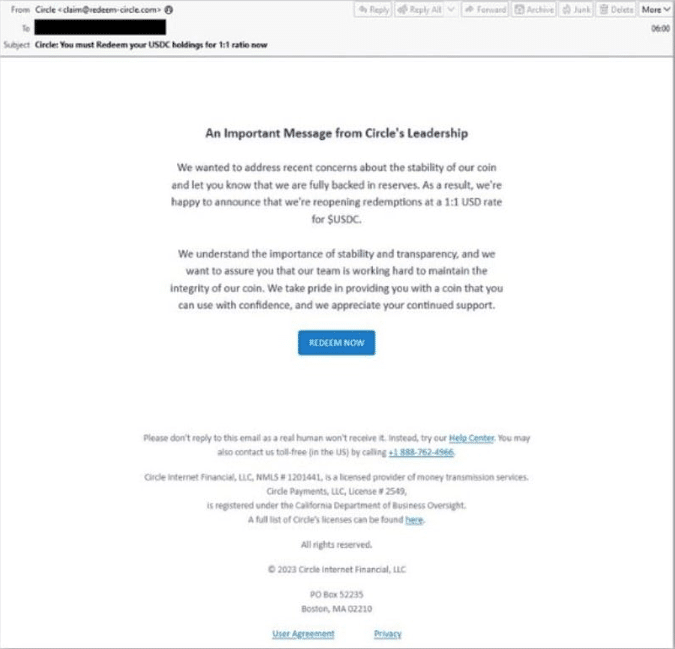
Pivoting To Find Additional Infrastructure
Now we know the malicious intent of the svb-circle[.] domain, but I wonder how deep that rabbit hole goes? Let’s explore this a little more and see if we can find additional infrastructure behind this campaign. In our previous query, we had two domains in our results with “circle” in the name, circle-svb[.]com and svb-circle[.]com, so let’s pivot from there.
First, let’s look for domains with “circle” in the name that have been registered since March 9th. With the same registrars as the two domains we currently have, this query would look something like this.
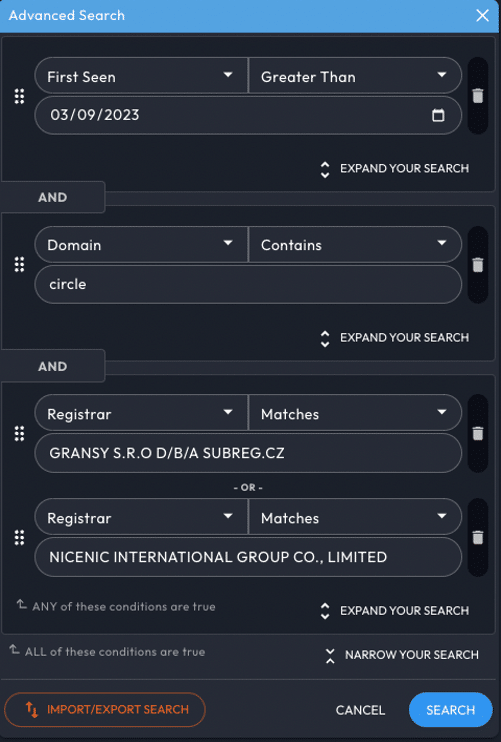
Based on that query, we find 16 additional domains. It’s worth noting that many of these domains share the same WordPress assets across them (the ones that haven’t been shutdown at least) and domain creations were observed by Iris as recently as 3 hours from the writing of this article, making this very actionable intel. Upon reviewing these, it also looks like there are multiple campaigns, all with the same goal. Interestingly, however, some have ditched SVB terms altogether, a couple examples being circle-usdc[.]net and redeemed-circle[.]com. The continued investment into this campaign would imply that this scam is getting traction. The bad actors also seem to be branching out: looking at some of these web pages, they are offering ethereum in exchange for USD, as shown below.
Now to fast forward a little bit, I continued to investigate the “Circle” impersonation scam specifically. Already at over 200 new Circle-related domain registrations since March 9th, new registrations are still occurring every day. It is possible that multiple bad actors are behind these domains, as there are over four different types of Circle scams with unique WordPress landing pages. Most concerning, hundreds of DNS queries are being resolved, indicating that the websites are receiving a small amount of traffic. Circle is just one example of a concentrated scamming effort by bad actors since the SVB seizure, though, showing the ripple effect major events like this can have and how quickly they can evolve.
In conclusion, we saw three different types of domain registrations that were influenced by the SVB seizure: opportunist marketing, obvious phishing, and a crypto scam. To give credit where credit is due, a lot of this was made easy by Iris Investigate. Utilizing data points such as Risk Score, Website Title, and SSL information, I was able to connect the dots on these multiple campaigns, even though they shared zero infrastructure. It’s also worth noting that many existing workflows would have required multiple tools to gather all this information. Because such attacks are only becoming more sophisticated and common, and because bad actors react quickly to global events such as the SVB collapse, it is even more important to be able to anticipate and identify these attacks to be able to prioritize threats and react accordingly.






