Out Here Playing Games
Share this entry
It’s 8 A.M on a Saturday morning and I don’t have to be on the hunt, but I am anyway. Two fat OSINT (open-source intelligence) books lay on the desk beside the humming computer. The legal pad next to my keyboard is busy with notes, arrows, boxes, and exclamation points. Geographic, language, and cultural data points emerge from the background. Data becomes clues, clues become guideposts, and I follow their lead to track down suspects. Maybe even the ringleader herself.
It’s 1992, and I am ten years old, glued to my first threat actor hunt: the MS-DOS game “Where in the World is Carmen Sandiego?” For those unfamiliar, “Where in the World is Carmen Sandiego” was a blockbuster computer game franchise in the 80s and 90s that put the user into the role of A.C.M.E detective investigating a ring of art thieves led by the elusive titular character Carmen Sandiego herself. The scene of the crime produced witness accounts along with physical or circumstantial clues involving geography, language, and other subjects located in the World Almanac and the Book of Facts, two bulky softcover books that came bundled with the game. Privileged to have access to a home computer from a very young age, many formative experiences unfolded from that Tandy 1000EX outward, but I didn’t put together until very recently my love of threat hunting, domain investigations, and Carmen Sandiego.

That I’m a gamer to this day comes as no surprise to anyone that knows me. I’m a little odd, I’m a lot reclusive, and I love creative stories and creative play. Gaming provides both affirming sandbox and stress outlet in many ways and my play spans most genres. Bringing together my love of games and my love of threat hunting is a natural move, of course; the DomainTools datasets and tooling make it easy, and the threat landscape makes it fruitful.
Gaming is no stranger to opportunities and infections. An early example was John Walker’s 1975 UNIVAC program ANIMAL, which involved a guessing game, while in the background reproducing itself in every directory to which the user playing the game could access. In 2000, the Pokemon virus wormed its way across the net by appealing to Pikachu fans. Hacks, aimbots, and other aids for many games as well as cracked versions often carried and carry trojans – Sophos began tracking the Baldr malware family as it began to target Apex Legends players in 2019, infecting them with infostealers. In December 2023, a popular modification for the game Slay The Spire called Downfall was compromised and used to execute a supply chain attack on those subscribed to the mod and install malware. Examples continue to pile up.
It is in this context we approach our current topic: the recent gaming threat landscape.
Discord
Any discussion of gaming-related threats must begin with Discord due to its centrality to gamers. Discord is a platform seeking to be a one-stop shop for communication and community – especially, but not solely, for gamers. Cryptocurrency-based communities and initiatives also began favoring Discord, leading to targeted attacks. It includes text chat, voice chat, image and file-sharing, and more. My learned colleague Joe St. Sauver covered Discord more thoroughly in a previous blog post, in addition to wider media coverage elsewhere, so instead let’s dive into what we can see in Iris.
You may have read my earlier post about IDNs (internationalized domain names) – these are domains that start with xn-- which tells a browser or other renderer to use Punycode to display different characters than the usual Unicode. This is especially necessary for non-English character sets or accented characters, and the overwhelming majority of usage is legitimate. But bad actors also like to use Punycode to impersonate other websites, also known as IDN Homoglyph Attacks.
One of the great things about Iris is that it translates keywords into IDNs to pick up on homoglyphs, so a keyword search for “Discord” detects domains like xn--discord-cza[.]com – which, in most contexts like HTML in websites and emails will instead display as discoírd[.]com. Notice the extra (accented) character, which is easily missed when bad actors use other tactics to add visual noise to what they’re displaying. Make it extra “busy” and users often miss incongruities.
xn--discord-cza[.]com
Registrar: OwnRegistrar
ISP: Hostinger
MX: titan[.]email
First seen: 2024-01-19
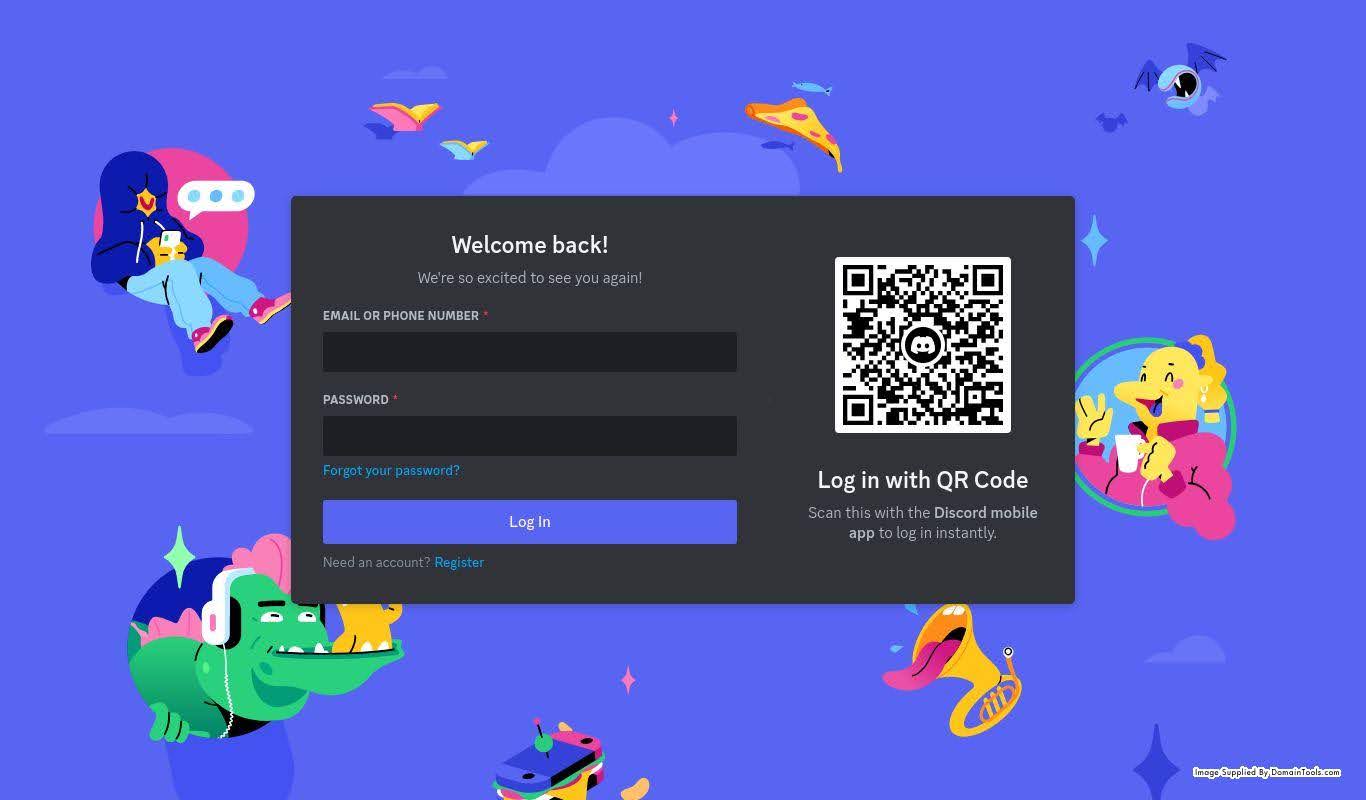
Iris also provides historical screenshots if available. We can see one for this domain on the day it was spun up:
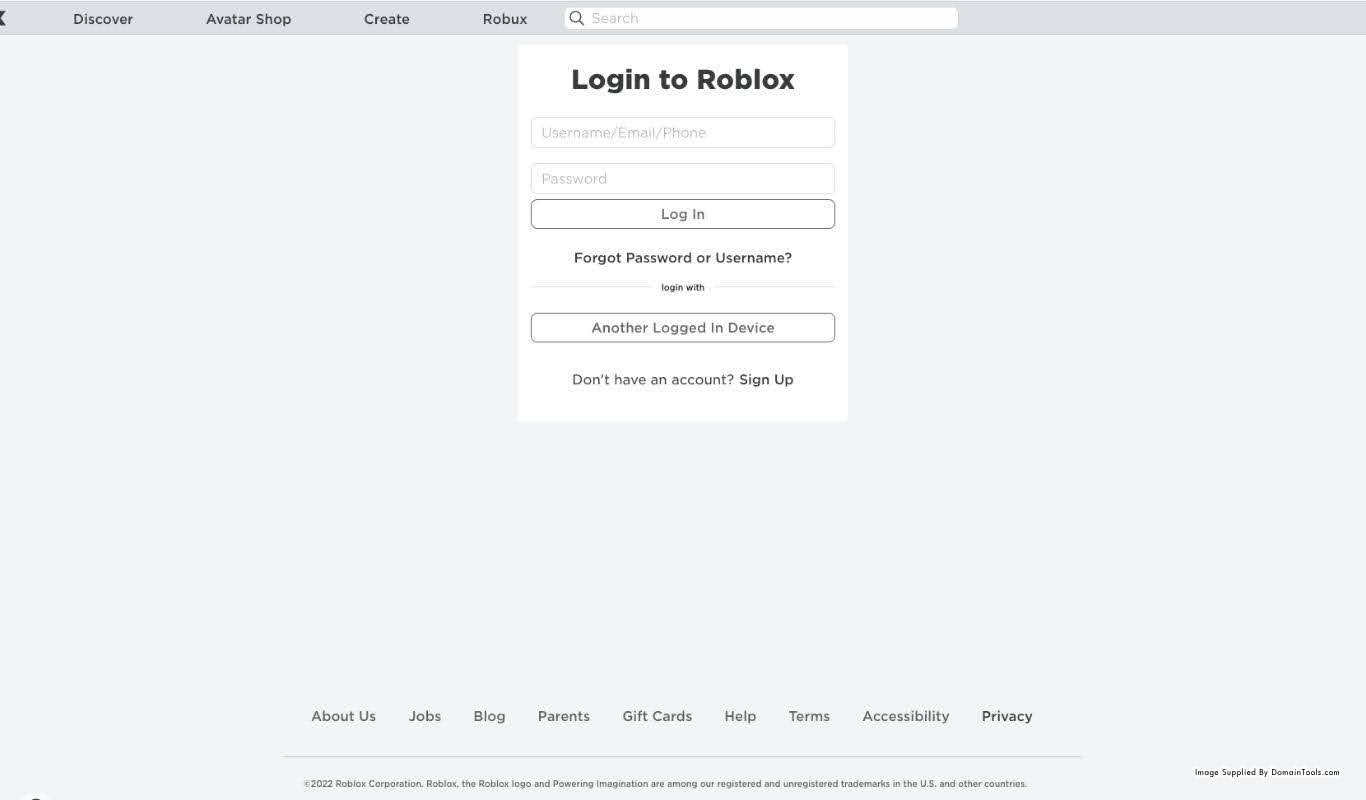
For reference, let us check the legitimate Discord platform login page:
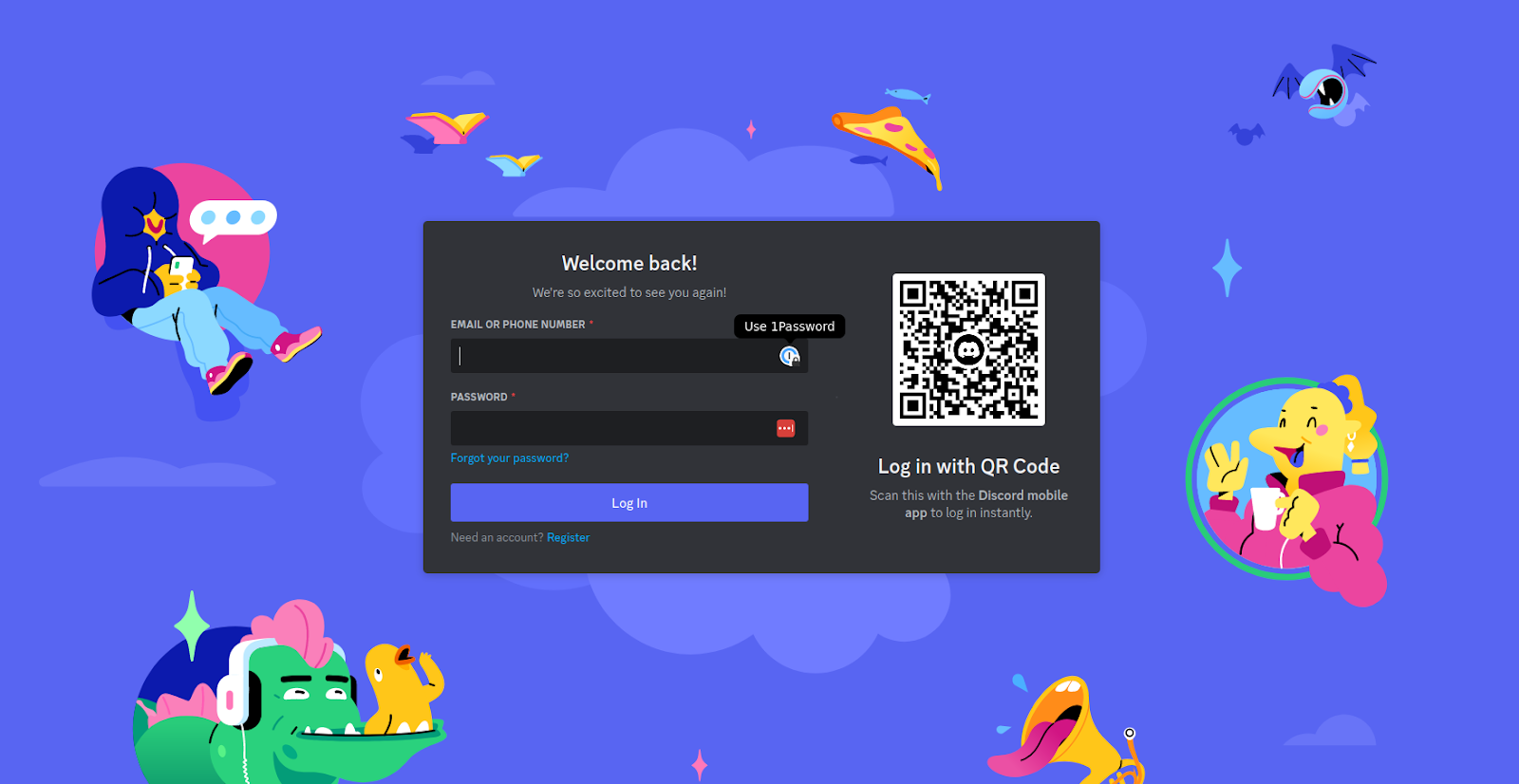
As we can see, the IDN Homoglyph domain is not only impersonating Discord’s URL, but its login page as well. There is no legitimate use case for this and a long history of malicious actors doing so – in this case we can reasonably infer that xn--discord-cza[.]com is likely attempting to phish Discord users’ account credentials, though other options are possible. Combining the knowledge of bad actor TTPs with obvious attempts to use brand imagery form the basis for an effective (though not guaranteed) takedown request by the brandholder or their designee.
Another IDN homoglyph targeting discord can be seen in xn--dscord-wva[.]com – which displays in most contexts as dìscord. Note the diacritical mark above the i in the latter. Both Iris Domain History and Farsight DNSDB Scout provide a longer history for this domain, as it’s been registered, taken down, re-registered, and taken down again multiple times since 2021. Passive DNS shows us that users have been trying to resolve this domain since at least 2019, in fact.
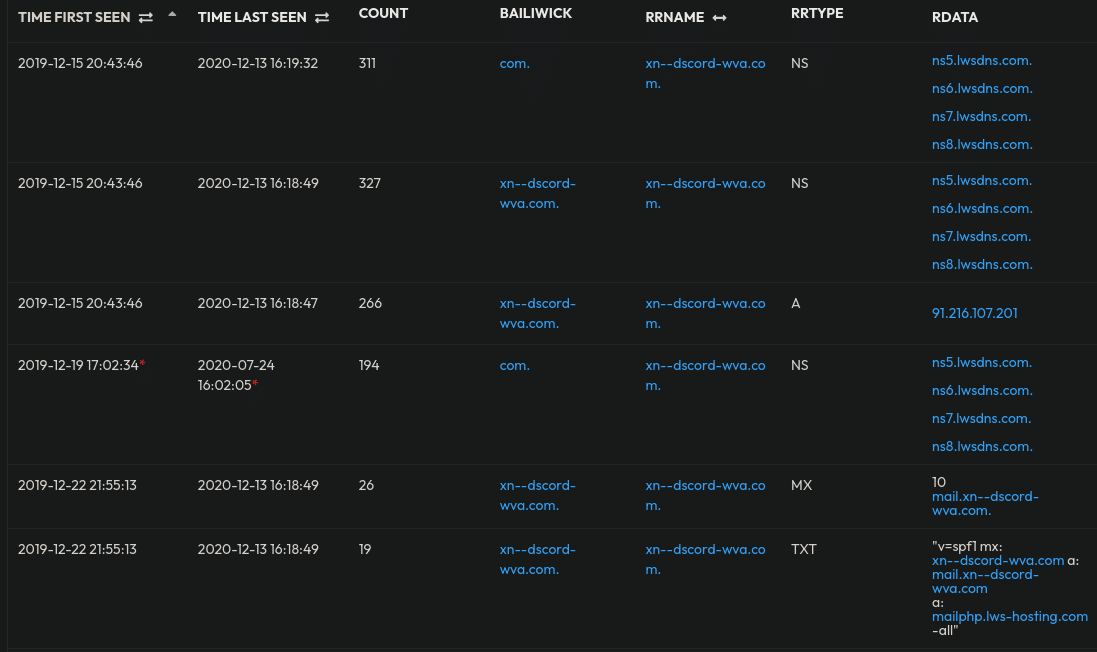
Combined with elements like whois, host, registrar, and more, doing direct hunting in passive DNS records can provide interesting insights. In this case, while this domain surfaced in 2019, it uses a distinctly different profile starting in 2022, indicating that either the actor in possession completely changed their typical profile or the domain came into the hands of a different threat actor. This is very, very common among both IDN and other non-IDN but suspicious domains (think here about domains with a particular service and then something like password-reset[.]tld or security-team[.]tld). Many registrars simply allow bad actors to move domains off their service rather than park them after termination, allowing an almost uninterrupted cycle of exploitation. Other registrars park the domains for a time and allow them to expire, whereupon bad actors monitoring expiring domains relevant to their targets re-register the domain.
In this case we can see that in 2022, xn--dscord-wva[.]com moved to Epik registration and nameservers. Epik is known as a refuge for extremist websites and other sites that the rest of the industry refuses to do business with, according to WIRED and many other sources. The domain bounced around several hosting services before going inactive in January 2024. Two months later the domain re-emerged, still under Epik registration but protected by Cloudflare nameservers.
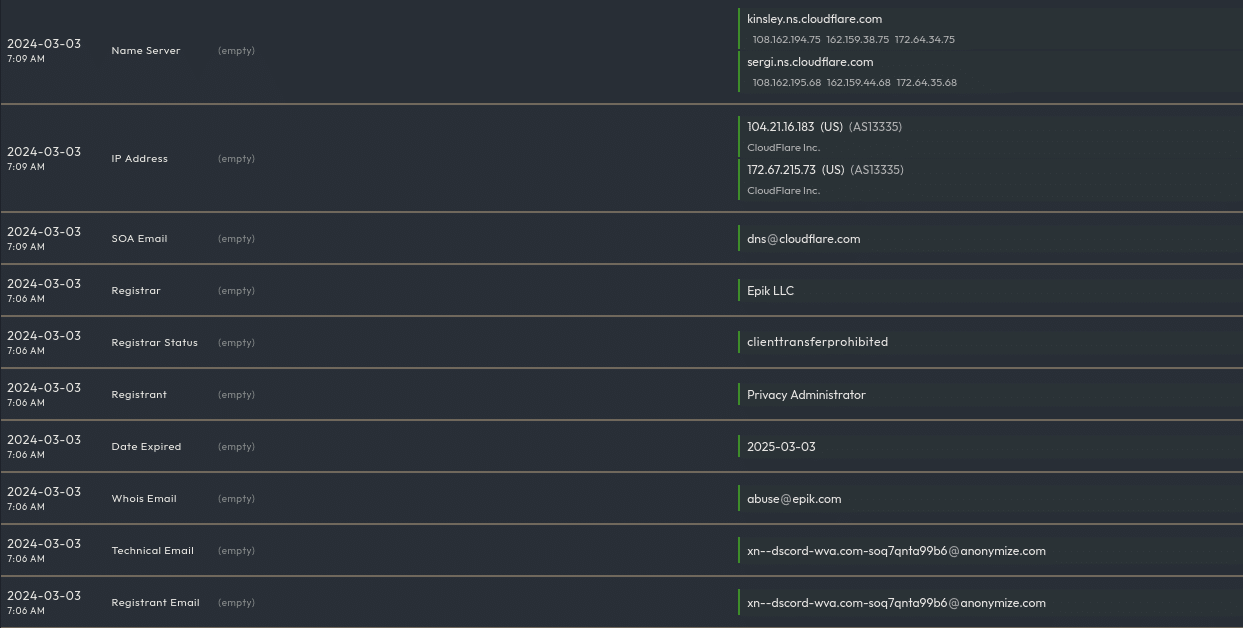
Given the two months of activity and shift to Cloudflare to obfuscate originating servers, this may be indicative of a takedown on its previous hosting, but is not conclusive. The shift of an IDN homoglyph domain to resources that make takedowns significantly harder (thanks, Cloudflare) dovetails with that inference.
Of course, Discord is far from alone as a target.
Roblox
Let’s take a look at Roblox, the online game platform boasting 164 million active users, including “over half of US kids under age 16” according to The Verge. Roblox utilizes an in-game currency purchasable with real dollars, making it a profitable target for bad actors with no scruples about targeting and devastating children. A quick check shows recent activity for xn--robox-vsa[.]com – which displays in most contexts as robìox[.]com, and has been in play since 2022-08-20. Its landing page around that time tells the story:
For another example, observe wwwwww-roblox[.]com – repeated w characters preceding a brand name often indicate an attempted typosquat, attempted adfraud, or attempted phishing. This domain has been in play since 2022-08-22
hey, wait a sec – that date sounds familiar!
Maybe because the example IDN homoglyph targeting Discord above – xn--robox-vsa[.]com – originated 2022-08-20! Two days before! And sure enough when we look at a historical screenshot in Iris, we see a Discord tie-in:
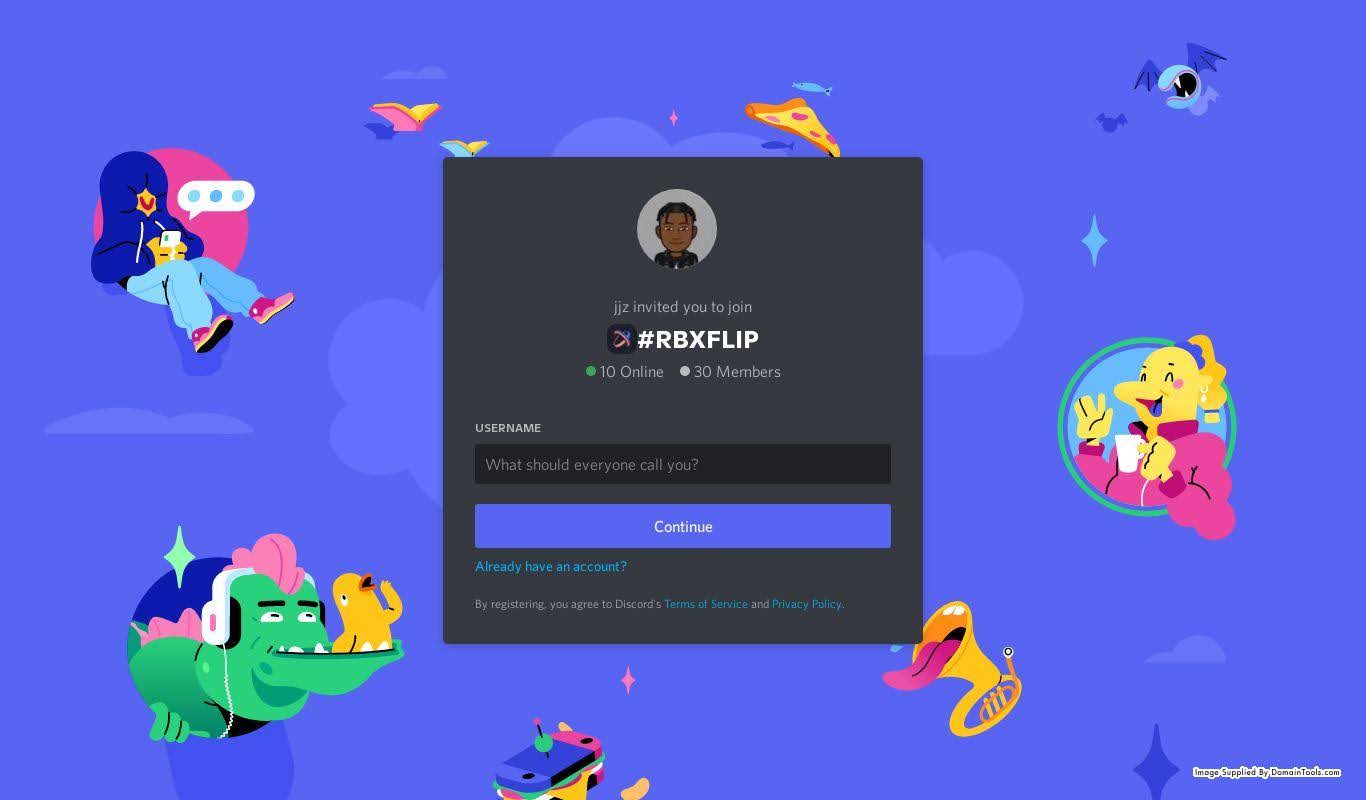
It may be that this site originally attempted to lure unsuspecting users to a Discord server where less visible attempts were made to defraud them (a known and common tactic), or it may be that once a username was input the next page attempted to phish credentials directly. The timeline and targeting parallels between this domain and the above IDN, while not conclusive, are interesting in the sense that they may indicate behavior from the same or coordinated actors.
Attempting to navigate there now shows a phishing warning, but allows you to click through. Cloudflare helpfully informs you that its protection is still up and running for its customer, the site-owner; but the customer’s endpoint server is not responding.
Very kind of them.
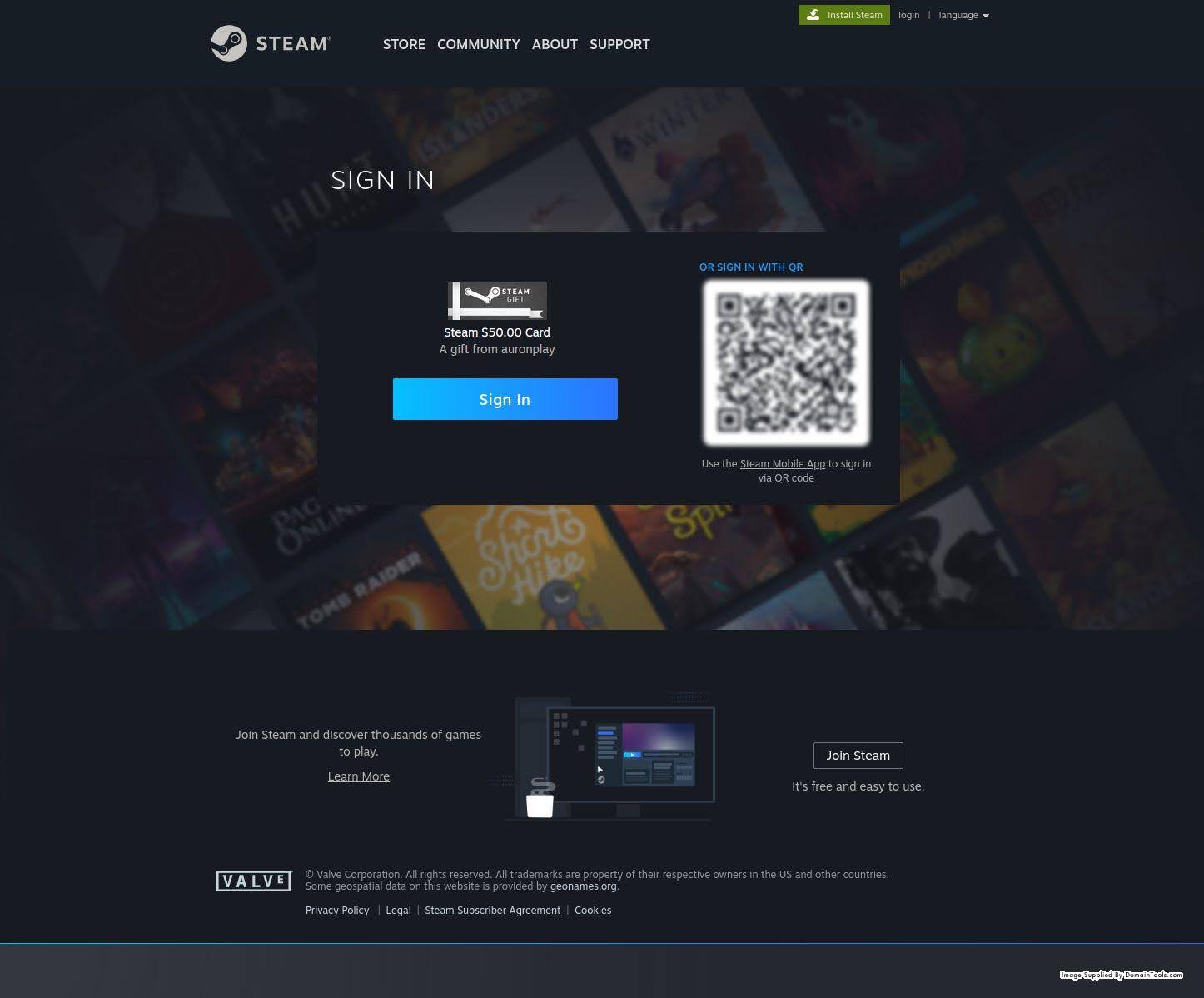
Steam
Communications platforms, games, what about game distribution platforms? Of course the dominant one here is Steam, often targeted by threat actors. One example is newly seen as of 2024-03-20, the day that I’m writing this article. Observe the domain steamcommunioy[.]com – an attempt to spoof steamcommunity[.]com, one of Steam’s official sites.
steamcommunioy[.]com
Registrar: Reg[.]ru
ISP: Cloudflare
First seen: 2024-03-20
The title of the website is “Gift Activation” and, sure enough, the landing page impersonates the Steam website and promises sweet rewards if you but sign in with your Steam credentials:
Pivoting off whois data for the above domain surfaces steamcommunimy[.]com – which shows the same landing page and domain profile, presumably for the same malicious purposes.
steamcommunimy[.]com
Registrar: Reg[.]ru
ISP: Cloudflare
First seen: 2024-03-20
Conclusion
Video gaming has been targeted by bad actors for over fifty years, since UNIVAC days, and continues to be a fruitful and active landscape for exploitation. In the examples above we have observed multiple recent examples of bad actors targeting the video gaming landscape for phishing and fraud, in most cases directly targeting children even less capable of detecting possible threats. Putting these examples together has been the product of a single morning in March 2024, between multiple meetings; a benefit of having DomainTools Iris Detect and Investigate as well as Farsight DNSDB Scout. Companies and institutions seeking to protect their brand as well as their customer base can do so much more effectively with these tools in their tool chest, arming their defenders to fight real-time threats with deep real-time and historical data.
As for me, I’ll keep gaming, and keep hunting. I’ll keep putting pieces together and tracking down leads, and keep delighting in it. The books I keep by my desk may have changed – they may not be the World Almanac anymore, but reading and learning will continue forevermore for me, I hope.
There may be one lingering mystery for you here, one last loose end to tie up before we close out this post. Where in the world is Carmen Sandiego?
She’s spent the time since by becoming a much more complex character – driven by a moral code, and her love of a good challenge. And as a gamer, a threat hunter, and a lock picker, I can surely respect that. So Carmen Sandiego has a place of honor right by my desk these days as I work, and I think she enjoys these challenges too.