Paul Security Weekly #617 on DomainTools Iris
Investigating Phishing Emails and Domains Using DomainTools Iris – Security Weekly
Investigation Time!
You may be sitting at work early in the morning, enjoying your coffee and the peace and quiet that comes along with being the first one in the office. Like most, the first thing you do is check some emails (not all of it, just some, because there’s a lot of email!). You’ve become pretty good at spotting phishing emails, even earned a few t-shirts and beer koozies along the way from the corporate security awareness training program. One of the first emails you spot is claiming to be from American Express, a company you hold a credit card with. The subject reads “Irregular Activity” and for a brief moment you panic and think someone has stolen your credit card. At first glance the email was somewhat believable as you have a couple of corporate Amex cards, you’ve had fraudulent charges in the past, and the cards are stored in several online accounts for automatic payment (leaving you vulnerable to fraud and irregular activity). Then, a voice speaks in a giant echoing tone: “Remember your training”. You snap out of panic mode, remembering your preparation, and begin to investigate the following email:
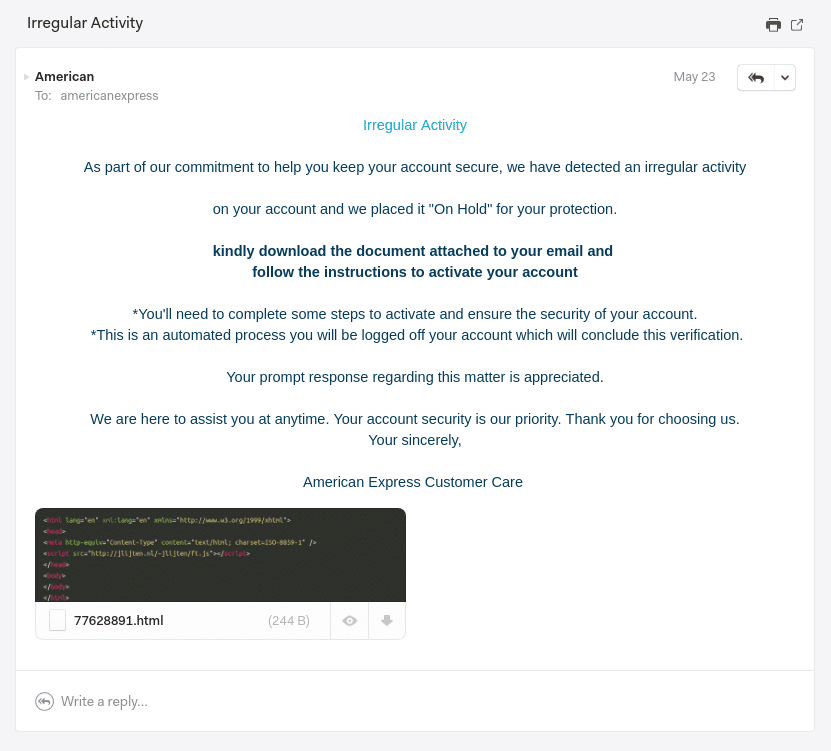
As you sip your coffee and inspect the details of the email, you notice a few things that are suspicious:
- The sender “American Express is strange, as the domain does not contain a reference to American Express in any way.
- The email’s grammar is a hot mess.
- The sender is asking you download an HTML file to reach the page that will activate your account (even though Sir Tim Berners-Lee invented the World Wide Web in 1989).
Based on these facts, you decide to warn your local security team of a potential phishing/scam email.
Basic Forensics
“Whew, thank goodness for end user awareness training” I thought to myself sarcastically when I received this email. The sarcasm originates from years of experience, knowing that for every 10 users that report a phishing scam, there may be at least one that falls for it and causes a security incident that, likely on a Friday, in the late afternoon. In any case, I decided to look into this email as I am a security nerd and intrigued by the HTML attachment as it is an indication that this phishing scam may not be all that sophisticated.
Let’s take a look at the attached HTML:

Upon quick review, its very basic HTML with an embedded script that is pulling down JavaScript from a web site. If you’re keeping score at home, just looking at the email and the attachment, I have two domains to investigate:
- rugjam.com
- jlijten.nl
So using the command line tool “wget” I pull down the JavaScript (I don’t want to run it in my web browser and my other option is to fire up my forensics environment, but I am lazy and just use wget). The resulting JavaScript file comes down and present me with some math:

Some “fancy” JavaScript eh? It’s using the JavaScript Math function to obfuscate the actual code. Kinda lame, maybe a bit neat, but highly annoying. Not wanting to load this in the browser (yea, I am that lazy!) I installed the node package locally. Node can execute JavaScript on the command line and save me the hassle, and risk, of opening it with a web browser. I replaced the “document.write” function with “console.log” so I could see the results in the terminal. Since we are not in a web browser we don’t have access to the document object, but we do have access to the console object. I executed the JavaScript using the following command:
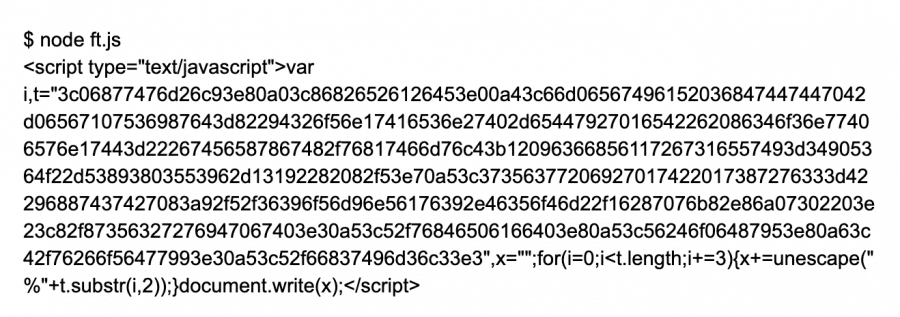
This uncovers even more JavaScript. Let’s do the same thing, replacing document.write with console.log, then running node:

Here we go again! This time the JavaScript unpacks and provides us with HTML that is downloading more JavaScript, this time from a different site. Now we also have another domain to investigate and another script to download, which when we apply the same process, looks like this:

I think we all know what to do now! Lets run this script through the same process:

We now have a full HTML website, which is a completely fraudulent American Express website created to collect the user’s Amex online account credentials. While the website was setup to look just like an American Express site (even using some JavaScript embeds from the real Amex site) the POST request is sending the user’s login to another site:

Now have another domain to investigate!
DomainTools Iris
I took the following list of domains derived from this exercise and plugged them into Iris (you can just copy and paste the entire list into the Iris search bar):
- rugjam.com
- jlijten.nl
- Comnac.com
- heilgeist64.de
DomainTools Iris makes it really easy to quickly investigate a list of domains. My first path was to review the list and look for any Guided Pivots.
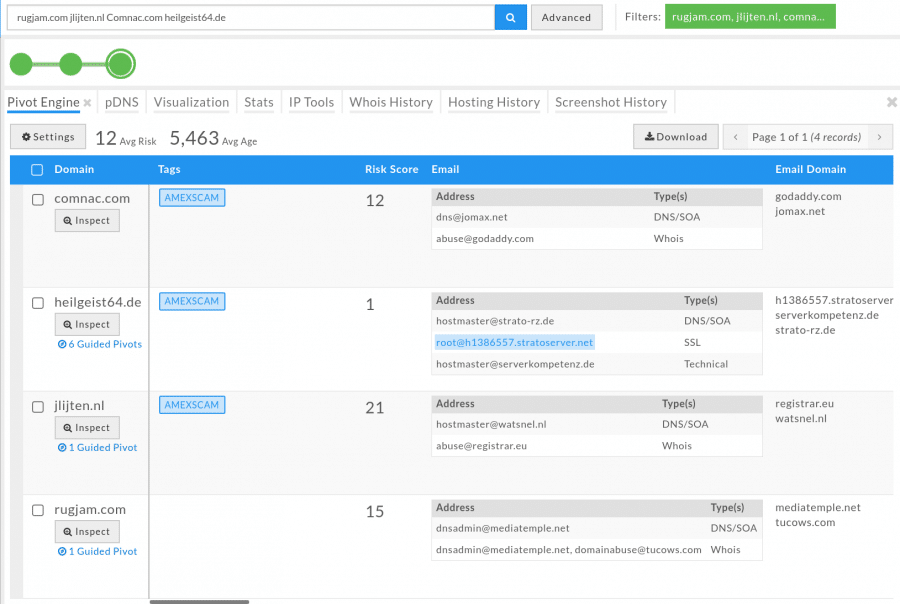
Iris provides you with the ability to include other related domains and IP addresses into your investigation by flagging them in the Guided Pivots. Below I noticed that one of the domains shares the same IP address as a bunch of other domains:
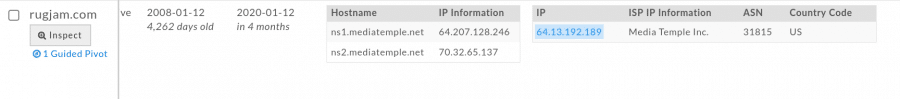
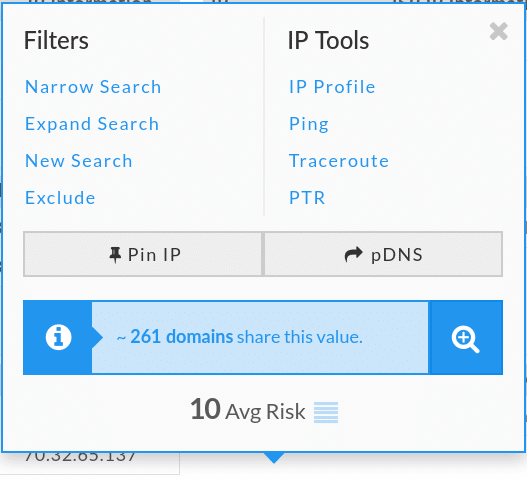
I clicked “expand search”, which adds all 261 domains to the list, then I sorted by Risk Score:
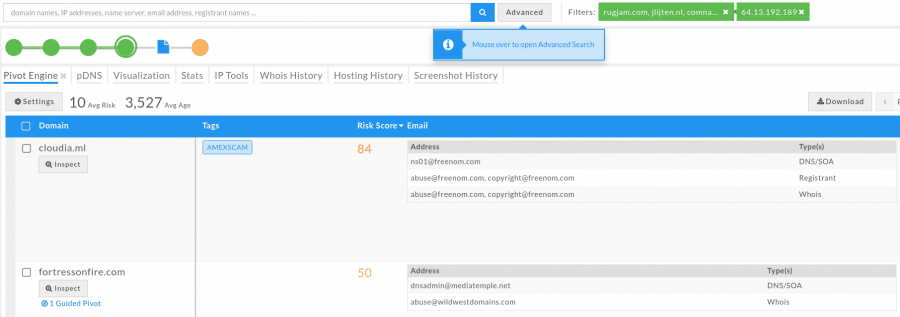
Looks like this domain could have some bad neighbors. This could also be an indication of a future phishing attempt, so I could go ahead and block all of these domains, or the IP address, at least for a specific time period to prevent any further phishing scam attempts. It also occurred to me that the domains used in the phishing scam may have been hacked, in a number of different ways, and put together by the same attacker(s) to run the phishing scam. I reviewed some of the passive DNS information and revealed similar results for all domains: They all had some type of mail, ftp and other services running on subdomains:
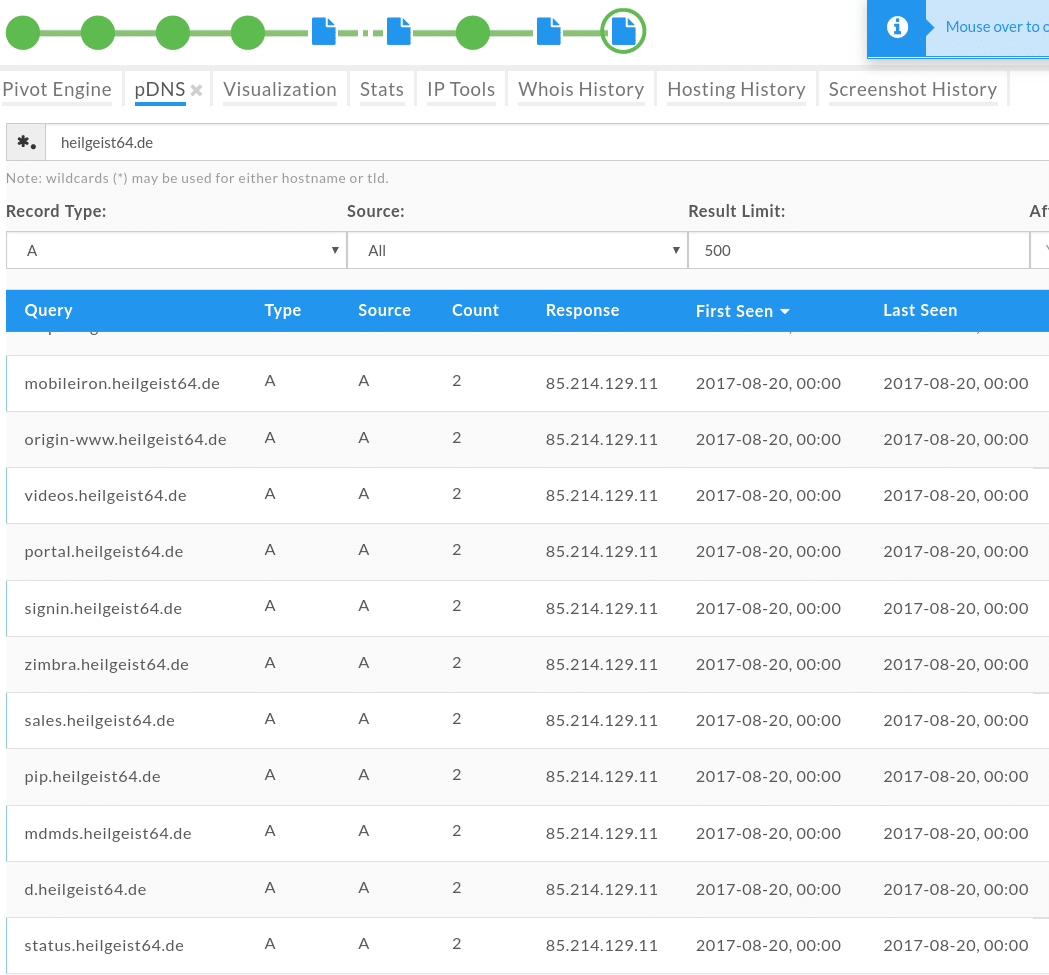
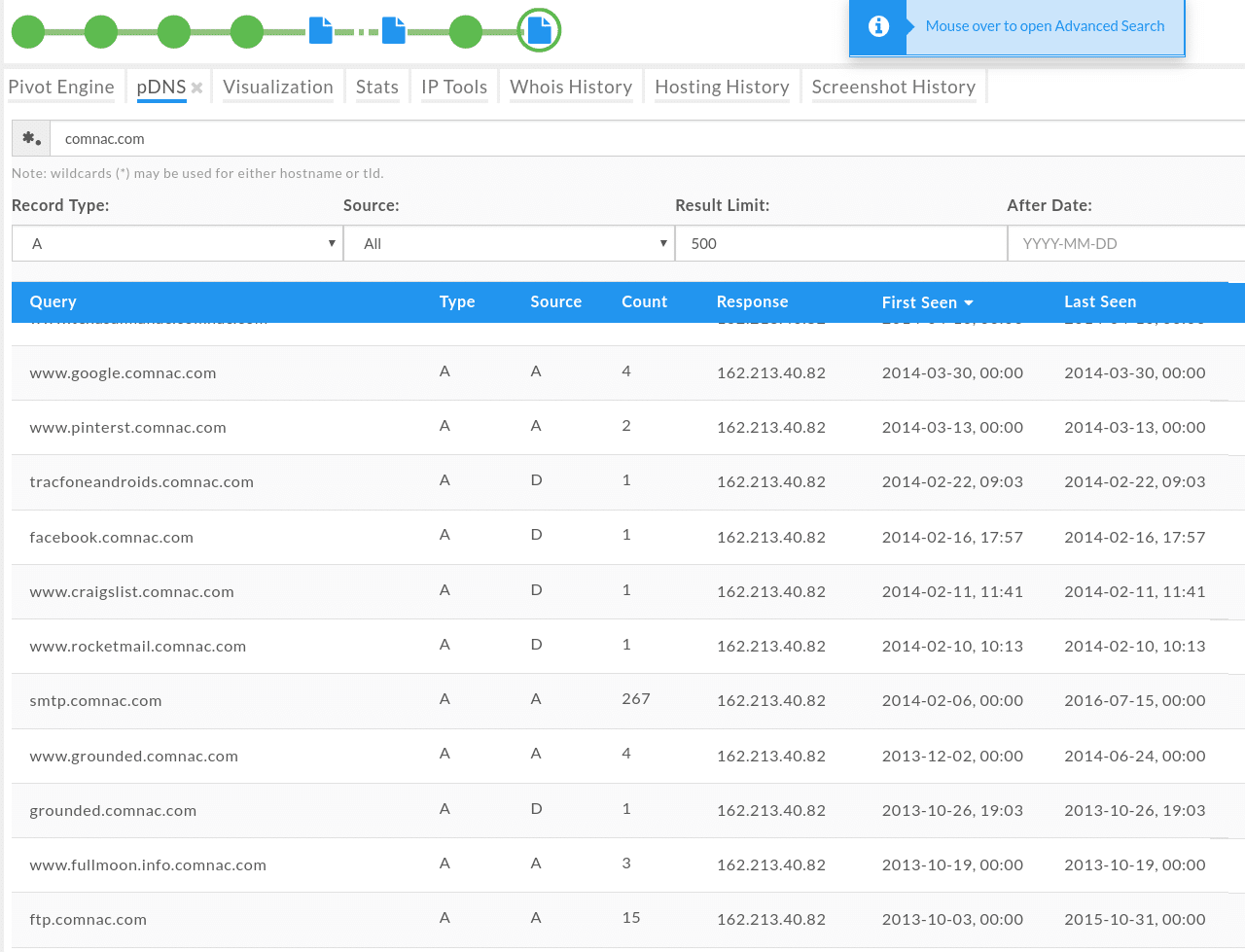
The above result was also interesting as the subdomains contained names of other popular domains. This was a more obvious indicator that these domains do not live in a nice neighborhood.
I also checked with VirusTotal to see what it knew about some of the domains involved, turns out they have been flagged as malicious:
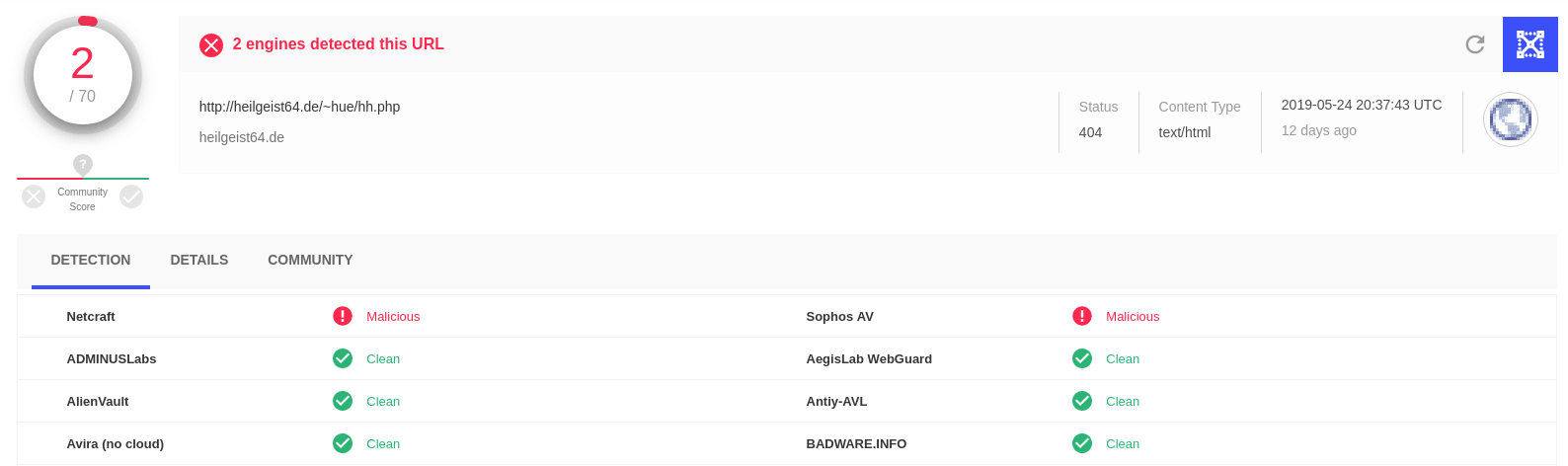
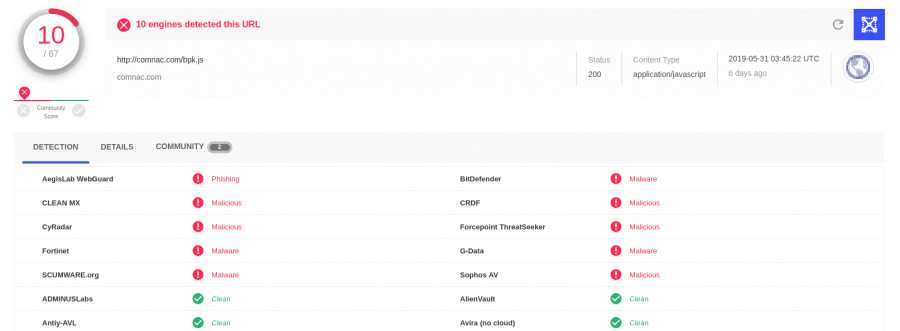
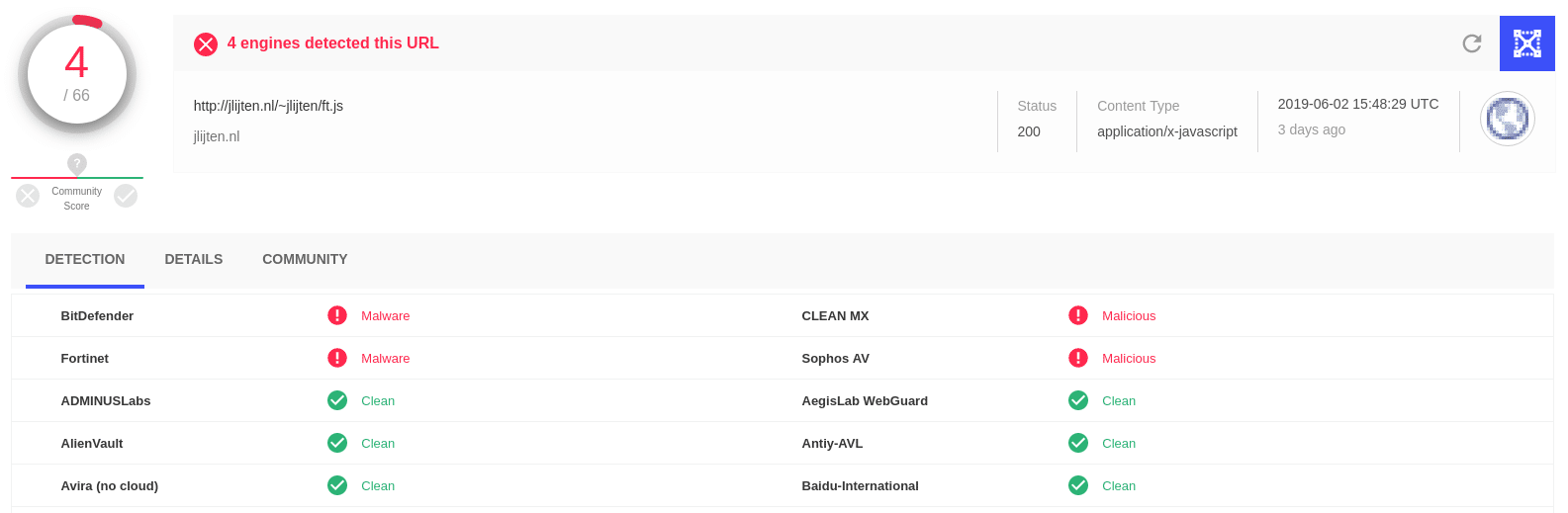
One user even commented that they observed this domain in a phishing scam:
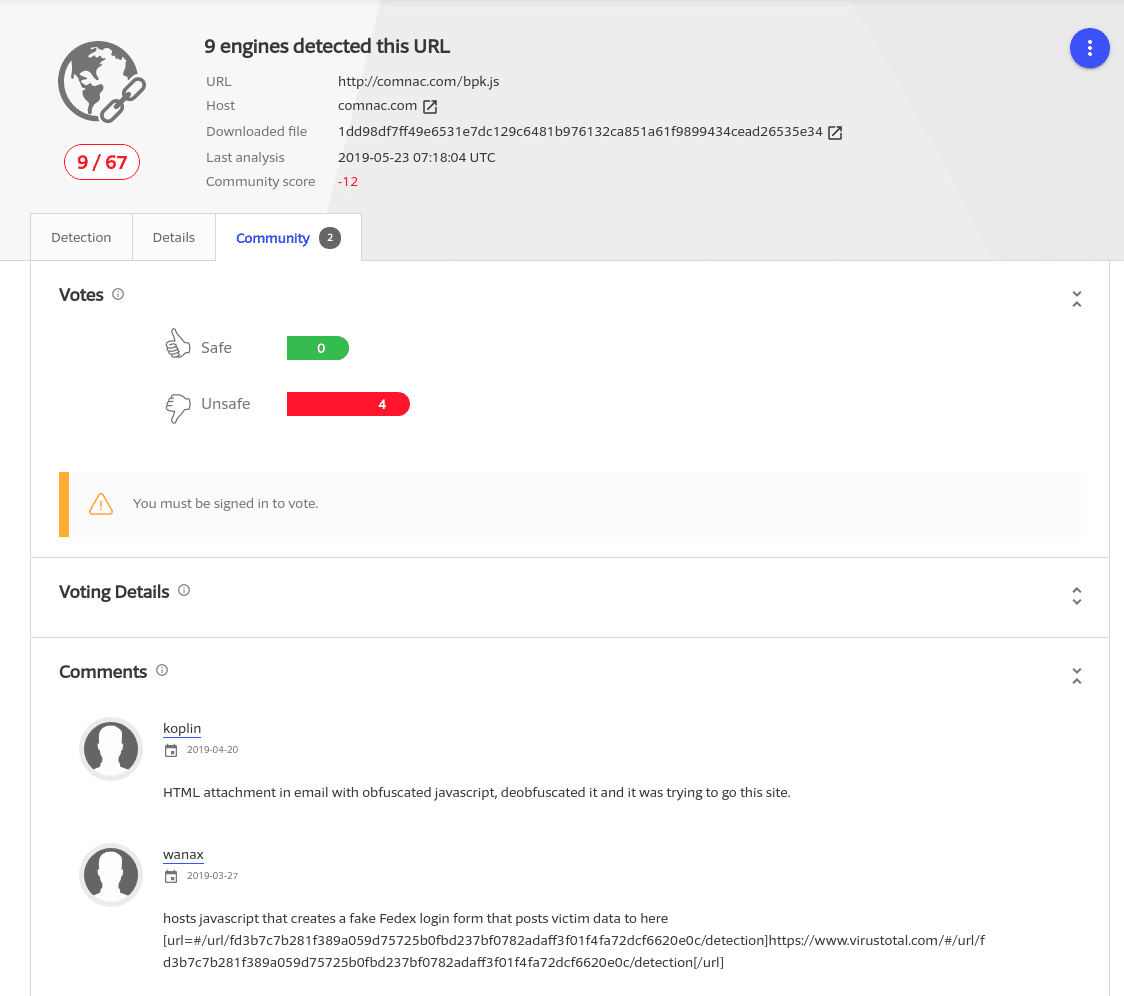
Don’t Judge a Book By It’s Risk Score
My actions were simple, I blocked the domains and IP addresses associated with this phishing scam. Even though the Domain Risk Scores were not high, my investigation revealed that the domains were sharing some of the same infrastructure (IP address), not hosting any websites that appeared to be used by our users, and contained several services that are likely targeted by attackers to gain control of the systems.





