You Must Pay the Toll Troll
Share this entry
On April 12, the Federal Bureau of Investigation (FBI) issued a Public Service Announcement (PSA) warning the public of an on-going toll collection service SMS phishing (smishing) campaign. According to the PSA, the FBI’s Internet Crime Complaint Center (IC3) has received over 2,000 complaints reporting smishing texts representing road toll collection service from at least three states.
In addition to the FBI’s PSA, the Pennsylvania State Police issued similar warnings via X (formerly Twitter), including an example of a smishing lure, with a domain, that was sent to victims.
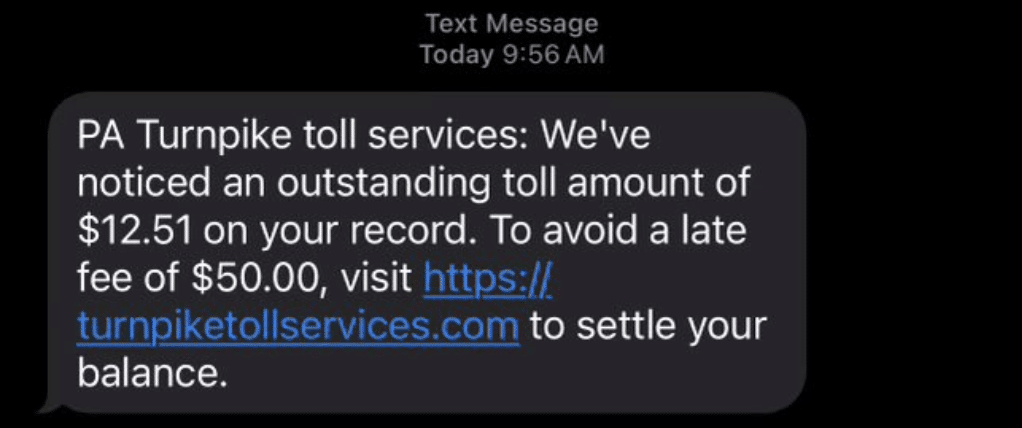
The lure is relatively straightforward and effective. Like many financial scams, the threat actor creates a sense of urgency by “warning” victims they will incur a $50 late fee if they don’t pay the relatively small charge of $12.51 very soon. If convinced, the false sense of urgency causes victims to act impulsively and with less attention to detail and logic.
Our research into these domains showed a straightforward campaign that is opportunistic and not targeted. The threat actor’s primary objective is to harvest payment card information with a secondary objective of gathering their victims’ personal information.
The sophistication of the campaign is considered relatively low. The websites do not perform any input validation checks or any other data quality controls to ensure the user input is legitimate.
Despite the campaign’s low level of sophistication, it may be especially convincing for individuals who have recently traveled to, or through, these states in a rented car. Many states have implemented toll-by-mail policies and some travelers may assume the car rental company provided the toll collection authority with their contact information.
At DomainTools, we take malicious domains pretty seriously and decided we wanted to dig a little deeper into this campaign to:
- See how many other domains associated with this campaign we could identify.
- Understand the threat actors’ objective and the level of sophistication behind this activity.
Finding Domains Associated in a Smishing Campaign
We started by searching the domain turnpiketollservices[.]com in our Iris Investigate platform. From this search, we were able to gather some key information about this domain:
- Create Date: Apr 7, 2024
- Registrar: ERANET INTERNATIONAL LIMITED
- DNS Provider: Cloudflare
- ISP Provider: Cloudflare
- Registrant Country: Peru (PE)
The infrastructure used by the domain is fairly generic and frequently used for shared hosting, thus we did not immediately identify any direct pivot points, based on infrastructure, to identify other domains associated with this campaign.
Instead, we focused on the domain’s naming structure to search for additional domains. We queried Iris Investigate for domains first seen within the last three months that contain the terms “toll” and “service” or “toll” and “turnpike.” This returned 73 unique domains, 60 of which were identified as having a high probability of being related to the original domain shared by the Pennsylvania State Police.
| Domain | Created | Domain | Created |
|---|---|---|---|
| myezpasstollservices.com | 4/25/24 | turnpiketollsservices.com | 4/7/24 |
| ezpasstollsservices.com | 4/25/24 | turpiketollservices.com | 4/7/24 |
| ezpasstollservices.com | 4/25/24 | turnpiketollservice.com | 4/7/24 |
| ncsun-spasstollservices.com | 4/24/24 | paturnpiketollservices.com | 4/7/24 |
| ncsunspasstollservice.com | 4/24/24 | turnpiketollservices.com | 4/7/24 |
| georgiasunpasstollservice.com | 4/24/24 | itollswayservices.com | 4/5/24 |
| mysunpasstollsservices.com | 4/24/24 | iltollswayservices.com | 4/4/24 |
| paysunpasstollservices.com | 4/24/24 | illinoistollservices.com | 4/3/24 |
| ctrtollservice.com | 4/22/24 | iltollwayservice.com | 3/28/24 |
| georgiasunpasstollservices.com | 4/21/24 | itollwayservice.com | 3/26/24 |
| gasunpasstollservices.com | 4/20/24 | itollwayservices.com | 3/26/24 |
| ncsunpasstollservices.com | 4/20/24 | iltollwayservices.com | 3/26/24 |
| ncsunspasstollservices.com | 4/19/24 | wwwtollwayservices.com | 3/24/24 |
| txtollservices.com | 4/16/24 | tollwaysservices.com | 3/24/24 |
| ctrtollservices.com | 4/16/24 | tollwayservice.com | 3/24/24 |
| texastollservices.com | 4/16/24 | tollwayservices.com | 3/24/24 |
| tollwayservices.co | 4/15/24 | myetoll-service.xyz | 3/23/24 |
| sunpassservicestoll.com | 4/16/24 | myetoll-service.top | 3/23/24 |
| sunpasstollsservices.com | 4/16/24 | myetoll-service.life | 3/23/24 |
| servicessunpasstoll.com | 4/16/24 | myetoll-service.info | 3/23/24 |
| sunpasstollservice.com | 4/15/24 | myetoll-service.com | 3/23/24 |
| mysunpasstollservices.com | 4/15/24 | njtollservices.com | 3/21/24 |
| sunpasstollservices.com | 4/14/24 | toll-road-service.link | 3/17/23 |
| floridasunpasstollservices.com | 4/14/24 | nytollsservice.com | 3/11/24 |
| flsunpasstollservices.com | 4/14/24 | nytollservices.co | 3/5/24 |
| turnpikeservicestolls.com | 4/13/24 | nytollservice.com | 3/2/24 |
| nytollsservices.com | 4/9/24 | nytollservices.com | 3/1/24 |
| myturnpiketollservice.com | 4/9/24 | ie-tolls-service.info | 2/8/24 |
| turnpiketollservices.co | 4/7/24 | onlinetollfreeservice.xyz | 2/6/24 |
| myturnpiketollservices.com | 4/8/24 | ie-toll-services.info | 2/3/24 |
The results of this query show the campaign likely started in early-to-mid February with the threat actors representing themselves as a toll collection authority for the State of New York. The campaign picked up its cadence in mid-March when it began using New Jersey Turnpike-themed domains and later expanded its targeting to Pennsylvania, Florida, and other states.
How Threat Actors Gather Personal Information
We performed some reconnaissance on these newly identified domains. Our initial attempt to navigate to the websites using a traditional web browser was unsuccessful. The threat actor appeared to be using a browser filter and the phishing page only loads for mobile browsers, which makes sense as this is a smishing campaign.
Using a secure mobile browser, we navigated to sunpasstollservice[.]com which first prompted us to complete a ReCaptcha verification filter then loaded a landing page designed to look like a legitimate bill payment page used by SunPass, Florida’s electronic toll collection system. The landing page prompts victims to enter their phone number and date of birth, giving the victim a false sense of verification legitimacy.
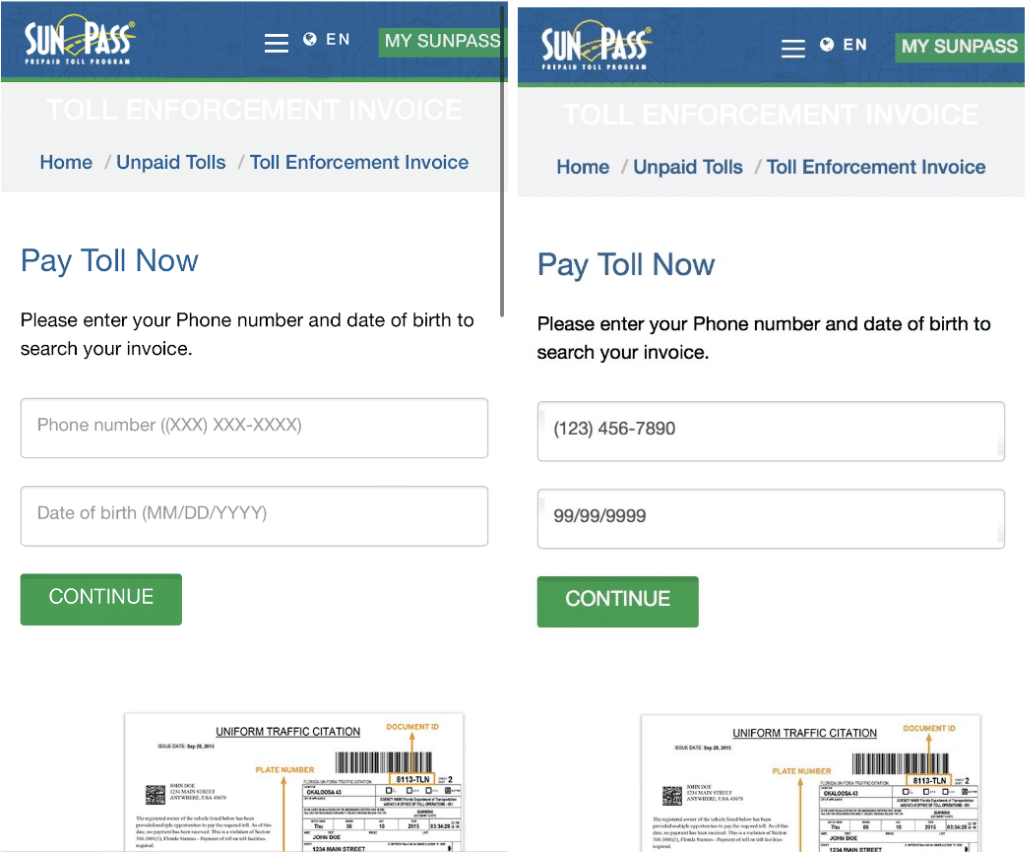
Interestingly enough, the threat actor also neglected to set up any input validation to ensure the phone number entered matches a phone number that actually received one of the smishing messages or that you even entered a valid date for the date of birth field.
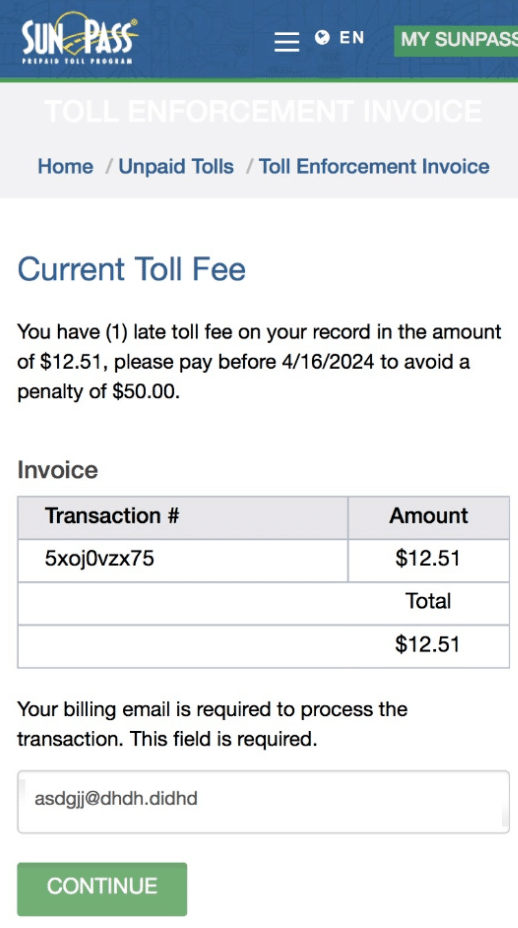
After a victim enters their phone number and date of birth they are taken to a page showing their “Current Toll Fee” of $12.51 and directing them to enter their email address. The transaction number and amount stayed identical for all of the websites we investigated indicating this is a relatively low sophistication campaign.
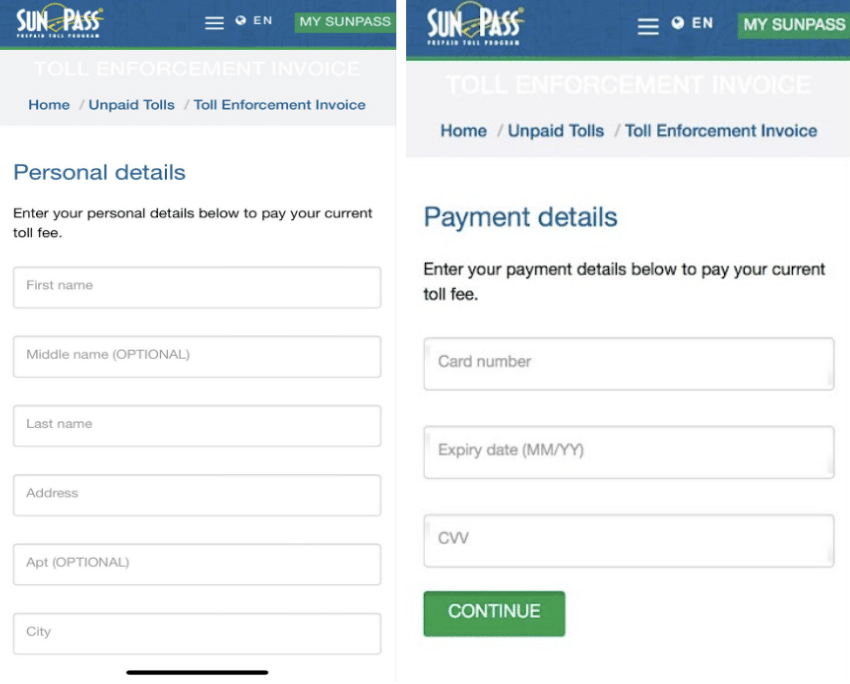
After entering their email and pressing continue, victims are directed to a third page instructing them to enter their name and address followed by a fourth page instructing victims to enter their credit card information.
Once the victim has entered their payment info and clicked “continue” a false “processing” page is briefly loaded before displaying a payment error message.

The page does not prompt victims to re-enter their payment info and instead refreshes and redirects to the legitimate website of the toll collection authority the fake website represented itself as.

The threat actor’s decision to give the victim a “payment error” message and redirect them to the legitimate site is interesting as the two websites are not identical and could tip some victims off to the fact that the message was a scam.
Conclusion
This campaign and the creation of new domains to support it does not appear to be slowing down any time soon. On April 23rd and 24th, DomainTools identified 16 newly created domains containing the terms “toll” and “service.” Seven of the domains were likely registered with malicious intent, however it appears that state toll collection authorities are fighting back. The nine newly created domains that we believe were not registered with malicious intent appear to have been registered by a legitimate state toll collection authority. Although proactively registering domains may seem like a solution, doing so is costly, time consuming, and likely to have limited success. Threat actors are, if nothing else, resilient and willing to change or adapt their tactics to continue a lucrative endeavor.
Although the primary victims of this campaign are individual consumers, the campaign also has downstream impacts for credit card companies and banks who will likely absorb the costs of any fraudulent transactions that result from credit cards that are compromised by this campaign.
Recommendations
Toll collection authorities and law enforcement agencies handling these cases should report domains associated with this campaign to phishing protection teams like Google’s Safe Browsing Team. If Google determines that a site violates Google’s policies, they will update the domain’s status in their Transparency Report and share the URL and its status with other third parties that can also choose to limit traffic to the malicious domain.
Update: June 21, 2024
As of Friday, June 21, 2024, this campaign appears to remain active. We identified a second cluster of toll collection-themed domains (shared below). Although the second cluster of domains are likely being used to gather payment card information, differences in the domain’s naming conventions and registration patterns suggests the campaigns are being operated by separate threat actors
- tollroadtrust[.]com
- intollroadacc219[.]com
- newyorktollroadtrust1[.]com
- intollroadtrust[.]com
- mnezpasstrust[.]com
- nytollroadezpass1[.]com
- tollnyezpassweb[.]com
- nyserviceezpass[.]com
- web-nyezpass1[.]com
- nytrust-ezpassweb[.]com
- newyorkacc-ezpass[.]com
- nyusezpasweb[.]com







