Coming up this week on Breaking Badness. Today we discuss: Detecting Malware is as Easy as Pi, Phishing Emails Cause a Cloud of Suspicion, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Detecting Malware is as Easy as Pi
- This sweet, sweet fruit confection (known as a Raspberry Pi) is basically the #1 giveaway prize for the cool organizations. It’s a small computer, about the size of a traditional PC mouse, that runs a flavor of Linux called Raspbian natively (but can run other OS’s if you choose). It’s extremely flexible because it’s a really full-featured computer. Not the fastest thing on the block, but very capable. And it’s super inexpensive as well. So people have applied them to all kinds of applications, from home fun things like media servers to huge clusters of Pis to get some real power, to sci-fi level malware sniffers.
A poem on IoT
<Shall I compare IoT to a bummer day?
Thou art computer and yet also not;
Thy vendors think but little of defense,
Yet throw thee to th’Internet’s wiles and foes.
To firewall or not to firewall
Tis never much a question with these things
And so defenders look with no surprise
At the large misery IoT brings
A poem on France’s Research Institute of Computer Science and Random Systems discovery
Truly, it wondereth the eye to behold this object,
A malware scanner on the humble Pi
Which doth use the RF waves
And an oscilloscope equipped with probes
To hearken to the songs of malware’s voice
For the infected sing, though they know not
But the malPi heareth all that they tell
And compareth the airs of the pwnd
With all the joyous melodies of those not
And rendereth judgment on the state of the probed
All things computer make these RF waves
And tell their truth to those with ears to hear
These French have wrought a marvel on the Pi
The truth to find, a new mode of DFIR
- The claim on the accuracy of this system is that it, to quote, “predicted three generic and one benign malware class with an accuracy as high as 99.82%.” So it seems like as far as clever stunts go, this one is pretty impressive. If they continue this research the really interesting thing from my perspective is to see how fine-grained they can get in terms of detecting specific malware families and variants. But even just being able to determine in a non-intrusive way which devices are infected is quite interesting and could have some real-world applications if it’s proven out.
- The claim of the authors is that there’s no way for malware authors to evade this kind of detection. I’m not so sure about that. Admittedly, I’ve not read the full research paper behind these findings, so I’m going out on a bit of a limb here, but I would expect that by manipulating things like timing of various system calls in a random way, it might be possible to mask the RF signature of a given piece of code. Are all the ransomware gangs going to drop everything and start looking into how to do this? Not at all, at least not any time soon. They’d only have reason to if this technology became widely adopted, and there are a lot of issues with that.
- I see two challenges here when it comes to practical application. One is running this technology through the usual processes of additional research, and tons of testing, and figuring out the intellectual property and rights and all that. But the other, which I think is the bigger challenge, is scale. You have to physically probe the devices (I don’t mean touching them, but you have to have this scanner close enough to them to pick up the RF. Those waves don’t travel far because the actual level of energy in them is very tiny. So either you have to have humans or robots or something cruising around the protected environment running these scans, or you have to have some sort of network of the devices, or at least antennas for them, over enough of the protected environment to get coverage. Can you imagine trying to do this if your organization has hundreds of thousands of devices?
- But – for probing compromised IoT devices in the field, where the numbers of devices are reasonable, and could be part of a maintenance workflow or something, maybe there’s something real to be done with this. We’ll have to see. It’s quite interesting.
Phishing Emails Cause a Cloud of Suspicion
- Adobe launched their “creative cloud” back in 2013 in their shift from perpetual licensing over to a Software as a Service model. On the user side it allows for file synching across devices and it operates as a hub for grabbing their various products.
- These attacks were discovered and reported on by the folks over at Avanan (owned by Checkpoint) and occurred in December. They picked up attackers setting up Adobe Cloud accounts to send PDFs to other users that then redirects them to a credential harvesting page, hosted somewhere else.
- By utilizing Adobe Cloud accounts they are able to sneak directly into the inboxes of their victims. The PDF itself that they host also looks “clean” to the Adobe AV scanners and thus they get the credibility they need to get victims to click through their PDF to the credential harvesting page.
- Compared to something like the NSO pegasus spyware we looked at a few weeks ago, this isn’t sophisticated in the slightest. The landing page in the PDF is riddled with grammatical errors. However, by piggybacking off of Adobe Creative cloud attackers skip right through into your inbox. The simplicity here makes this tick.
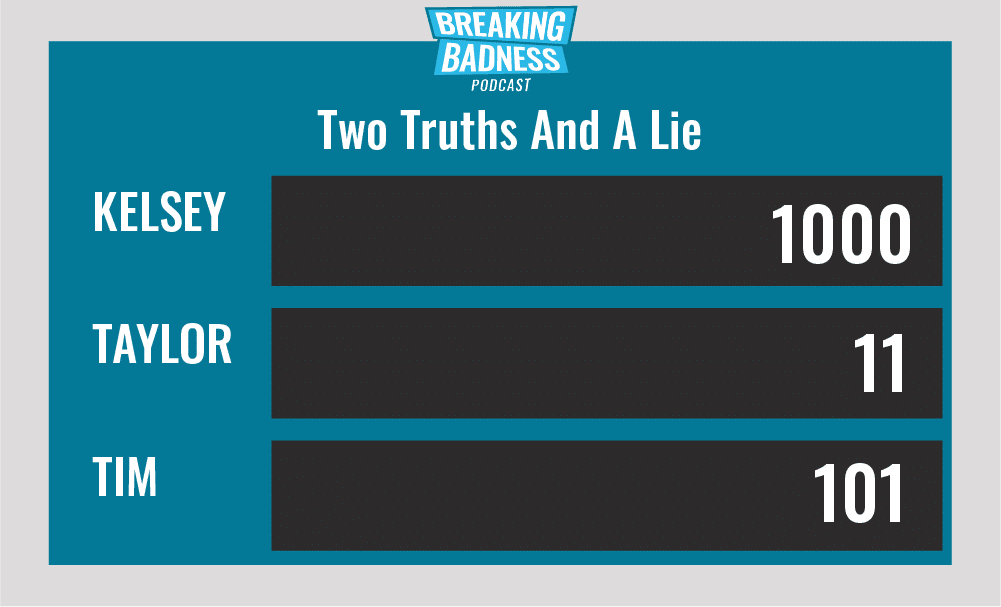
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Detecting Malware is as Easy as Pi
[Taylor]: 2/10 Goodies
[Tim]: 3/10 Goodies
Phishing Emails Cause a Cloud of Suspicion
[Taylor]: 3.5/10 Hoodies
[Tim]: 3/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!