Coming up this week on Breaking Badness. Today we discuss: Corn You Believe it? The Kernel Privilege Escalation is Back, Let’s Spill the FTCode on PowerShell Ransomware, and introducing our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Corn You Believe it? The Kernel Privilege Escalation is Back
- Google’s Project Zero discovered this use-after-free vulnerability in the Binder driver of the Android Operating System. Use-after-free vulnerabilities are when a program attempts to access memory after its been freed up by the system, which in this case with the Binder program allows execution of arbitrary code with the highest privileges possible.
- According to TAG the vulnerability is being exploited in the wild by the NSO group, which is an Israeli cyber intelligence company. You’ve probably heard about them in the news in the past couple years for the Pegasus malware, which was used to target human rights activists in the United Arab Emirates via URL in an SMS message.
- With this specific UAF vulnerability, a user can get exploited by installing an untrusted app which is one of the major security downfalls of Android. Another means is chaining the exploit with another vulnerability in the Chrome browser used to render content.
- This issue was previously patched in December 2017 in the 4.14 LTS Linux kernel without a CVE and by the Android Open Source Project (AOSP) in Android 3.18, 4.4, and 4.9 kernels. I haven’t seen any data to suggest why it happened, but I imagine because the bug originally was never given a CVE that it might have been swept under the proverbial rug with that insecure code being recycled and reused
- I think this is a reaffirmation that all code has bugs and vulnerabilities, and that’s normal. The crux of the problem is when vulnerabilities get weaponized and manufacturers don’t address it via patches. That is still one of the biggest security risks with running Android, it’s a gamble whether your device will be supported with patches or not.
- The scope and impact are both huge here. Especially that we have 18+ Android flagship models that are vulnerable, including Google Pixel phones. The impact is huge, since we’re dealing with the worst type of vulnerability. Unlike the CheckM8 vulnerability with the iPhone, the affected models don’t all have a hardware-based security key store. So, the impact on some of these devices can be even larger with your personal data being affected.
Let’s Spill the FTCode on PowerShell Ransomware
- In March 2013 Sophos released a report about a new Russian ransomware that was written completely in Powershell. However, according to Certego, the ransomware wasn’t too effective back then for a few reasons. For one, at the time, Windows XP was still widely used, and Powershell isn’t installed by default until Windows 7. So in order for Powershell-based ransomware to work, the attackers first had to download Powershell onto the victim machine. Certego also mentions that other, more basic pieces of malware such as Zeus were much more effective at the time, rendering the new Powershell variant less desirable to threat actors.
- This ransomware is delivered to the victim via phishing email. In this case, the email contains a Microsoft Word document attachment that is purporting to be an invoice. If the user opens the attachment, they are prompted to disable “Protected View,” at which point a malicious macro will download the ransomware. It’s important to note – this is not unique AT ALL as far as malware delivery goes. Fake invoices, Word document attachments, and malicious macros are all up there in the most common delivery methods for all types of malware, not just ransomware. If possible, it’s a good idea to disable Word macros at your organization.
- The macro runs a Powershell process that invokes the ransomware code itself. It also pulls down a variant of JasperLoader to allow the threat actor to download additional payloads if they want, and it also maintains persistence by creating a creating a scheduled task that runs on reboot.
- After this, the malware checks first to make sure the machine is not already infected by FTCode. If it’s not, the malware goes ahead and checks for all drives with at least 50 KB of free space and it looks for all the files with certain extensions (a ton of extensions). Then, it encrypts the first 40960 bytes of each of them using the “Rijndael symmetric key encryption”. Finally it appends the extension “.FTCODE” and creates the file “READ_ME_NOW.htm” ransom note in the affected folders.
- I didn’t see too many other reports of that other than the tweet cited by Bleeping Computer, but I feel that may actually be due to people not attempting to pay the ransom at all, or not reporting the failure out of an attempt to hide the fact that they’re facing a cyber incident. This is certainly not the first time a ransomware decryptor hasn’t worked after payment was given, which is part of why the FBI urges infected corporations and individuals to never pay a ransomware ransom. Last week we mentioned rEvil ransomware and how that variant was offering to decrypt 3 files for free before the user paid the ransom, and this is exactly why. People are (rightfully) scared that they’ll pay a ransom and still not get their files.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
(Truth) Earlier last month, over 500M+ Android users have installed Apps from the Google Play store that are bundled with malware.
(Lie) NY Attorney General has filed suit against McDonalds over the company’s alleged failure to notify customers of a breach. It was Dunkin’ Donuts!
(Truth) Social Media platforms will be forced to disclose encrypted messages from suspected terrorists, pedophiles and other serious criminals in a new treaty between the US and the UK.
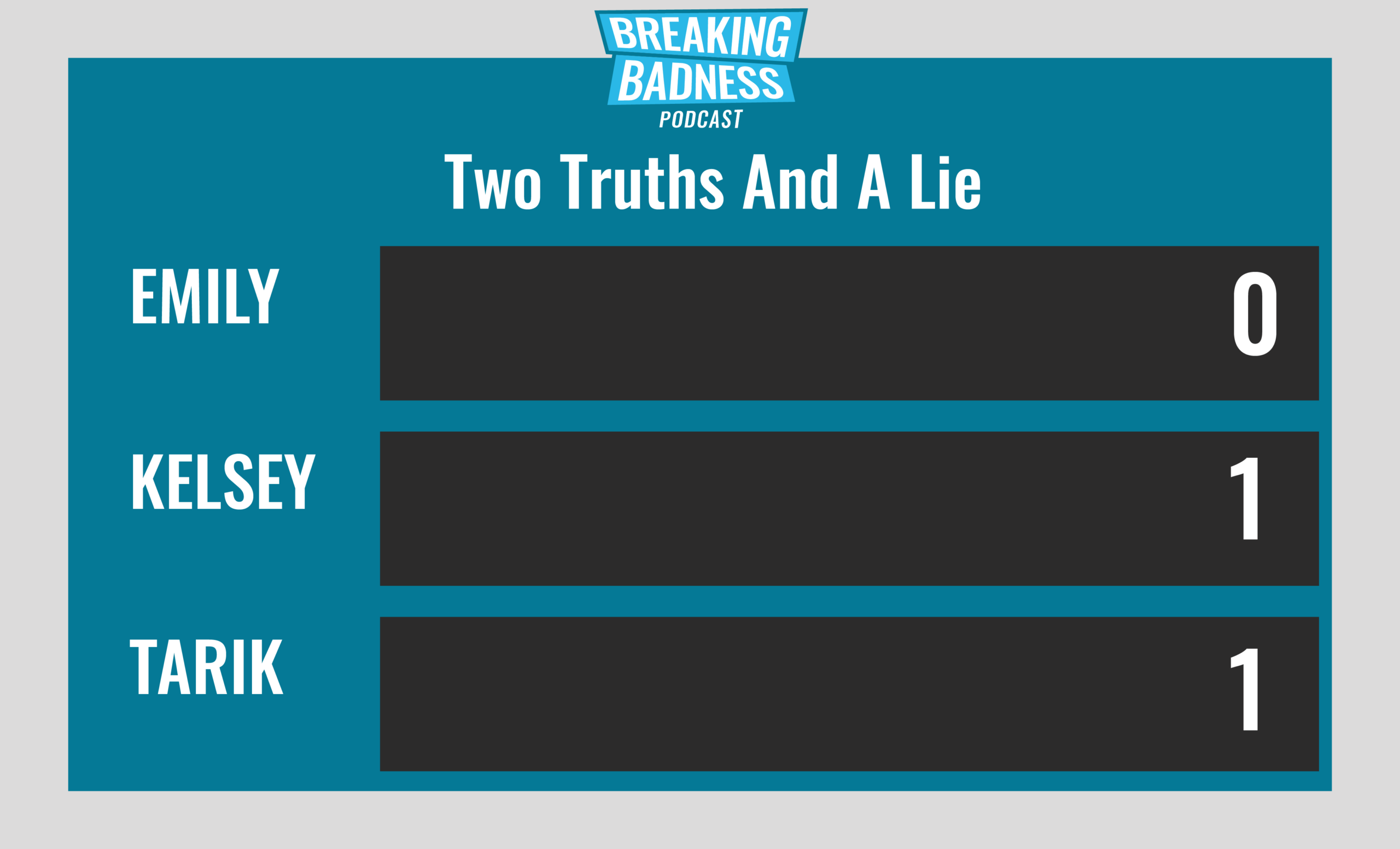
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Corn You Believe it? The Kernel Privilege Escalation is Back
[Tarik]: 8/10 Hoodies
[Emily]: 7/10 Hoodies
Let’s Spill the FTCode on PowerShell Ransomware
[Tarik]: 4/10 Hoodies
[Emily]: 4/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!

