Coming up this week on Breaking Badness. Today we discuss: Cozy Bear Finally Stops Ghosting Internet, Anti-CoinMiner Campaign Flies Under the Radar, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Cozy Bear Finally Stops Ghosting Internet
- What’s interesting is that it seems that Cozy Bear was never actually hibernating at all, but rather had slipped under the radar of researchers for a few years. This article from ESET indicates that they’ve been conducting this “new” campaign – Operation Ghost – since 2013.
- Historically, Cozy Bear has been a pretty infamous group. They are of course known for their involvement in the 2016 DNC breach. In 2017 they targeted the Norweigan government, and in 2018 they were suspected to be behind a one-off phishing campaign targeting American government officials.
- ESET uncovered a lot of information about this latest campaign. Most interesting to me was the first stage malware Polyglot, which can interpret characters from alphabets such as Cherokee, Katakana, and Kangxi. Another thing that really stood out to me was Cozy Bear’s use of social sites for C2 in this stage. ESET noted that they’d used Twitter, Imgur, and now Reddit to post encrypted C2 URLs. I’ve seen Twitter and Imgur being used before (and even Instagram I think), but Reddit is a new one for me. They posted a screenshot of the C2 comment in question, which I verified was still up and on Reddit as of this morning. One thing to note about their use of common sites like these and like Dropbox is that it’s a way of hiding amidst the noise. Defenders are expecting to see their users visiting social media sites and sites like Dropbox on a regular basis, so it doesn’t stand out as potential nefarious activity.
- Besides that, they’re also using steganography to be as sneaky as possible. One of the image file names mentioned in the report is “cuteanimals12.jpg,” which is just another way of them hiding in the midst of regular, expected downloads.
- After this, the second stage downloader MiniDuke is installed. This is not new malware for this group. And finally, the third stage is FatDuke. This one does seem to be new for this campaign.
- ESET lists a few different reasons they tied this campaign back to Cozy Bear. First, the use of known CozyBear tools such as MiniDuke was their first indication, but they admitted that wasn’t really a strong enough tie for full attribution. Many of the groups TTPs were in common with previously documented Cozy Bear TTPs – such as the use of social media for C2, use of steganography, etc – and that coupled with code similarity gave ESET enough confidence to attribute Operation Ghost to Cozy Bear.
- Interestingly enough, ESET has not been able to determine the exact method of infection for this campaign. This group is known for highly targeted spearphishing emails, but ESET says that no such email was ever found on an infected system. However, they also noted that two of the three infected organizations in question had also previously been infected in previous Cozy Bear campaigns, and that it’s possible they simply moved laterally to the systems at that org they wanted to compromise for this campaign.
Anti-CoinMiner Campaign Flies Under the Radar
- Cryptomining attacks are always interesting to me. They can be classified as low impact, since they essentially only steal resources from your organization (compute) and not PII or data.
- Interestingly enough, this attack was detected when administrators of a European international airport were migrating to a new EDR platform. In this case, Cyberbit’s offering.
- Once installed, Cyberbit’s EDR solution was able to collect a lot of interesting telemetry and process data, which uncovered this large malware outbreak on their network.
- One of the issues of traditional signature-based AV solutions is that they often only scan for malware once something is written to disk. In this case, the attackers used “living off the land” techniques by leveraging the OSS PAExec tool to execute their malware remotely without writing anything to a disk to be scanned by AV. PAExec (and psexec) are tools used by sysadmins for legitimate purposes, but in this case are being abused by attackers.
- I’m always fascinated by different means that malware authors use to bypass detections. In this case, there isn’t anything groundbreaking but there didn’t need to be. The malware authors were relatively sophisticated, using Reflective DLL injection as a cradle to their malware execution. And, just to level set Reflective DLL injection or loading isn’t a new technique but it’s moderately sophisticated. You essentially take an executable that is not on disk, retrieve it, map it to memory and then it gets written into an existing process and executed, preferably a legitimate one. This is a means of bypassing a lot of detection controls, except for EDRs which have kernel level access and can usually spot this type of activity.
- I wish I could estimate how many workstations that 50% number entails, multiplied by how much time the mining software was allowed to execute to really calculate how much potential money the attackers were able to acquire from the attack. That number can really help calculate the impact, but generally speaking I think the PR impact from this is really important to consider. Everyone has to fly to travel, and the notion of weak cybersecurity on airport networks makes me real uncomfortable as a customer. However, again, I’m saying this because malicious code was allowed to execute on airport networks even though in this specific case it was just a theft of computational resources and not PII exfiltration or ransomware.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
(Truth) How BlackBerry Used Improv Comedy To Make Cybersecurity A More ‘Human’ Topic
(Lie) Cyber attack in Mount Dora results in a net gain of over 60 bitcoin
(Truth) Hackers stole 26 million credit cards, but vigilantes just rescued them
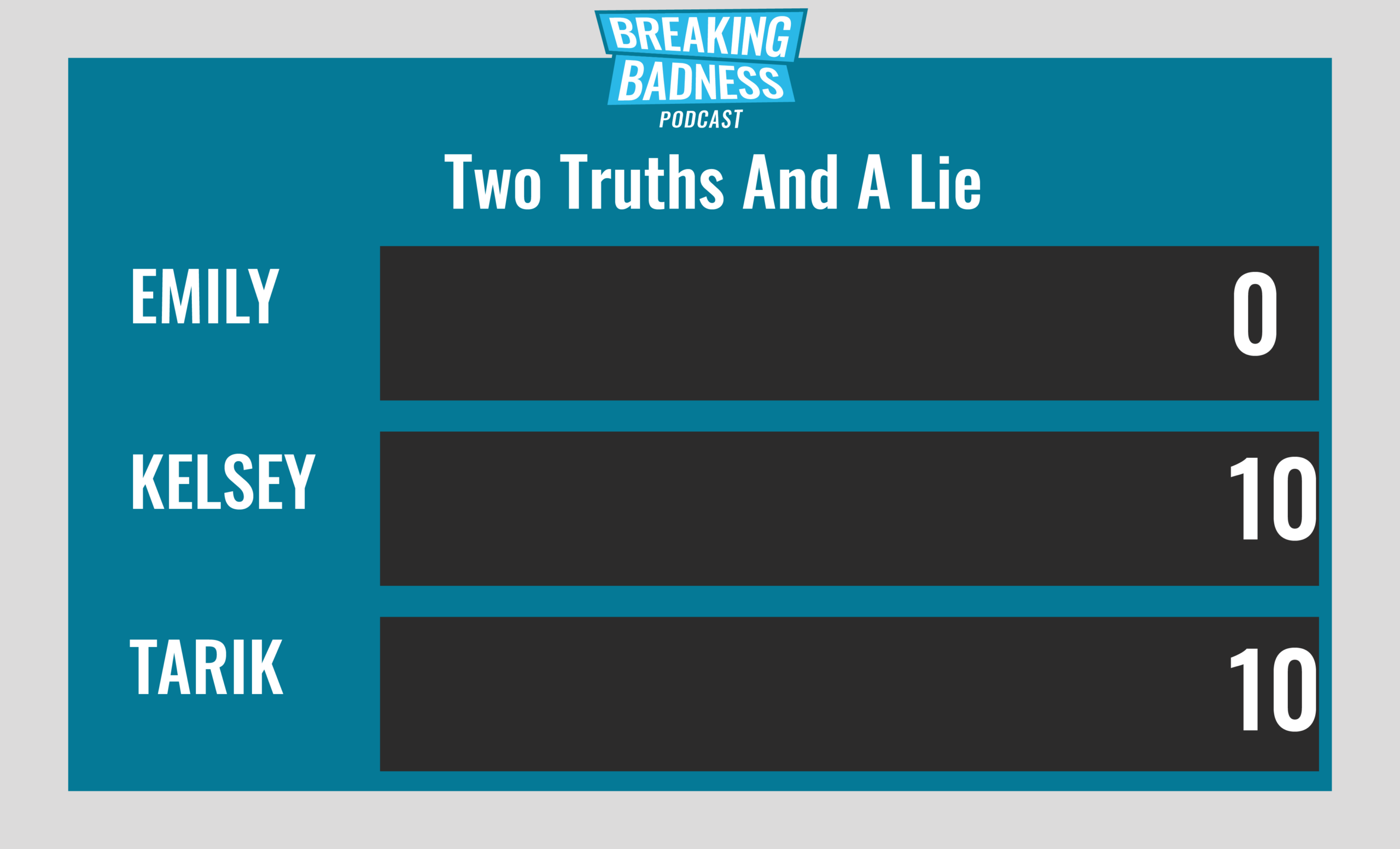
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Cozy Bear Finally Stops Ghosting Internet
[Tarik]: 9/10 Hoodies
[Emily]: 8/10 Hoodies
Anti-CoinMiner Campaign Flies Under the Radar
[Tarik]: 6/10 Hoodies
[Emily]: 4/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!

