Coming up this week on Breaking Badness. Today we discuss: Rabid Cybercriminals Use Raccoon Malware, I’ve Got a Funny Eeling About This: Charities Phished by Threat Actors, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Rabid Cybercriminals Use Raccoon Malware
- This malware is popular for a number of reasons – not the least of which should be the adorable nature of the little raccoon icon. Other than that though, this malware is easy for tech neophytes to use successfully.
- It’s an infostealer capable of stealing credit card data, cryptocurrency wallets, usernames and passwords, emails, browser data, cookies, and system information. That’s a lot of information that wannabe criminals would be interested in getting their hands on – and this malware gives them a way to do so even if they aren’t technically inclined. In addition to that, numerous users of the malware have left positive reviews, stating that the seller was very responsive to inquiries and had even made some changes “on the fly” when a user reported a bug. The criminal market – like any market – responds more positively to an item when it has good reviews and a good business model, and Raccoon Malware has both.
- This malware is delivered via the Fallout exploit kit and by phishing emails containing a malicious Word document attachment containing malcros. Once the malware is downloaded onto a machine, it unpacks itself in memory and connects to its C2 server, then it downloads a compressed zip file with multiple different DLLs. Finally, the malware checks to see if the machine’s local language settings include Russian, Ukrainian, Belarussian, Kazakh, Kyrgyz, Armenian, Tajik, and Uzbek, and if so, the malware does not run.
- Once all that is done and the malware is finally ready to go, it uses a few different methods to start pulling information from an infected machine and storing it in a Temp folder. It takes screenshots, steals system information, browser info from a huge list of browsers, outlook accounts, and more. It then zips all the info up and exfiltrates it to the C2. Then it self deletes.
- One of my favorite aspects of this report from Cybereason is actually how in depth they were as to the origins of this malware. According to cybereason, the malware author is a Russian guy known as Glad0ff in various shady forums. Glad0ff has made other malware variants before including the Decrux and Acrux cryptominers, the Mimosa RAT and the ProtonBot loader. It first was launched in April this year.
- Malware as a service is something that defenders should be concerned about because it expands the threat landscape a lot more. Even though the malware variants involved in MaaS – like Raccoon – are often not the most sophisticated, they are easy to use and widely adopted, meaning your organization may be pummeled with it. This one, for example, features an easy-to-use automated backend panel, bulletproof hosting, and 24/7 customer support in both Russian and English. And it only costs 200 bucks.
- Having an up-to-date antivirus solution and blocking unnecessary macros can help your organization defend against this malware.
- So far it looks like this malware has affected over 100,000 endpoints worldwide within a few months. As far as browsers that it can target, there’s a huge list of them, including:
- All in all, this has clearly been pretty widespread and successful, and as the operators are continuing to make improvements to their product, I’m only expecting this to grow.
I’ve Got a Funny Eeling About This: Charities Phished by Threat Actors
- There seems to be two sets of humanitarian groups targeted: one set centers around the UN, including the UN itself, the UN World Food Programme, the UN Development Programme, and UNICEF. The second set seems to target other large aid organizations, such as the United States Institute for Peace, Humanity and Inclusion (in France), and Concern Worldwide (in Ireland), the East-West Center. It also targeted other groups, including UC San Diego, and the Heritage Foundation among others. I am really not a fan of going after non-profits and humanitarian aid groups.
- The infrastructure here is small and contained. The attackers used two domains and a few IP addresses from the same block. These domains, session-services[.]com and service-ssl-check[.]com, are now on industry blocklists and have been flagged by our Domain Risk Score as being malicious for months. Our data suggests these domains became active in January of this year and were still active as of Friday. The AS on which the IPs were located has been known to be of “low reputation”, according to Lookout and have been used to deliver malware in the past according to Bleeping Computer.
- It was clear the actors were actively going after mobile users. The actors used multiple subdomains and hostnames to create a very long domain names which, if you mistake periods for slashes, resemble the real login URLs to these organizations.
- For example, the full phishing UNICEF domain name was: login.unicef.org.adfs.ls.client-request-id.session-services[.]com
- Whereas the legit one looks more like this: login.unicef[.]org/adfs/ls/client-request-[LEGIT MS TOKENS]
- The bad actors added specific mobile-aware JavaScript to render the phishy login pages on phones and tablets correctly. Because screen real estate is at a premium on these devices, only a small set of the URL is shown—the first few characters, specifically. This, added to the fact that the attackers got real SSL certificates for their domains (not Let’s Encrypt ones, but for pay ones), would mean a mobile user would see the green lock and then something like “login.unicef.org” on their phones. It would have fooled me.
- The keylogger embedded on the landed pages is one of the sketcher portions of this attack. The bad actors added custom JavaScript to the login page which captured the user’s email address and password. They used the ‘onkeyUp’ JavaScript keyboard event to capture this information, so the user didn’t have to press ‘Enter’ for the attackers to get the credentials. As the user typed in their information, the bad actors were capturing it. This means even a user who started to log in but stopped could still have been compromised.
- This is a targeted attack on humanitarian aid organizations. It’s like kicking a puppy, this is not something that you do, ever. These phishers seemed to have operated for 10 months on this campaign, so I’d have to guess that it’s been successful. The keylogger is a new twist on this operation, and a disconcerting one. Then again, the domains and infrastructure used are easy to detect as being used for malicious intent. So, reasonable execution on known bad infrastructure. The trick here is the mobile component: what kind of endpoint protection/malware blocking do users have on their phones?
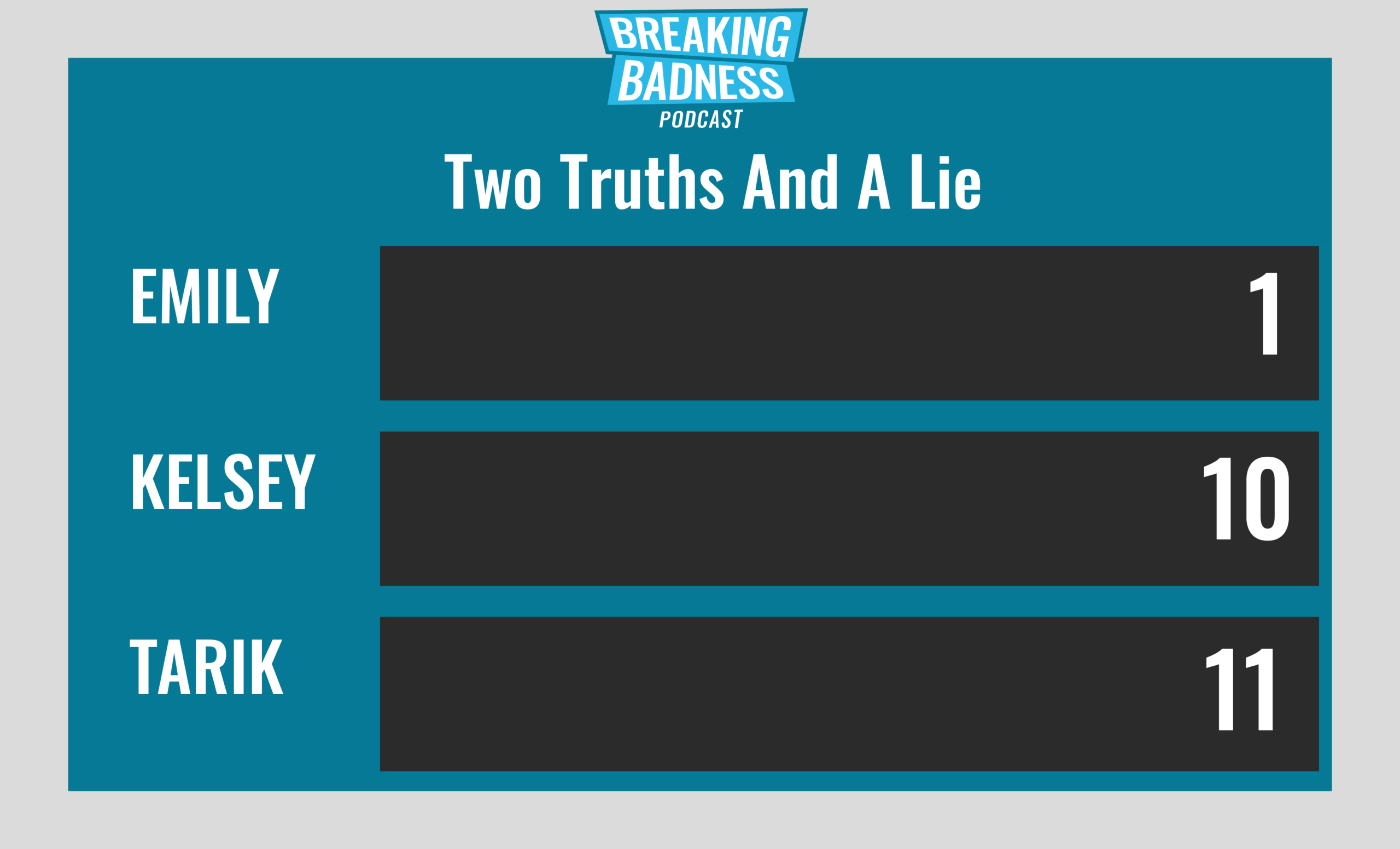
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
(Truth) Yes Bank Files a Police Complaint Against Fake News,Alleging It Frightened Off Investors
(Lie) Ransom-Where? Sygic GPS Navigation App Infected With Ransomware That Denies Users Turn By Turn Directions
(Truth) Devs Commit Cardinal Coding Sin – Vatican Launches ‘Smart Rosary’ Complete With Brute Forcing Flaw
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Rabid Cybercriminals Use Raccoon Malware
[Sean]: 3.5/10 Hoodies
[Emily]: 4/10 Hoodies
I’ve Got a Funny Eeling About This: Charities Phished by Threat Actors
[Sean]: 7/10 Hoodies
[Emily]: 5/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!

