Coming up this week on Breaking Badness. Today we discuss: GRUs Bears Bombard Burisma, Son of a Patch! NSA releases Patch for Microsoft Vulnerability, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
GRUs Bears Bombard Burisma
- Fancy Bear or APT28 is a Russia-based espionage group that most attribute to the Russian intelligence agency GRU. It’s been around since at least 2008—likely early. Their big hit, of course, being the Democratic National Convention email hack and their attempts to influence the 2016 election. Along with that they’ve hacked French television, the World Anti-Doping Agency after Russia was banned from the Olympics for drug use, the Olympic Committee hack and dozens of attacks on journalists most notably the Bellingcat group that uncovered the men behind the downing of Malaysia Airlines Flight 17. They aren’t as known for disinformation campaigns as their counterpart Cozy Bear, but they do a decent amount of that as well. They’re an interesting group to study and quite sophisticated.
- Per usual, Fancy Bear leveraged spearphishing emails that go to a website that looks legitimate—in this case it’s websites that look like sharepoint. It’s all about the lateral movement and targets after that successful credential theft though, right? That’s the stuff we don’t quite know yet. The spearphishing for entry thing is consistent everywhere though. It works, why stop?
- Their targets, for this campaign, were all subsidiaries of Burisma Holdings which is the company that Hunter Biden—Joe Biden’s son—sat on the board of from 2014 to 2019. This is the holding company that is tied in with Donald Trump’s current impeachment since it all ties to the quid pro quo bit, asking Ukraine to investigate the Biden family in exchange for money and all of that. It’s… interesting to say the least that those are the targets.
- What many are posing here as a theory is that this follows the tactic of breaking into tertiary companies of a final target so that there is easy lateral movement. The smaller subsidiaries won’t have as mature of a security team so you sneak in there, find out how they’re connected, maybe drop a couple of malicious documents and pivot into the main target’s network. If that’s the move here then people are thinking this is an attempt to get information on Hunter Biden’s time at Burisma Holdings and use that much like the GRU did in 2016 to influence the presidential election. If you dump a trove of emails people will find whatever they want to believe in there—the true pinnacle of confirmation bias when you read a ton of emails out of context. Not saying there might not have been something shady going on, but it is pretty easy to sway public opinion with a document treasure trove as we’ve seen before.
Son of a Patch! NSA releases Patch for Microsoft Vulnerability
- This isn’t the first time, nor the last, we can expect to see the NSA be involved with Windows Crypto vulnerabilities. This vulnerability has a cool name too. AKA “CurveBall” (because it affects ECC – Elliptic Curve Crypto) attack scoped out to Windows 10, Server 2016 && Server 2019.
- Essentially, the vulnerability affects the Windows CryptoAPI. This API provides a ton of cryptographic functionality for Windows. It’s used for all encryption/decryption routines, generating random numbers as well as authentication via digital certificates.
- The CurveBall vulnerability lies in the validation, or lack thereof, in the certification signature process with the Windows CryptoAPI.
- PKI, or the Public Key Infrastructure does a lot of things. It really is the underlying mechanism that systems use to help validate identities and software.
- This is a really serious, high impact vulnerability. When you can fool the operating system to trust a digital certificate you can do all kinds of nasty things.
- When I do traffic analysis on my malware VM, I install a certificate I generated on the system and I’m able to decrypt all HTTPS traffic.
- If you digitally sign a binary, in this case malware, this would affect how your AV (or Windows Defender) treats and trusts the executable. Generally speaking, digitally signed binaries are added to an allowlist by Windows Defender.
- If you have Windows 10, Windows 2016 or 2019 Server you need to patch. Vulnerabilities in crypto trust systems are absolutely critical!
- In a post-Snowden era, I think it’s safe to say there is a general uneasy-ness about the NSA. We can thank the NSA for being apart of the responsible disclosure process for this major vulnerability, as well as for contributing towards OSS with Ghidra. On the other hand, we all have our apprehensions about them. It’s a very grey area, in my opinion.
- The NSA has always been involved in Crypto, and that’s not going to change.
- Curveball vulnerability is really concerning! When you have the ability to tamper with the trust systems of Windows, nothing good can come from it. Everyone needs to patch yesterday.
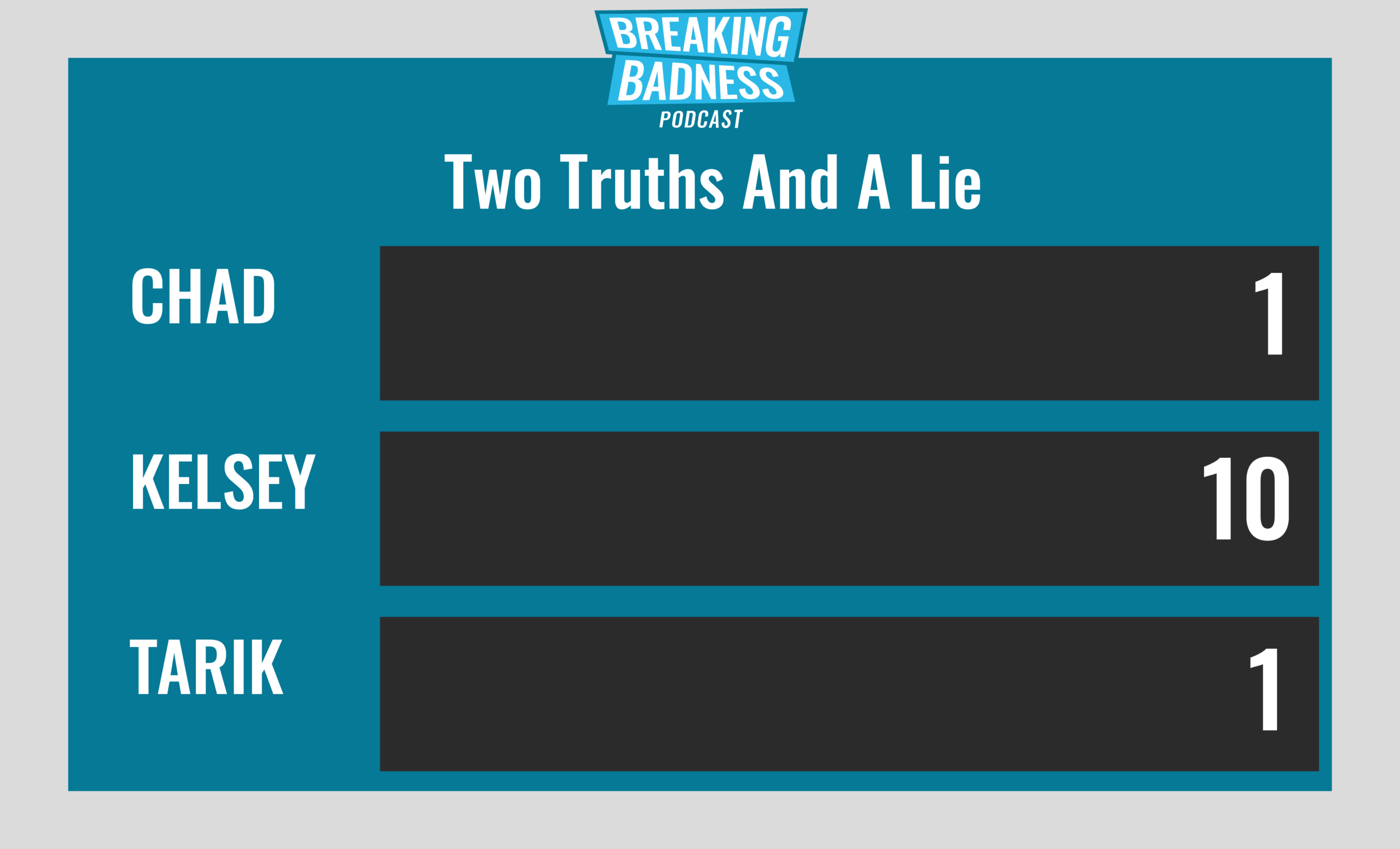
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
Current Scoreboard
This Week’s Hoodie/Goodie Scale
GRUs Bears Bombard Burisma
[Chad]: 9/10 Hoodies
[Tarik]: 8/10 Hoodies
Son of a Patch! NSA releases Patch for Microsoft Vulnerability
[Chad]: 9/10 Hoodies
[Tarik]: 9/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!

