Coming up this week on Breaking Badness. Today we discuss: Reopen Domains: Shut the Front Dorr, US Government Hopes to Codify Nation State Fast Food Phishing Campaigns, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Reopen Domains: Shut the Front Dorr
- I immediately felt that the domains registered in Florida at a later date and the domains that were redirecting to websites had to be different people and I wanted to show that so I went about pulling infrastructure data, then went with things on the page, then went through historical WHOIS records and eventually brought it all together through historical SSL certificates.
- I have a number of scripts that I use—really more just shell aliases—that pull things down and help me glue them together or distill down information I care about. You can use services for this and pay someone or you can get good on the command line with the coreutils. This just pulls data, kicks off scans elsewhere, pulls their results, collates it all basically, then looks through all of those pulled results and grabs out all of the unique URLs.
- The Dorr domains were the most interesting because of how it was all tied together. Sure, the content looked the same, but most of the domains had been registered with privacy at the onset so I had to find other ways to prove they belonged. The Cloudflare SNI certificates here showed that all of these domains were hosted in the same place and revealed a bunch of other domains that Dorr had. This also led to some other email addresses which then spidered out through other historical WHOIS records and the whole network fleshed out.
- The Dorrs were pumping their reopen domains on facebook groups they spun up. Basically the domains were just a way to drive traffic to their action pages and donate buttons.
- They probably actually believe in what they are doing, but the giant donate buttons I think say the most. They are trying to make some money off this whole thing for certain.
- The second batch of domains was a smattering of potential phishing campaigns, domainers and other small time folks setting up domains along with the activist in Florida who registered dozens of domains to keep them out of the hands of extremists. That second batch just keeps growing as well. Not much activity from the Dorrs since their initial setup.
- As of today there have been almost 1000 new reopen domains registered since the first ones of the Dorrs on April 8. These terms are definitely trending upward and we are seeing all kinds of things on them now.
- My main concern here is public health. Every side of the political spectrum does these campaigns, but in this instance it is negatively going to affect public health and probably be a detriment to us actually reopening the country sooner. It’s idiotic and I would be less concerned about it if it didn’t relate to everyone else as well. The protest in Olympia, WA here had over 3000 people at it. We will see in the next week how many of them come down with symptoms.
US Government Hopes to Codify Nation State Fast Food Phishing Campaigns
- I think one of the most interesting lures is using popular US based fast food companies in conjunction with COVID19 wording. But also, were seeing validation of more phishing attacks masquerading as health organizations. But with the fast food…. For example, one of the lures is stating that due to the current pandemic you can order food online with these delivery options. Upon initial glance, a casual reader would say this email is legitimate and probably harmless. There isn't a mention of asking for your credit card or account information, or any other real hallmarks of phishing attacks.
- What's interesting is that a majority of these email attacks were flagged as spam and never made it to the users actual inbox. So unless you're really bored and going through your spam folder, then you likely weren't exposed to this attack. I personally love digging through my spam folder, but that's just for security research fun.
- What's fascinating and really affirming here is the amount of malware/phishing messages being sent out correlate to how much activity we've been seeing in the threat intel community around COVID-19. Approximately 18 million malicious emails a day have been detected meeting that criteria.
- The threat group Charming Kitten is an APT group associated with the Iranian Islamic Revolutionary Guard. Their attack TTPs have a common pattern: phishing and account hijacking.
- According to Google, Charming Kitten was detected in all of this noise conducting phishing attacks against international health organizations like the WHO, specifically around COVID19. While their goals aren't explicitly clear, we can glean their purpose is to hijack accounts targeting the WHO to gather more information on what they're working on and other data points. Having this type of access would be beneficial in a lot of ways.
- I think attackers are trying every angle they can here with COVID-19. I think some of the lures masquerading as free food coupons or meals is on one hand kind of humorous but also pretty sad. Attackers are really trying any angle here to compromise people by taking advantage of the pandemic...even fast food.
- In terms of advice for health organizations, don't think I need to convince these organizations to invest in a cyber security program. However, there are specific things that these and all organizations can do that are quick wins: implement 2FA and get yourself a strong EDR.
- I think we’re going to see more success in novel approaches for lure building. Although we don't have the data specifically, the thinking out of the box methods are really interesting like fast food delivery as a target. It’s really attackers throwing darts at a dartboard and seeing what hits.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
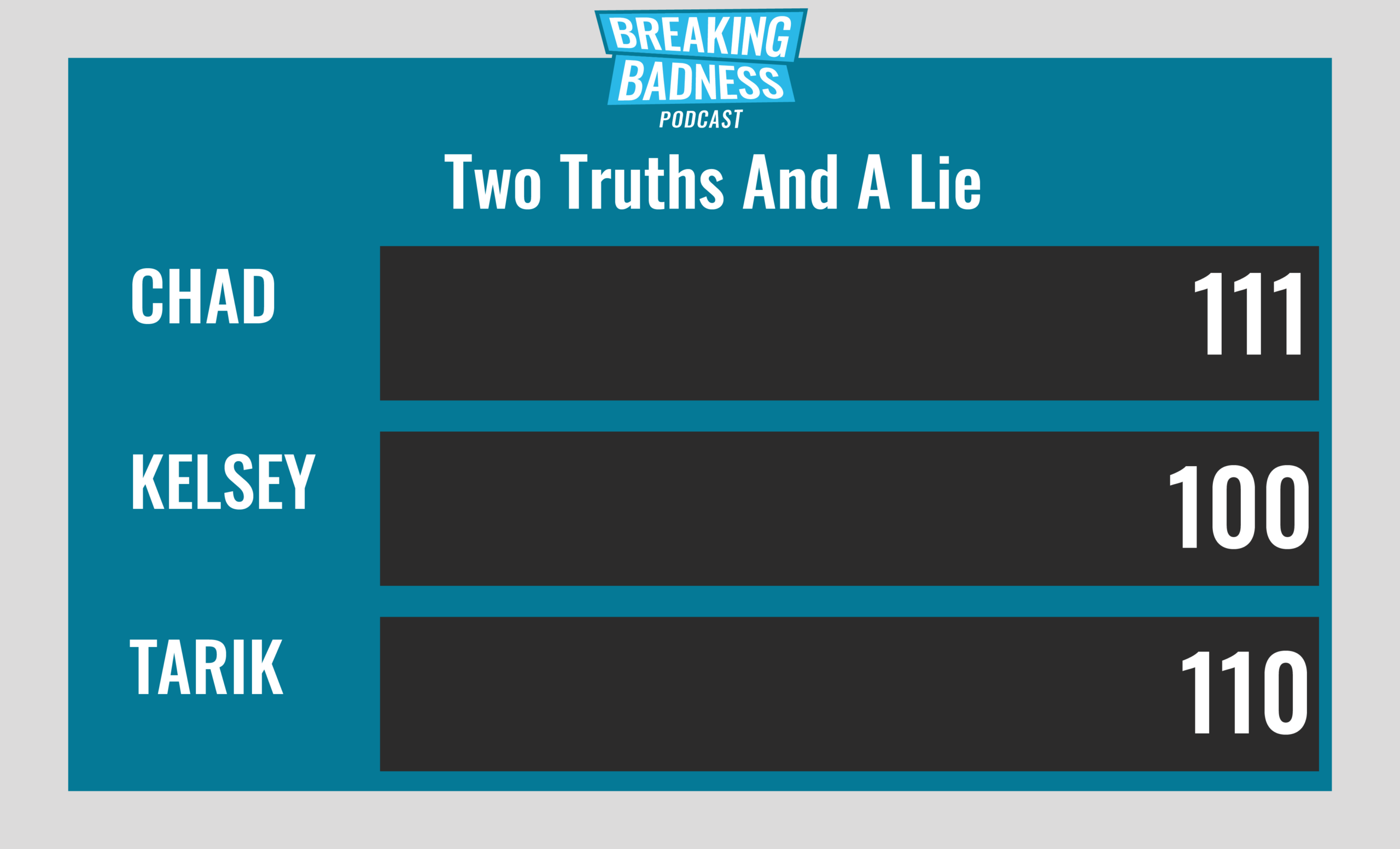
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Reopen Domains: Shut the Front Dorr[Chad]: 10/10 Hoodies[Tarik]: 10/10 Hoodies
US Government Hopes to Codify Nation State Fast Food Phishing Campaigns[Chad]: 6/10 Hoodies[Tarik]: 8/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!


