Coming up this week on Breaking Badness. Today we discuss: The Dark Before the Avaddon, NSA and FBI: the Bearer of Bad News, and our fun game, two truths and a lie.
Here are a few highlights from each article we discussed:
The Dark Before the Avaddon
- Avaddon is a new “Ransomware-as-a-Service” (RaaS) malware that uses an affiliate revenue system as part of how this threat group achieves it’s financial goals.
- Avaddon is being actively advertised on various cybercriminal forums, and has been associated with recent massive email spam campaigns for its distribution.
- I knew I wanted to tackle ransomware for some security research investigations as a goal. I began to dig into my cybercriminal forums I’m a part of and noticed some marketplace activity around Avaddon. That, plus an article in Bleepingcomputer.com was released that day showing a major malspam attack using Avaddon.
- You can read more about the details of the victimology on my blog post, but, it was fascinating to see the country breakdown have more Asian countries involved and the emphasis from Avaddon’s authors to not include RU/CIS countries in attacks.
- The Avaddon creators are following a really highly effective new trend in ransomware called ‘double-extortion’, which was originally created by the Maze ransomware authors. In traditional ransomware attacks, you lose access to your files and have to pay a ransom to get them back. With double-extortion ransomware attacks, you lose access to your files like traditional ransomware but prior to encrypting them the ransomware will upload those files to an attacker controlled server. The ransom note usually has a timer of some sorts and a threat that they will publish your data publicly if you don’t pay. So, that may not be a threat to some home users but VIP targets or companies that are at risk of losing intellectual property or some sensitive emails would be way more inclined to pay.
- The initial loader is pretty trivial. Keep in mind that the loader was created by the “customer” of Avaddon and not the Avaddon author. The loader quality is pretty juvenile in its design, and generally should work on older Windows machines that are unpatched using a forked process of Bitsadmin and Powershell to pull down the Avaddon binary. Take a look at the blog for a more in depth analysis.
- Speaking agnostic of Avaddon, the growing trend of double-extortion ransomware is scary. It’s more effective, flat out. Attackers (much like us defenders) always look for new ways to be effective, and if someone has found a means or a method others will copy it. Avaddon did with Maze’s double-extortion, therefore it’s reasonable to assume that other ransomware operators will do the same. Double-extortion ransomware will eventually be the new norm.
NSA and FBI: the Bearer of Bad News
- This is a new rootkit that they’re unveiling the discovery of and calling out the GRU. it’s a pretty big deal since there has been an uptick in rootkits from other state-sponsored actors this year according to some research you may have seen at Black Hat this year. Seems to be that they’re coming back into vogue. The name Drovorub actually is the name the authors gave it as well—means chop firewood basically in Russian. Lastly, it’s also targeting Linux systems so specifically going after server platforms and what not…since it’s still not the year of Linux on the desktop.
- This malware is tied to APT28 in this case AKA Fancy Bear. They typically go after intelligence targets. Typical Russia state-sponsored party here. Western governments and such.
- US officials published this alert because they have reliable ways for detecting this and it has been being deployed for a little bit. Using some network analysis and on-system scripts to talk to the implant they can reliably find the rootkit and eliminate it.
- Russia continues to be the most advanced adversary here. The work by the GRU in this case was quite elaborate. Rootkits are particularly dangerous because they can intercept system calls of programs meant to find them and then return like everything is normal. Rootkits are notoriously difficult to discover and really the only fully reliable way is to scan the system and check files against known-good files while it is offline. The main parts of importance for me here are the detection techniques they’ve outlined though. Really good reporting by the NSA and FBI here.
- The C2s of Drovorub were using some of the same servers that are known APT28/Fancy Bear C2 infrastructure so it looks like just recycling of old infrastructure has linked them at this point.
- The malware is divided into a database, server component, implant, and the rootkit itself. The implant of course installs the rootkit which communicates with the C2 that’s the database and server component. What’s important to note is that this just infects Linux 3.7 and lower so it’s an older version that has been largely patched to fix the holes used by the implant. As of today we’re on general release for Linux 5.8 —installed it this morning actually. Old servers though are of course still vulnerable here and unfortunately old servers are often holding that technical debt and old data companies find so valuable.
- I still don’t think the move for Russia is actual vote manipulation though, but rather influence. Changing votes is too risky a move, but purposefully disrupting polling centers now there’s a big maybe. We’ll see in the months to come though. All of it is unsettling.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
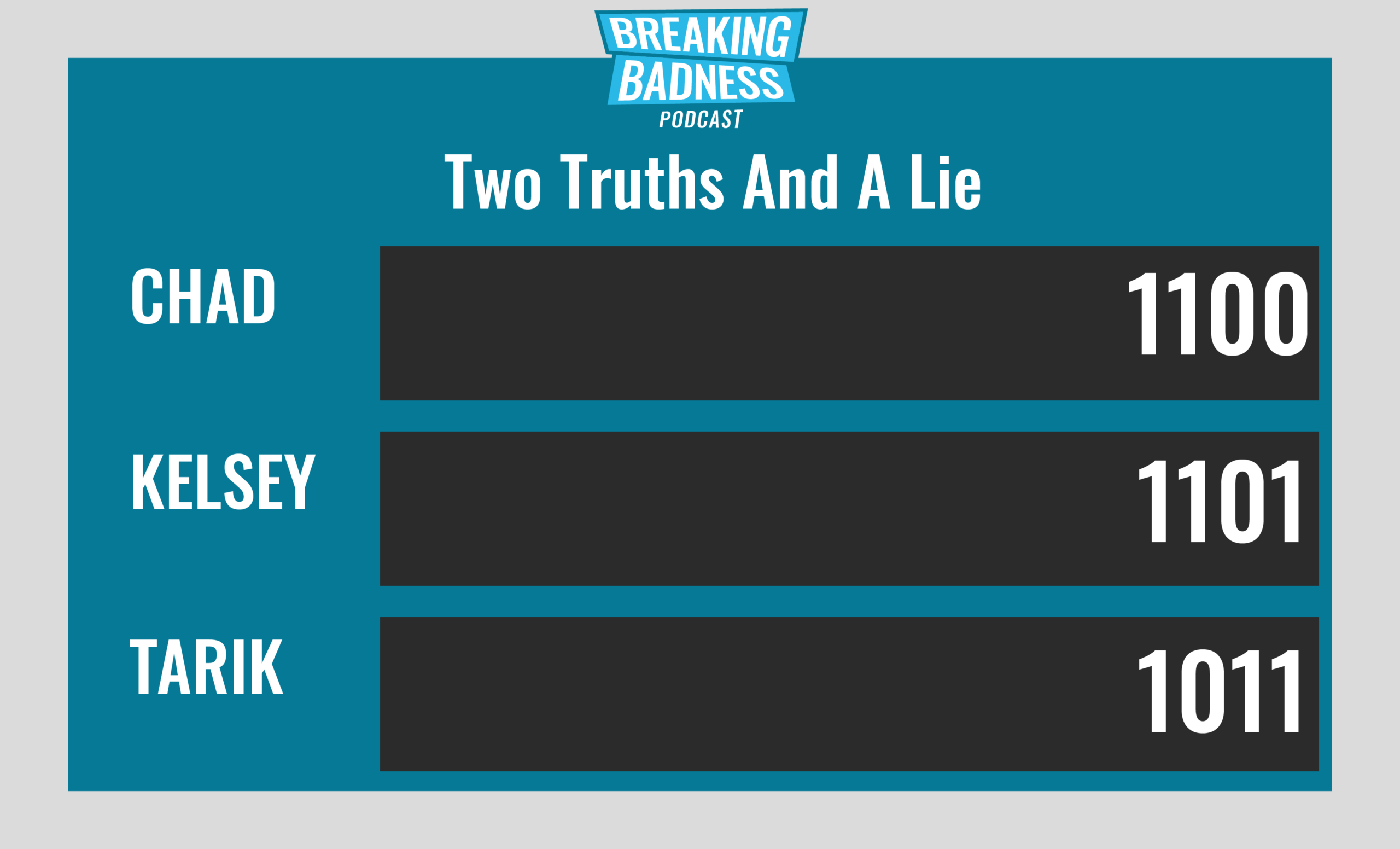
Current Scoreboard
This Week’s Hoodie/Goodie Scale
The Dark Before the Avaddon
[Chad]: 8/10 Hoodies
[Tarik]: 8/10 Hoodies
NSA and FBI: the Bearer of Bad News
[Chad]: 10/10 Hoodies
[Tarik]: 10/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!

