Coming up this week on Breaking Badness. Today we discuss: Europol the Rug Out From Under DarkMarket, Looks Like We Have Sprung a SolarLeaks, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Europol the Rug Out From Under DarkMarket
- This was considered to be the largest illicit marketplace on the darkweb. People sold all kinds of things, largely the things you’d expect in an underground market, like pharmaceuticals, counterfeit goods, counterfeit money, credit card credentials, and I’m sure a whole lot more beyond that
- Here are some stats for you: about 500,000 users, over 2,400 vendors, over 320,000 transactions. They also claim that it has moved more than 4,650 bitcoin, which translates to a dollar figure that is fluctuating so rapidly I can’t give it to you. They do claim that the total value of all this is in the neighborhood of 140M Euro.
- Europol doesn’t just want to shut down this particular operation; they want to hone their ability to shut down others as well. We know, obviously, this is far from the only marketplace of this kind, and it’s a sure bet that Europol and other law enforcement agencies are targeting more of these.
- As things EU are intended to be, this was a team effort. The arrest of the Australian guy who seems to have been running the thing was done by the Central Criminal Investigation Department of the German city of Oldenburg. But that investigation itself, the one that led to the arrest, was done by the Koblenz public prosecutor’s office. The shutdown of the servers for DarkMarket was supported by the German federal police.
- Europol itself helped to coordinate these efforts, and provided analysis and intel and personnel. They also wrote the press release.
- So the process of shutting down DarkMarket involved seizing and turning off more than 20 servers that were in Moldova and Ukraine, and of course the arrest I mentioned earlier.
- The future of DarkMarket is not too bright. But in general, we have to keep in mind that this is a giant game of whack-a-mole. There are countless other dark markets ticking along just fine. This may have been the largest, but of course that doesn’t mean that it accounted for most of the actual volume of illicit goods and money. Those operators of DarkMarket that don’t get arrested will undoubtedly just focus on either putting up new marketplaces, or building upon ones that already exist. Underground markets have existed pretty much as long as any markets have existed, it’s probably safe to say. But on the positive side, as I mentioned, Europol and the law enforcement agencies it assists, are all getting better at this. That’s a positive. We’ll have to hope that they’re getting better at defeating these things more rapidly than the criminals are getting better at their opsec.
Looks Like We Have Sprung a SolarLeaks
- Jake Williams, commonly known as MalwareJake on Twitter dropped a bunch of screenshots on the 12th.
- Jake Williams mentioned in his tweet that this is an attempt at a Guccifer 2.0 bluff (you may remember, Russia faked being a Romanian hacker who went by Guccifer when leaking DNC data) and the ShadowBrokers-esque bit of offering to sell the data from their exploits including Windows source code, Cisco products, SolarWinds source code, and FireEye red team tools. There really isn’t more to be deciphered from it though until more has come out.
- The images shared by Jake Williams featured 600,000 dollars for the Windows source code (claiming to be 2.6GB compressed though which is like not even close to the size of the Windows source code). $500,000 for Cisco source code, $250,000 for SolarWinds, and only $50,000 for FireEye.
- My gut though is that there probably is some interesting data here. Jake Williams had a good point about how all of the data is commercially interesting but of no intelligence value which means nothing from any of the government organizations breached. That’s kind of intriguing to me as well. I’m guessing the ruse here is in whoever they are claiming to be but that they may have some data to sell and that hopefully no one will pay top dollar for it.
- I have not seen anything from Microsoft since the reporting from Jake Williams first came out. Microsoft did admit earlier that the SolarWinds hackers did access their source code, however, so it’s possible.
- Joseph Cox from Motherboard found a hidden service version of the leak site that was misconfigured and dumped a lot of server data and also tied to another clear web website. Outside of that a lot of the takes are just split on whether or not this is a cash grab or to be trusted as the real deal. Lots of people seem to think that we’re looking at the actual actors due to none of the intelligence data being included in the leak and that that indicates it being a state actor because some random hacker would leak at least something interesting there. Again, all so much speculative, we’ve got to wait further on this one.
- Supply chain attacks are a huge problem, right? We just blindly trust so much software in our daily lives and that includes the open source libraries that are used in creating so much software today. No one writes their entire stack from scratch so there is just so much trust involved. We’ll continue to see more from this if anything from attackers reading the news and thinking, sure, why not, I’ll give this a try and see how many places I can get into. Luckily for a lot of these attacks it takes patience that cash grab cybercrime actors usually do not possess.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
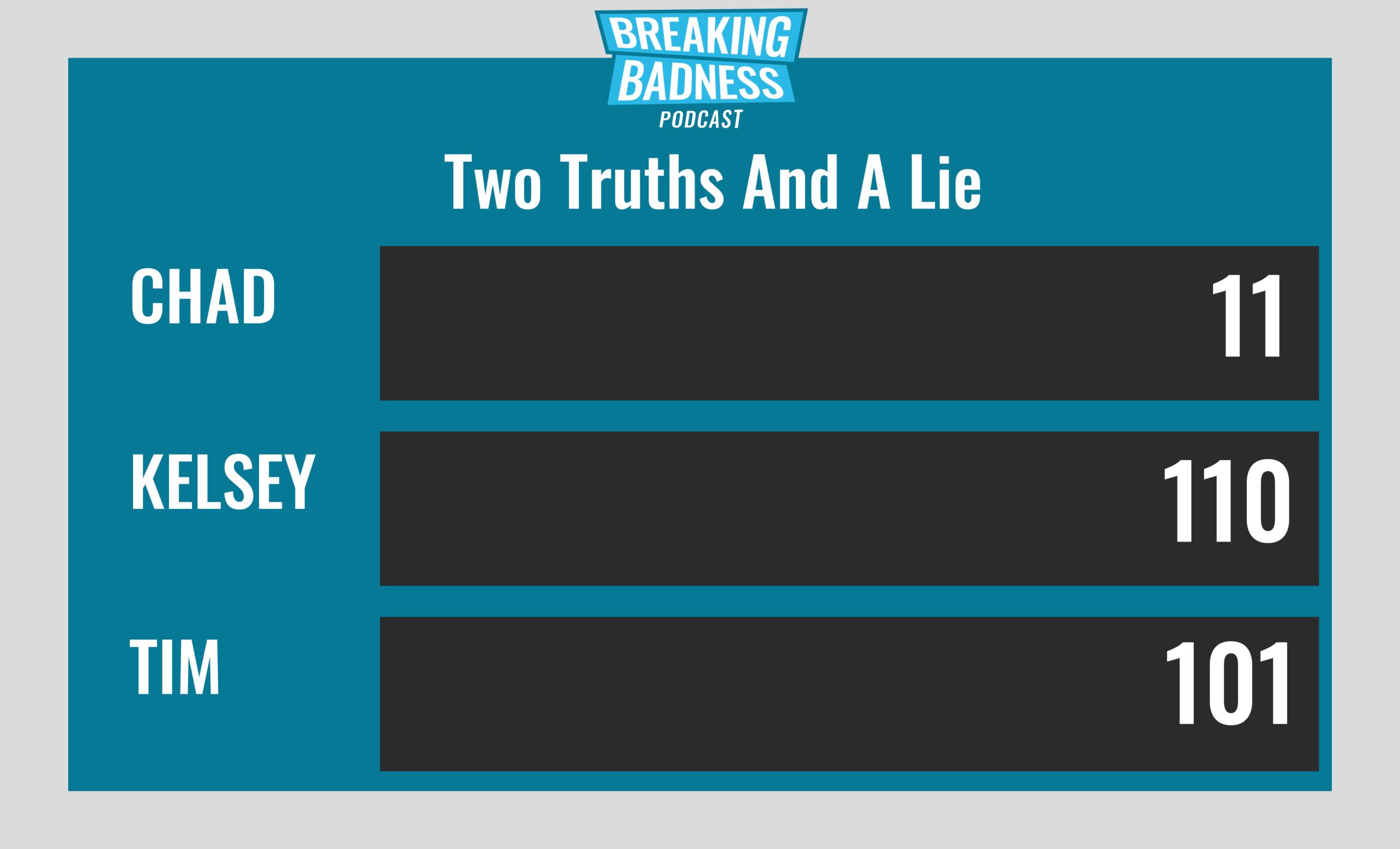
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Europol the Rug Out From Under DarkMarket[Chad]: 3/10 Hoodies[Tim]: 3/10 Goodies
Looks Like We Have Sprung a SolarLeaks[Chad]: 8/10 Hoodies[Tim]: 8/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

