Coming up this week on Breaking Badness. Today we discuss: Financial Corporation Pays Their Premium, The SimuLand of Opportunity, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Financial Corporation Pays Their Premium
- This would be the biggest public payout that has been made. We’ve already seen, according to some Palo Alto research, that ransomware average payments have gone up about 170% to over $300,000 per payout. That’s quite the sum of money for these people to be getting and why it continues to be so lucrative. It’s actually more lucrative if you’re in a CIS country now to start a ransomware affiliate gang than to start a legitimate technology company.
- CNA is one of the larger insurance firms in the world. So they have access to lots of client and customer data, anything involved in the insurance industry. They offer cyber security insurance which covers things like your network being infected with ransomware. So this is an enticing thing for ransomware actors as they would know what the underwriting on policies look like so they would know, when compromising a victim that uses CNA for insurance, what they can ask for at the negotiating table.
- Basically we know that the Hades ransomware, often tied to Evil Corp, a group which was sanctioned by the US in 2019, was the tooling used. Attribution of course is always hard in these casse, but it’s likely-ish to be them. According to some Internet rumor mill they were originally asking for $60 million, but CNA negotiated them down.
- CNA did state that none of their policy data or record systems were compromised, but who can say really. They were also very adamant to mention repeatedly that they didn’t break any laws in paying even though the US government has been talking about sanctions for companies that pay out to criminal hacker groups. It’s true, they didn’t break any laws, but that doesn’t mean it’s a good look.
- A few other highlights from the world of ransomware this past week: the n3tw0rm group with ties to Iran has been going after Israeli companies. Lots of new Conti infections. Darkside had their systems taken over and now affiliates are angry about not getting paid. The Zeppelin ransomware came back to life after being quiet for a while. A bunch of cybercrime forums quit allowing ransomware affiliate group advertisements since they seem to be drawing more and more heat. It’s a mess out there. Folks working ransomware, so we are tired.
- I think we’re just going to see more groups come online. Especially with how easy it is to get away with ransomware infections and make quite a bit of money. There really is no government enforcing anything against these actors in CIS countries so it’s just an open season. If you’ve got some technical chops it just makes sense. I’d like to think we’d have some technology changes that would render ransomware less viable, maybe some better behavioral analysis baked into Microsoft Windows or something, but even then that can be circumvented since a lot of these groups start with a hands-on-keyboard infection and move their way deftly through networks to infect all machines. I don’t really see much changing other than higher payouts perhaps.
The SimuLand of Opportunity
- For years now Microsoft has been relatively proactive about security. When I first got into infosec mumble mumble years ago, we all joked that Microsoft represented job security for all of us, because they had so many egregious vulnerabilities. They’ve come a long way since then, and I think it makes sense that they contribute something back to the community in this form.
- This lab environment is a kind of an environment-in-a-box with multiple components like AD servers, Azure cloud services, and other components you’d typically see in an enterprise Windows network. One of our engineers referred to it as an “on-demand cyber range” and that’s a good description. You can execute various kinds of attacks, and they have created simulation plans that map to the Mitre ATT&CK framework so you can base your simulations on known adversary tradecraft.
- To deploy StimuLand, you have put up a Github repo that anyone can access, so it’s freely available on the Information Superhighway. But it’s not free. You have to have an Azure tenant and at least one 365 ES license, though that one can be a trial license. As far as how you would deploy it, it’s all on Azure, and I will say that it’s not exactly click-n-go. There are a fair number of configuration steps to get it up and running. The advantage, though, is that it’s an alternative to red-teaming your production environment, so for orgs that haven’t built their own ranges, it’s an easier way to develop that.
- According to Microsoft, they’d like to see community support, with contributions of new scenarios and topologies and such. You can create an end-to-end attack path scenario and open a ticket in their github to post it. Of course, there are folks saying that attackers might well use this much like they use VirusTotal to hone their malware to evade detection. An attacker could use SimuLand to develop novel techniques without having to practice in real environments where they could tip off defenders about what they’re attempting. I don’t know if this was part of Microsoft’s vision, but it should at least be part of their threat modeling!
- Some of the feedback I saw on slashdot about this kind of pointed out that there are a lot of ways to hammer Microsoft products that don’t require SimuLand, and there are plenty of tools that let you do that...Metasploit, sqlmap, Kali Linux, and I’ll also sort of put Cobalt Strike in that category, because even though it was not meant to be open source, the fact is that there are ways to get hold of it outside of buying it. Now, any ethical defender wouldn’t obtain it that way, we can presume. And there are of course tons of open source projects on the detection, monitoring, and prevention side of things as well, really too many to go into on this finite podcast.
- It’s far too soon to know how widely adopted SimuLand will be, and there are other ways to simulate attacks that don’t involve paying Microsoft a subscription fee. But there are advantages to having it packaged up this way, too. I certainly think that it’s a positive thing when vendors encourage the community to hammer on their products.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
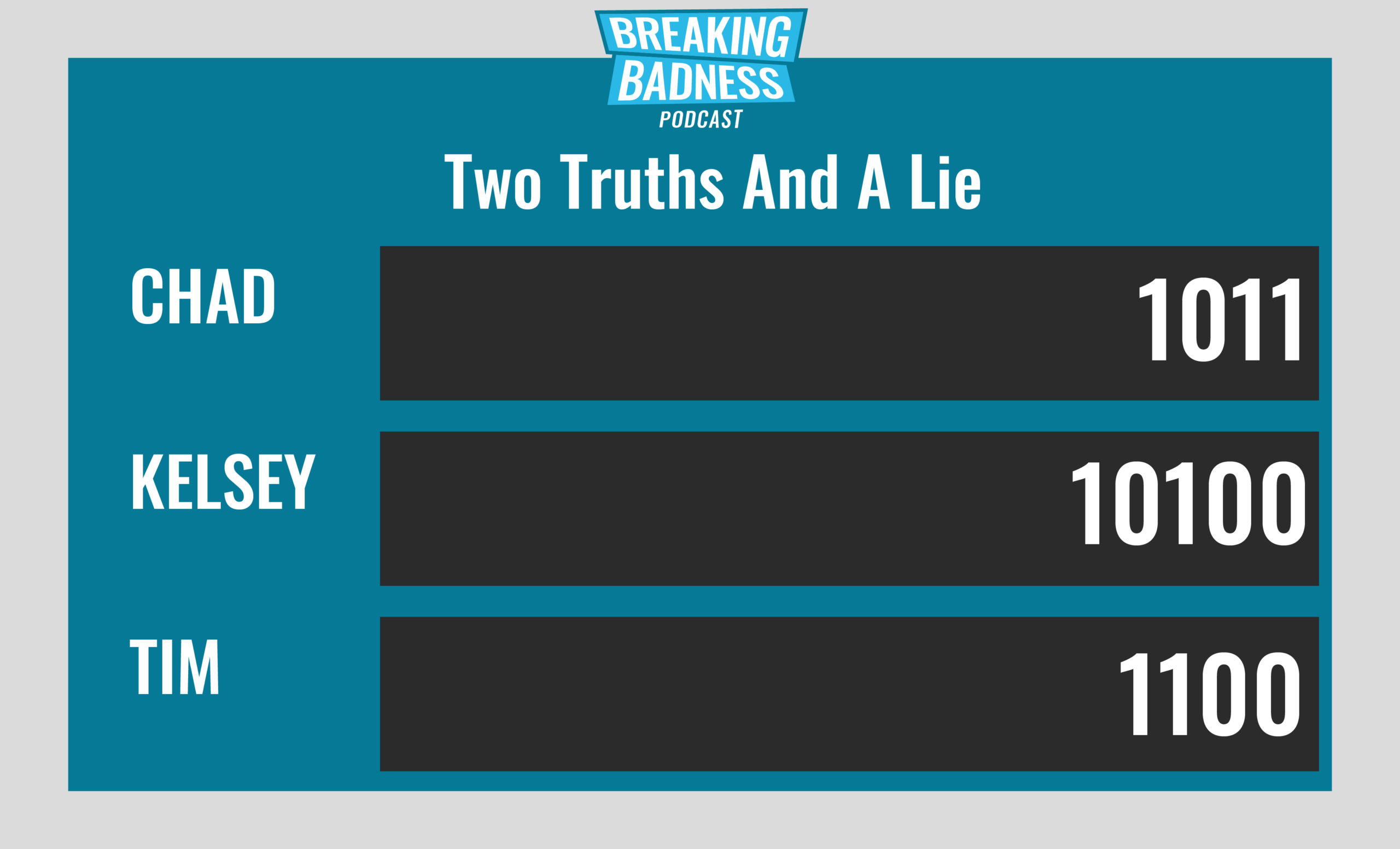
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Financial Corporation Pays Their Premium[Chad]: 6/10 Hoodies[Tim]: 6/10 Hoodies
The SimuLand of Opportunity[Chad]: 7/10 Goodies[Tim]: 6/10 Goodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

