Coming up this week on Breaking Badness. Today we discuss: Vulnerability HTM Hell, Nothing Botnet, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Vulnerability HTM Hell
- So four days ago Microsoft released information on an in the wild (ITW as the cool kids say) remote code execution vulnerability that affected MSHTML which is a browser rendering engine used in a number of Microsoft applications including Microsoft Office. Within this renderer are things called ActiveX controls and ActiveX is a now deprecated software framework, used mostly by Microsoft products, that allowed for basically more interaction with the system than the browser could provide, to simplify it. Anyways, this of course was used for a whole host of malicious reasons and was pulled from the most recent version of Microsoft’s new browser Edge. So what happened here is crafting a malicious document, that leverages a crafted ActiveX control, that renders in Microsoft’s older MSHTML browser rendering engine, an attacker gains full remote access. Now we’re seeing a ton of variations crop up on Twitter and public exploits proliferate all over GitHub.
- Microsoft Windows was impacted by this vulnerability. As more tweaks and variations come out I’m guessing more software will be affected, but I’ve only seen things working with Microsoft Office documents right now as well. However, given where Trident, what MSHTML is also called, is used across Microsoft systems I wouldn’t be surprised to see more novel ways of setting things in motion here.
- Folks from Mandiant, EXPMON, and MSTIC were all credited with the discovery. I’m not sure on the exact time frame of discovery, but I would guess it was shortly before the September 7 release since this was found in the wild.
- In order to protect your organization, disable all ActiveX controls. Realistically this should’ve happened years ago when Microsoft moved to Edge, but they don’t like to actually sunset anything. Look at XLM macros in Excel documents still being a pain for defenders to deal with out there.
Nothing Botnet
- It’s been a minute since we’ve talked about record-breaking DDoS attacks, hasn’t it? And this is sort of this interesting thing, too, where it seems like when you do hear about them, it’s only when the latest record has been broken. So this botnet, whose name is Latvian for “plague,” as I’m sure everyone already knew, is composed of tens of thousands of compromised devices. Now what’s sort of interesting here is what kinds of devices were recruited into this thing - it’s a little different from Mirai and others we’ve heard about in the past, where a lot of the bots were on pretty low-end routers and IOT devices and such. In this case, the net targets more sophisticated equipment - specifically, it looks as if it goes after Mikrotik gear. Mikrotik is a Latvian purveyor of networking equipment (which is favored, by the way, by a lot of geeks because it is good quality gear and highly configurable.
- News came out widely last week, but a company called QRator labs, which has been working with Yandex on this, first started catching wind of this new botnet back in June or so. But as the magnitude of this most recent attack started to really be understood, that was when a Russian-language media outfit called Vedomosti reported that sometime around what was our Labor Day weekend things were really starting to ramp up.
- In terms of how these attacks work, there’s actually a clue about how they work in the unit that’s used to measure them - requests per second or RPS. What the bots do is send their target a flood of requests that open a channel, but then don’t send any data through. So they aren’t sending malicious code, they’re just clogging up the pipes. The analogy I’ve used before is as if you’re having a party, but a huge line of door-to-door salesmen forms at your front porch, hundreds or thousands deep. All they do is knock at the door, and when you open it, they just stand there until you tell them to go away, which they do when asked. Your guests can still come to your party, but they have to share the line with all those salesmen, so it really slows things down. The “distributed” part just means that lots of different devices are participating in the denial of service, and any meaningful DoS these days is almost definitely going to be distributed, at least if it’s using one of the really common techniques for this.
- Besides the fact that it’s Mikrotik devices as I mentioned before, one of the things they’re noticing here is that all these Mikrotiks seem to be Ethernet (rather than WiFi) connected. That often, though not always, can suggest a larger, more powerful device. Also they noticed inter-bot communication over L2TP tunnels, which is a form of encrypted tunneling that a lot of consumer-grade devices do not support.
- Yandex is definitely feeling some pain. We got a description of this from the aforementioned Vedomosti in these technical terms: they’re having a hard time. And this isn’t surprising; DDoS mitigation is one of the tougher things to do in infosec, because all of this traffic is coming into your pipe from all sorts of different locations, you can’t block it fast enough, and even if you change to a different pipe, most of these connections are coming to a URL rather than hard-coded IP addresses, so they’re just going to keep coming at you on the new pipe. Ultimately these things do get quelled, but it can take hours or days.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
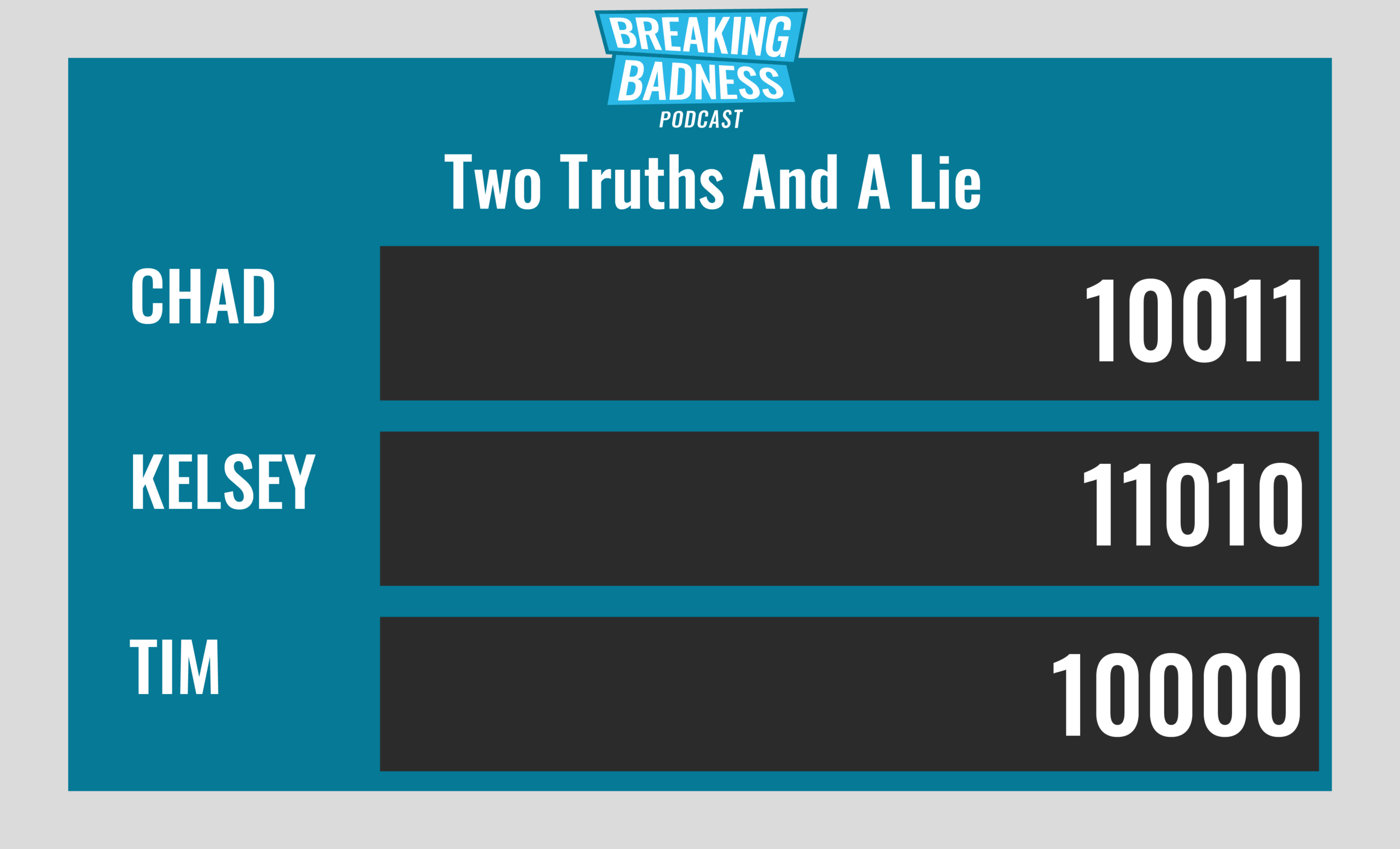
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Vulnerability HTM Hell[Chad]: 8/10 Hoodies[Tim]: 7.2/10 Hoodies
Nothing Botnet[Chad]: 7/10 Hoodies[Tim]: 6/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!


