Iris Investigate Features Blooming Like Spring Flowers!
Today, we are pleased to announce the latest of a set of enhancements to DomainTools Iris Investigate: Domain Tagging . But before we go into detail about Tagging, let’s set the stage. Over the last several weeks, we have released a series of new features in Iris Investigate designed to help our customers find more relevant information, and in more streamlined ways, than ever before. If you’ve used Iris Investigate in the last few weeks, you have probably already noticed the new Inspect view , the summary Risk and Age metrics in the Pivot Engine, the subdomain information in SSL Subject Alternative Names, the ability to download pDNS results, and the choice, when arriving into Iris Investigate, of whether to begin an investigation or to leave your query as a single ad-hoc lookup. To that list, we now add Domain Tagging. It’s been a busy few months for our Engineering team!
What do these new features offer?
- Domain Tagging: you can now add your own Tags to domain names. The Tags can be anything of your choosing (20 character max), and you can add as many Tags as you like to a domain. You can also add descriptive information to your Tag; examples could be a link to a threat actor report, a link to a work ticket, or a simple narrative description of what the Tag is about. Tags are shared at the group level, to facilitate collaboration with team members within your organization. You can also search or filter on Tags with the Iris Investigate and Iris Enrich APIs.
- New Iris Investigate “arrival” experience from the Search page, incorporating the Inspect view: when you initiate a search on a domain or IP address into Iris Investigate from the main search page (https://research.domaintools.com), you see a summary view that gives quick insights into the domain/IP; from this view, you can choose to start an investigation, or simply close out if you just needed a quick ad-hoc lookup.
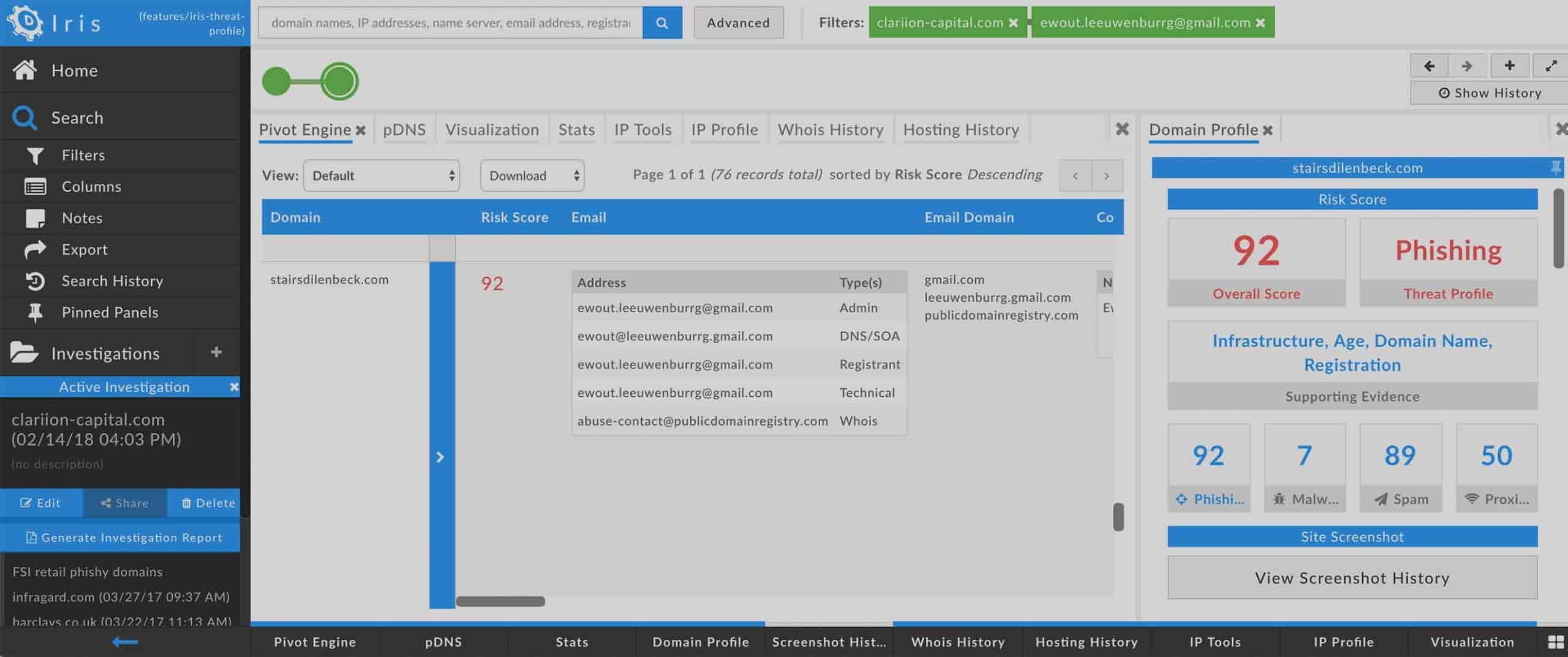
- Summary Domain Risk Score and domain age statistics Pivot Engine: when you have a multi-domain results set, you can now see the average Domain Risk Score and average age (in days) of the domains, right at the top of the Pivot Engine.
- If you’re a user of passive DNS (pDNS), you can now download the pDNS results to a .csv file for use in other tools, or for documentation of your research.
- The SSL Profile now includes subdomain support in the Subject Alternative Name section, which can help illustrate relevant infrastructure that would otherwise be difficult to find.
There are many ways to take advantage of these enhancements, so let’s just look at a couple of specific ones.
Domain Tagging
Let’s say you read an interesting threat intel report about an adversary group (we’ll call it “APT FINCH”) that you’d like to understand better. If it’s like many intel reports, it has a list of IOCs (Indicators of Compromise), including domain names associated with the malicious activity. You copy the list of domains (no need to remove the “defanging” brackets around the dots!) and paste them into Iris Investigate’s search box. Once you’ve run your search and have the results in the Pivot Engine, you can select any–or all–of the domains and add a Tag to them–in this case, “APT FINCH.” And since you can add a description to your Tag, you can paste a link to the APT FINCH intel report in the Tag Description. You’ll always be able to find these domains in the future by searching on the Tag you created. And, if you decide to start an internal work ticket related to (let’s say) blocking APT FINCH infrastructure, you could add another link in your Tag Description–this time to your work ticket. This helps you move more seamlessly between Iris Investigate and the other tools in your ecosystem.
Ad-Hoc Lookups and the Iris Investigate “Arrival” Experience
While Iris Investigate is a great way to conduct a deep investigation into adversary campaigns and infrastructure, sometimes you just need to get a quick look at a specific domain. With the new Inspect view, if you search on a domain from https://research.domaintools.com (using the “Search with Iris Investigate” default), you’ll be presented with a summary of all the key information about the domain, but Iris Investigate won’t create a new investigation unless you tell it to. That way, your ad-hoc lookups don’t clutter up your Investigations list. By the way, the Inspect view works on IP address searches as well. And it’s not just for when you arrive into Iris; you can invoke the Inspect view from Pivot Engine, Domain Profile, and IP Profile as well.
We hope you enjoy using these new features as much as we enjoyed building them! Everything we develop is born out of deep curiosity about, and respect for, the ways in which InfoSec professionals carry out their work. Let us know your thoughts on these features, or anything else that comes to mind!
To learn more about these new Iris Investigate enhancements, join DomainTools Director of Product Management, Tim Helming, on June 25th at 10AM PT/1PM ET for our live webinar.