What Does WhoIs Data have to do with Cybersecurity
When we launched our new homepage last year, a lot of people asked me “What does Whois data have to do with cybersecurity?” A lot, as it turns out. My answer then is the same as it is now: Whois data helps you understand who is behind nefarious domains and IPs, and helps you connect domains and IPs to each other and to their owners.
If you follow cybersecurity news, the Mandiant/FireEye exposé on an Iranian hacker group garnered a fair amount of attention this week. Additional insight was provided by the security heavyweights at Crowdstrike. It seems some pretty powerful threat intelligence folks have been tracking this group for months. What’s also obvious, however, is that both teams used Whois data extensively in their research. The Crowdstrike blog post, for example, imbeds a screenshot from DomainTools’ newly redesigned Whois History product in outing the keyvan.ajaxtm gmail address. In parallel, the FireEye report has a significant amount of detail, including Maltego transforms that help visualize the relationships that Whois and DNS data can surface. This is, essentially, what the DomainTools suite of Reverse products does: Connect actors and internet resources to each other.
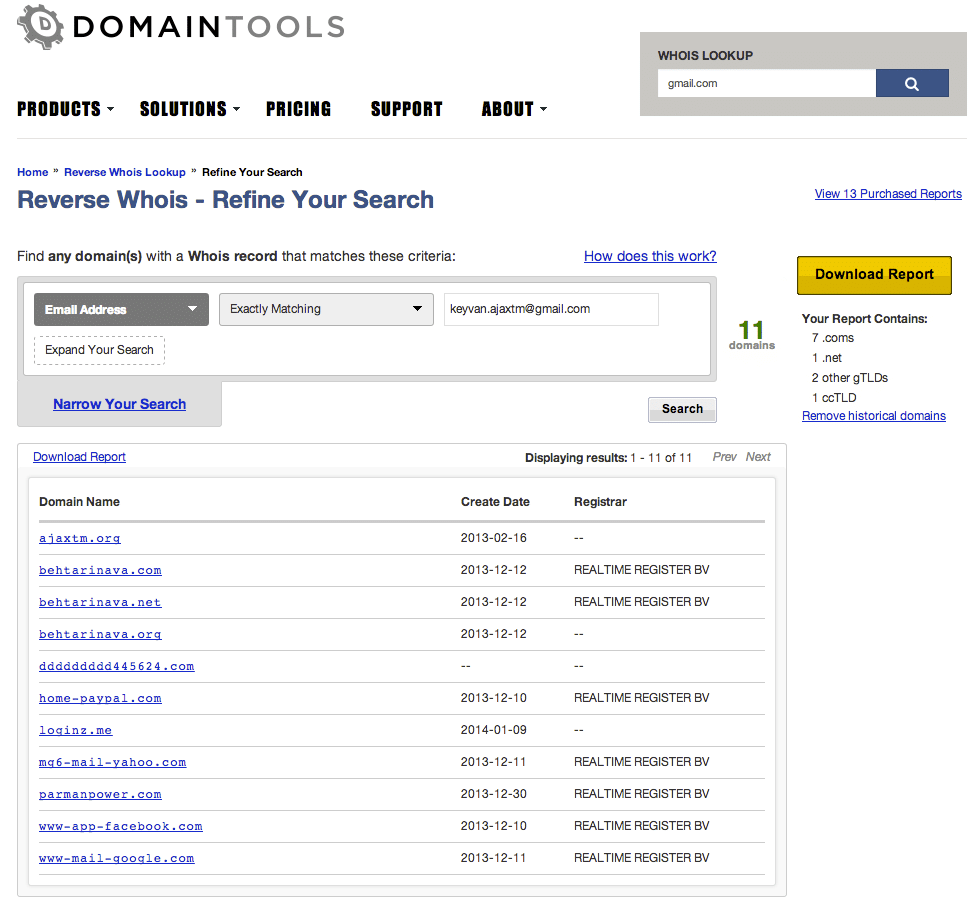
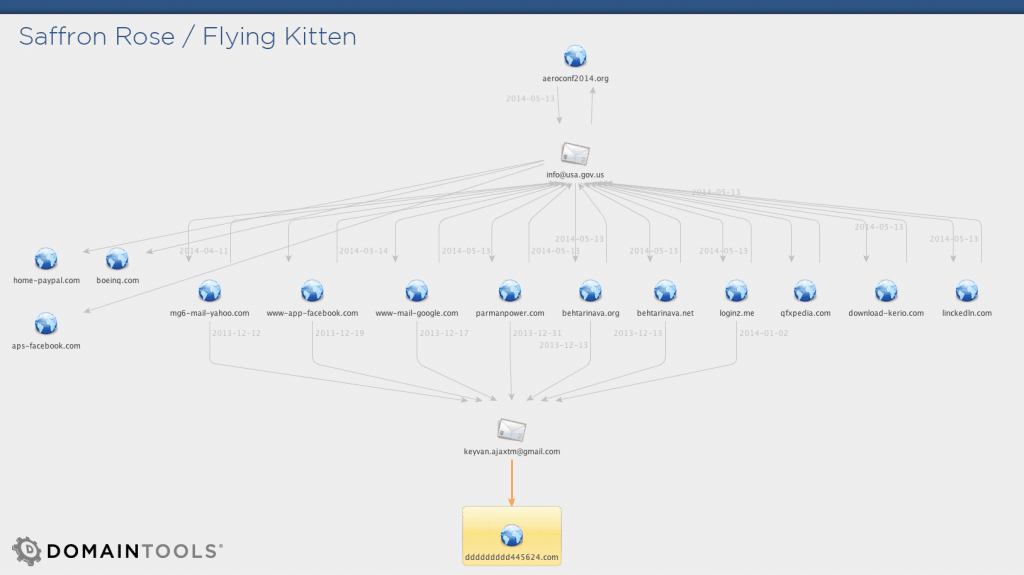
Below are two ways to visualize DomainTools data. The first is the standard output of our web-based Reverse Whois IRM product, for a search on the surfaced email address. Notice the brands being targeted by this group. Dropping our data into Maltego makes it even easier to notice a domain name that was not mentioned by either FireEye nor Crowdstrike: dddddddddd445624[.]com. This domain only briefly existed in DNS, in 2010. DomainTools captured one Whois record, which is available in our Whois History tool.
In security, you either have the data or you don’t. DomainTools knows about more domains in DNS than any other Whois provider, we have a much longer record history, and we capture more records more frequently than anyone. That is why we are a particularly useful partner to threat intelligence communities worldwide. A comprehensive search of our data sets will surface more leads for this investigation than anything, I would argue, than a specific forensic investigation of the malware exploits themselves. And we can help inform the output of those efforts as well, as detailed in the FireEye report.
Here is this example played out in steps
- Start with the phishing webpage: aeroconf2014[.]org
- Get the email address from Whois: info (at) usa[.]gov[.]us
- Reverse the email into a list of current AND historic domain names
- Use Whois history on these domains to surface a new and interesting email: keyvan[.]ajaxtm (at) gmail[.] com
- Reverse this new email into a list of curent and historic domain names
- Do a Whois lookup on the short-lived domain: dddddddddd445624[.]com
- Pull the registrant name from this record: Ali Alavi
- Reverse this registrant name into a list of current and historic domains
- Investigate a few of the associated domains, say for example: youthpartyofiran[.]com
- Go deep into Whois history on this domain and pull out a new associated email: ali_alavi97 (at) yahoo[.]com
- And so on.
Look at the number of potential investigative leads surfaced in just this one thread. There are many more if you take the time to interrogate Whois and DNS data with powerful tools.
Internet activity leaves a trail of evidence, in the form of domain names and IP addresses. Signals like email addresses and websites all back out to hostnames, domains and IPs. To steal a line from Dan Hubbard at OpenDNS, these ‘threatcrumbs’ are the foundation of threat investigation and, ultimately, prevention. Why not avail yourself of the world’s best domain name and IP data?
Later this year DomainTools is going to release an incredibly powerful new tool that puts all of our data sets, fully parsed, into a unified searchable database. It will make all of this research lightning fast, with an overlay of proper usability features such as sorting, filtering and saved searches. If you are a customer of DomainTools and would like to participate in the beta trial for this product, please contact us at [email protected].