Navigating Cybersecurity Rough Seas: Choosing Objective Observations vs Narrative Fallacies
We have reached unprecedented complexity of our cyber defence systems, and we have very little understanding how all of this works.
We add even more complexity to mitigate the vulnerability we discover. We justify that by narratives about how the adversary would fall in our trap, if we only had one. And that is a fallacy because the objective of the adversary is to evade it.
An opportunistic adversary would be happy to open any door, and motivated ones would want to open your door, and they will, with certainty, as demonstrated by the empirical evidence. Against the former, a “hygiene” approach would likely work, however the latter adversaries could create a vulnerability in your environment and the traditional compliance-based approach will likely fail.
Adding the complexity, e.g., so called “layered defences”, “next gen” of this and that, or, recently, logically inconsistent principle “never trust, always verify”, to “make it harder” does not seem make any measurable difference, especially, against the motivated actors.
The matter becomes even worse, as we cannot devise a test to demonstrate security positive. That is, all those “new things” cannot be validated in principle. That leads to an inability for us to self-correct and provides a safe haven for the narrative fallacies and the storytellers.
I have been thinking deeply about the state of security today. If we cannot prove security positive, is it possible the opposite is true: the fallibility of a security system is its’ fundamental property? And if that is true, then we are doing the wrong thing!
Instead of trying to make a system “secure”, we need to learn how to “run insecure systems in hostile environment safely.” New approaches are required that will quickly detect, respond fast, and swiftly recover from the compromise – resilience not robustness shall be our long-term strategy.
How can we do that?
I will now share an analogy of sailing in the high seas – if that is not hostile enough, what is? And as we know from the history, people crossed the high seas and survived hurricanes on rather primitive vessels (Niña), and sunk in the quiet on their first journey on a state-of-the-art ship at the time (Titanic).


What, among other equal things, determined their destiny?
Obviously, not superior technology nor their size or sophistication, but, instead, the abilities and skills of their crews equipped with the facts about the environment they were in – the objective observations that they used and interpreted to “run insecure system in hostile environment safely”.
What facts would we need to collect and interpret to learn about the hostility of the interconnected environment (i.e. the Internet) we and our systems are in?
There is lots of useful data, but I will touch on a few types here. There are fundamental protocols that fuel the Internet, DNS and BGP. Early changes in observable data delivered by these protocols can be strong indicators of badness development that give defenders the window of opportunity to get ahead of the malicious actors.
Furthermore, it is also very important to keep the historical records of the events to ensure the preserved observations can be used as evidence of malicious activities. It is vital for incident response and investigative and forensic purposes to pursue the perpetrators.
NOTE: Historical observations such as e.g., Passive DNS, can answer questions that regular or conventional methods cannot answer in principle.
How can we help?
Why us?
We understand the threat landscape inside out – and we are pioneers in our field, perhaps even the first in the industry. We have the Top industry skills of like-minded people in our Team, who are on a mission to make the internet a safer place for everyone.
Where and how can we find accurate historical DNS records of the events?
Here at Farsight Security, we collect and rigorously maintain since 2010 over 130Bn accurate DNS observations. We collect those PII-free by design DNS requests and responses from all across the Globe – the accurate and objective observations of the events, DNS questions and answers, that have actually occurred. These are the facts, not speculations, about everything we observed happening – both, good and bad.
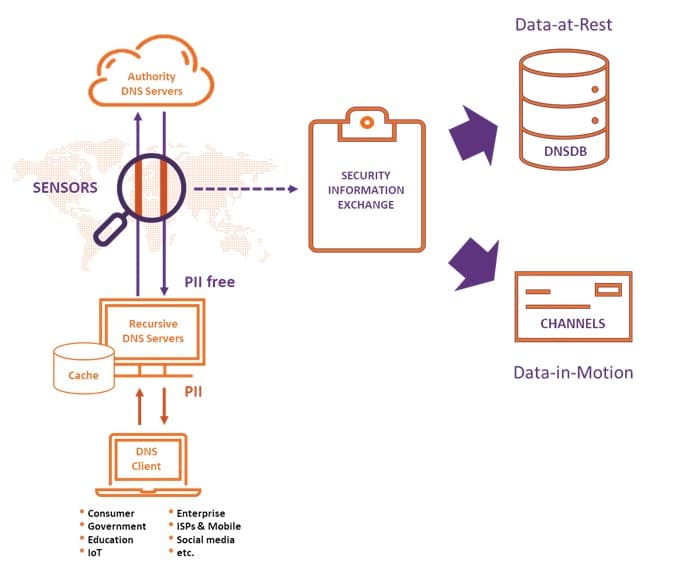
So what?
Whilst many still rely on judgment and reputation-based solutions, organizations are increasingly turning to the raw facts. In the fast-changing world, opinions become obsolete very quickly whereas facts — Global DNS resolutions — remain unchanged. We developed several dozen use cases on how to use Passive DNS data to defend businesses against even the most formidable actors.
Those use cases are to assist you and guide your everyday work life in many different disciplines, from cyber security/defence to anti-fraud, etc., on how to use the Passive DNS observations and find relevant facts of malicious activities.
These facts can serve as evidence that can not only can help you avoid any speculations and narrative fallacies, but also make informed decisions and build a case that can stand in the Court of Law.
Boris Taratine is a Principal Architect for Farsight Security, Inc.




