Paul’s Security Weekly #598 on DomainTools Iris Investigate
Enjoy a guest blog written by Paul Asadoorian detailing Paul’s Security Weekly Episode #598
Malicious or Not?
The above question runs through the brains of SOC analysts across the world multiple times per day. When you are analyzing security events looking for the “bad” things, you often come across a domain that requires investigation. Domains are an integral part of a security investigation as a whole as they can appear in malware samples, malicious JavaScript, several different types of logs, and of course directly from your network (via a SPAN port) or directly from your DNS servers if you are logging all queries. If you are not analyzing all of your DNS queries, you should be as a domain can be a reliable indicator of malicious activity. While there are several tools and techniques available to gather information about a domain, DomainTools has consolidated this information, making it easy to pivot and investigate domains using Iris Investigate. I had a chance to use Iris to investigate some domains, and was very impressed. My methodology from start to finish is outlined below.
Collecting Domain Data
My setup is fairly traditional as I use a network SPAN port along with The Security Onion to collect data about my network for security analysis. I used a Cisco switch with the following commands to setup the SPAN port:
- Monitor session 1 source vlan 172
- Monitor session 1 destination interface Gi0/39 encapsulation replicate
By default, the first command will monitor traffic in both directions on the specified VLAN. We then send the monitor session traffic to port Gi0/39, using the encapsulation method as the source interface, giving us BPDU and Layer 2 traffic as well (Further reading: https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3750/software/release/12-2_52_se/configuration/guide/3750scg/swspan.html)
I setup the Security Onion on an Ubuntu server. Documentation for this setup can be found over at the Security Onion Website.
Additional Modules – Baby Domains
I installed the DomainStats add-on, written by Mark Bagget and implemented in Docker by Justin Henderson, Security Onion, using DomainStats, will report on domain age, listing domains that are younger than 60 days. New domains can be suspect as C2 channels will often register new domains for communication.
https://github.com/SMAPPER/docker_domain_stats
https://github.com/Security-Onion-Solutions/security-onion/wiki/DomainStats

A list of baby domains in the Security Onion Kibana interface
Parsing Query Logs
By default Bro, as part of the Security Onion, will begin to log all of the DNS queries observed on the network. It stores them in /nsm/bro/logs/current (and archives older logs into separate directories by date). I use the following command to save all of the queried domains to a file:
$ zcat dns.* | jq .query | uniq -c | sort -n | uniq | egrep -v '(.com|.net|.org|.edu)' > ~/domain.list
The “jq query” command is a newer addition to the Security Onion and will parse the JSON output and return just the domain names in the logs. Next we use basic Bash commands to get a unique list and remove common top-level domains. This was an approach I used to pair down the list into the domains that may be more interesting. I then searched through the results for specific top-level domains. Using the following commands I reviewed the domains from China and Russia as I thought that might be a good start:
$ egrep -v '(in-addr.|psw.io|.local|.io)' domain.list | grep ".ru"
$ egrep -v '(in-addr.|psw.io|.local|.io)' domain.list | grep ".cn"
As it turns out, one of the domains from Russia was identified by DomainTools Iris Investigate as being bad, earning a Domain Risk Score of 100:
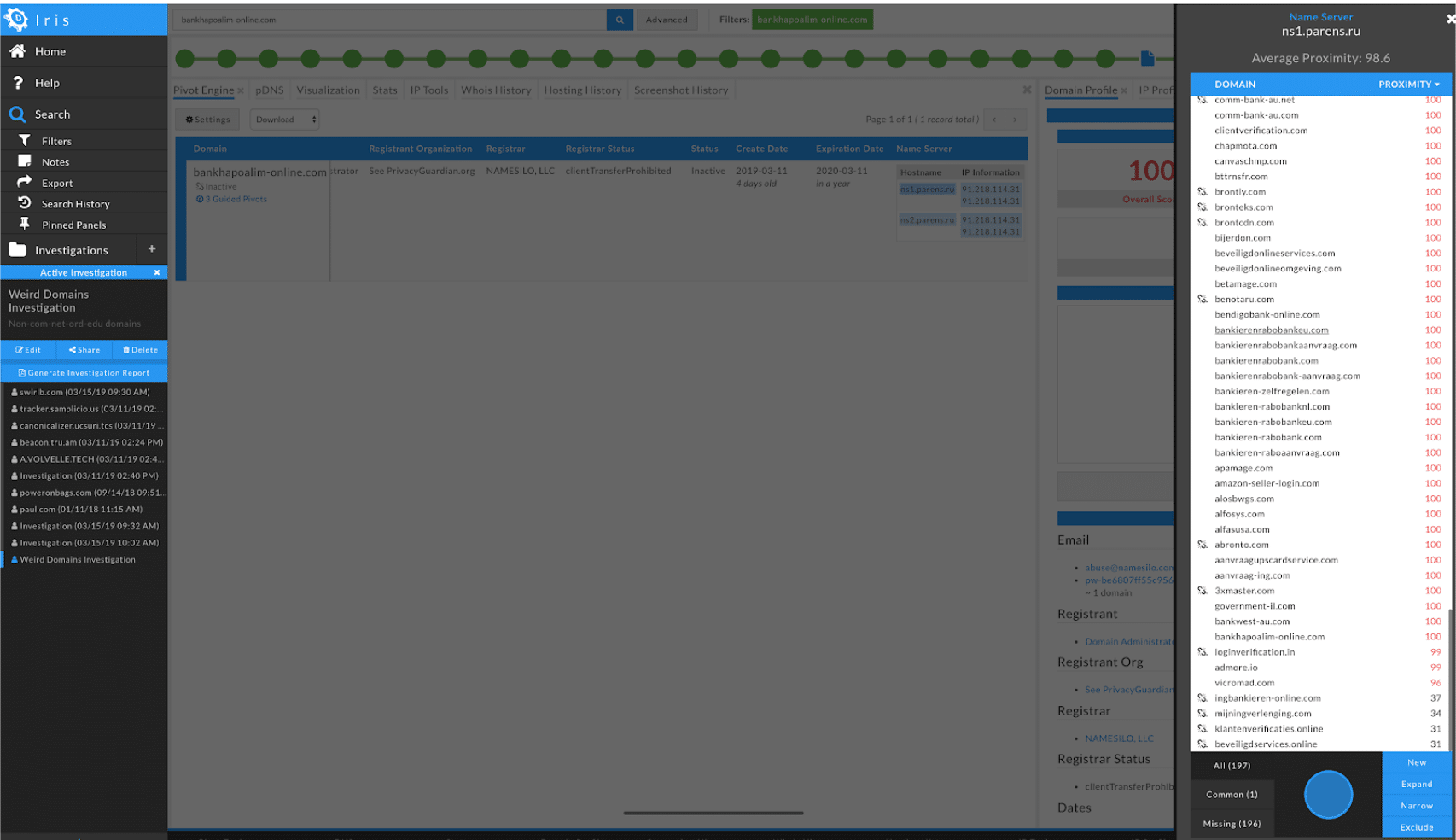
You can also see the list of other domains that are associated with ns.parens.ru. While most also earn a score of 100 (meaning the domain appears on industry lists of known-malicious domains), there is a shorter list of domains that have a lower score. This is because the DomainTools Risk Score predicts the risk level and likely threats from a domain that has not been observed in malicious activities, by analyzing various properties of the domain that exist as soon as the domain is registered. Domains scored above 70 are more likely be weaponized. It should also be noted that you can paste in multiple domains at once, consolidating them into one investigation, or by expanding your investigation in order to roll in domains you find throughout your investigation.
Conclusion
DomainTools Iris Investigate is a fantastic addition to your analysis toolset, providing insights into domains that are malicious, and even cooler those domains that will be malicious in the future! To see the full technical segment and Iris Investigate demo check out my segment on Paul’s Security Weekly visit: https://www.youtube.com/watch?v=hWf5mqr64ZU&w=560&h=315. While I used Iris Investigate on my own, there are some great collaborative features as you can add notes to your investigation and share with others on your team.





